v3.4 January 26, 2025
Version 3.4, a major release, includes:
Prerequisites
Before you can use the features and enhancements described below, you must update the relevant Agent on your device. macOS/Windows Agents 3.4 are generally available around a week after the release.
New features
This section describes the new features that we are releasing with version 3.4.
1 - Coro console
The following features have been added to the Coro console:
1.1 - Multi-language support
The Coro console is now available in three languages:
- English (US and UK)
- Spanish (Spain)
- Italian (Italy)
When creating or editing a workspace, you can set the language at the workspace level. Additionally, each admin user can set a language for their own console.
For more information, see:
2 - Email Security
The following features have been added to the Email Security module:
2.1 - Adding the Inbound Gateway to user information
Users protected by the Coro Inbound Gateway are now shown as such on the Protected Users page. A filter option under Protected Apps allows quick identification.
For more information, see Adding users and user groups for protection.
2.2 - Inbound Gateway monitoring
Coro continually monitors and verifies the configuration of your Inbound Gateway service, and alerts admin users through email and within the Coro console when problems are identified.
For more information, see Configuring the Inbound Gateway.
2.3 - Email Security threat warning priority
Where multiple threats are detected within an email, Coro prioritizes setting the warning message/banner to represent the most severe threat encountered.
For more information, see Scanning emails for threats.
2.4 - Exclude emails by subject line keywords
Admin users can instruct Coro to ignore emails containing specific keywords in the subject line.
For more information, see Excluding emails from threat scans.
2.5 - Security Awareness Training allowlists
Organizations can utilize Security Awareness (SA) providers to help train employees to recognize phishing attempts and malicious content delivered via email. SA providers send simulated email attacks to test employee awareness and measure response rates to deceptive messages, educating employees on what to look for and how to flag or avoid potential threats.
Coro allows you to define an allowlist for emails originating from SA providers so that these emails do not trigger Coro’s detection mechanisms.
For more information, see Excluding emails from threat scans.
2.6 - Spam sensitivity tuning
Coro enables you to set the sensitivity level (high, medium, or low) for spam detection within your protected users' emails. This can help alleviate scenarios where your users are seeing a higher-than-expected number of false positives, or conversely, if Coro is limiting detection to only the worst offenders.
For more information, see Setting sensitivity for spam and phishing detection.
3 - EDR
The following features have been added to the EDR module:
3.1 - Process graphs
The process graph visualizes the process tree for an EDR ticket, highlighting malicious and legitimate processes identified by Coro. Admin users can explore parent and child processes, analyze their relationships, and view detailed information for each process node. This helps assess processes to identify potential threats and take action.
For more information, see Process graph.
4 - Connectors
The following features have been added to the Connectors functionality:
4.1 - API - workspace search
You can now use the /workspaces/search endpoint to search for all child workspaces of a specific channel workspace.
For more information, see the Coro developer portal.
5 - Cloud security
The following features have been added to the Cloud Security module:
5.1 - Details and status of connected cloud applications
The Cloud Applications page now shows the number of protected users, highlighting active and inactive users, the number of connected third-party applications, the connection status of the cloud application, and whether the connection is secured.
For Microsoft 365 and Google Workspace, if the connection is not secure admin users can select the Connected (not secure) status, which displays a dialog. The dialog shows the latest heartbeat, which is when Coro last made contact with the cloud application, and the permissions for the cloud application. A Grant permissions option lets you grant full permissions for Coro on the cloud application.
For more information, see:
- Setting permissions for your cloud applications
- Connecting and disconnecting your Google Workspace app
- Connecting and disconnecting your Microsoft 365 app
5.2 - Inactive user ticket and custom setting
note
The inactive user ticket type has been deprecated.
Coro now generates Inactive user tickets, allowing admin users to identify and manage inactive users.
A new Settings tab in the Cloud Security module enables admin users to specify the number of days that a user can remain inactive before Coro raises a ticket.
note
The inactive user setting defines the period of user inactivity required before the user's status changes from Active to Inactive. The setting has not been deprecated.
5.3 - IP metadata in tickets
Mass data deletion and mass data download tickets now show IP address metadata. If the IP address is suspected of being a severe risk, it appears in red. If it is suspected of being a moderate risk, it appears in yellow.
For more information, see Mass event tickets.
5.4 - Protected users 'joined via' information
The Protected Users page now indicates how a user was added to Coro protection and the applications to which the user is connected.
For more information, see Adding users and user groups for protection.
5.5 - Third-party applications
The Third-party applications tab in the Cloud Security module provides visibility and control over all third-party applications connected to Microsoft 365 and Google Workspace protected by Coro.
Important
With the introduction of this feature, Coro requires additional new permissions to be granted for exising connections to Microsoft 365 or Google Workspace cloud applications in order to view and perform access operations on connected third-party applications. Affected customers can resolve this from the Cloud Applications page. For any connected cloud applications that show as Connected (not secure), select the status link and confirm the missing permissions in the subsequent dialog. For details, see Introducing cloud security.
Coro assures affected customers that your existing cloud protection is unaffected and the security and monitoring of your users' activity remains high.
For more information, see Third-party applications.
6 - Network
The following features have been added to the Network module:
6.1 - ZTNA
The Network module now offers zero trust network access (ZTNA). ZTNA delivers granular, identity-based access control, ensuring that only authorized users or devices can access specific resources.
For more information, see ZTNA.
6.2 - Endpoint Protection app
The Coro Endpoint Protection app is now available on iOS and Android devices. It supports VPN, ZTNA, and DNS filtering. The app is available in three languages: English (US), Spanish (Spain), and Italian (Italy).
For more information, see Activating the mobile app.
6.3 - DNS filtering
Devices not using VPN or ZTNA can now receive DNS filtering.
For more information, see SWG.
7 - MDM
The following features have been added to the MDM module:
7.1 - Passcode policy support for iOS and iPadOS devices
Coro MDM now includes setting a passcode policy for iOS and iPadOS devices. Policy settings include:
- Enforcing passcode strength rules.
- Setting the maximum number of failed attempts before a device wipe occurs.
- Setting the maximum inactivity timeout period, after which the device screen is locked.
- Setting the maximum passcode age, after which a new passcode must be set.
In the console, Coro also allows remote clearing of a passcode from an iOS/iPadOS device.
For more information, see:
Enhancements
Version 3.4 introduces the following additional changes:
1 - Coro console improvements
The following enhancements have been added to the Coro console:
1.1 - Coro console UI
The console now has an improved and redesigned user interface. The toolbar has been moved from the top of the page to the side, and the Devices, Protected Users, and Ticket Log icons have been moved under a new Lists icon.
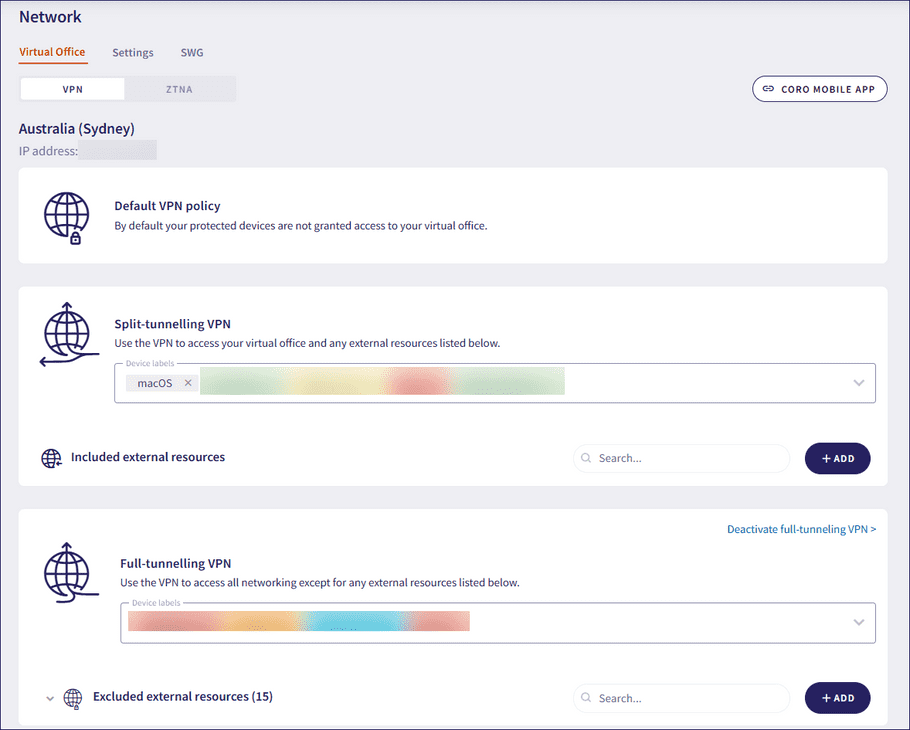
1.2 - Virtual office UI
The virtual office section of the Network module now has an improved and redesigned user interface. The VPN options have been named split-tunneling VPN and full-tunneling VPN, and the include/exclude lists have been separated. Additionally, a new CORO MOBILE APP button at the top of the page contains links to download the Coro Mobile Protection App for iOS and Android devices.
1.3 - Workspace moved to Trial state
Activating the Network module is now an onboarding event that moves a workspace from New to Trial.
1.4 - Pagination
You can now navigate directly to the first and last pages wherever pagination is available.
2 - Endpoint Security enhancements
The following enhancements have been added to the Endpoint Security module:
2.1 - Renamed 'Tamper protection' to 'Allow agent uninstallation'
Allow agent uninstallation enables admin users to uninstall the Coro Agent while maintaining Coro's tamper protection.
2.2 - Added an 'Online' option to the Groups filter on the Devices page.
The Groups filter now has an Online option, enabling targeted filtering of devices by their status.
2.3 - Removed 'Enhanced EDR block mode' from NGAV settings
Coro has deprecated Enhanced EDR block mode. During deployment, Coro registers as the primary security product in Windows Security Center (WSC), and replaces Windows Defender. No additional configuration is required.
2.4 - Device posture text improvements and tooltips
The following text improvements and tooltips have been made to Device Posture settings:
- Added tooltips for the Password must meet complexity option in Remote Password & Session Locking and the Allow connection to specific networks option in Wi-Fi Connection device posture policies.
- Updated Wi-Fi Connection policy text: replaced Allow connection to all encrypted networks with Deny connection to all unencrypted networks .
Fixed issues
- Resolved an issue where devices from archived workspaces could not be uninstalled. Tamper protection is now automatically disabled when workspaces are archived, allowing the Coro Agent to be uninstalled from devices.
- Fixed a crash during initial and on-demand malware scans on macOS devices caused by stack size limitations in the Bitdefender SDK. Updated scanning algorithms ensure stability during scans.
- Addressed an issue where file approvals or malware scan exclusions for legitimate tools detected as false positives did not work, resulting in repeated alerts.
- Resolved a problem where enabling Secure Web Gateway (SWG) and selecting specific categories caused unrelated websites, such as YouTube, to be blocked despite not being part of the selected categories.
Agent updates
This section describes additional Agent updates released with version 3.4:
Prerequisites
The relevant Agent must be updated on your device before changes take effect. The features described will not function until the updated macOS and Windows Agents are installed. Coro commences the roll-out of Agent updates after the release.
1 - macOS Agent 3.4
macOS Agent 3.4 includes the following:
1.1 - Multi-language support
The Coro Agent UI now supports the following three languages:
- English
- Spanish (Spain)
- Italian (Italy)
1.2 - Bug fixes
General bug fixes were made for this release.
2 - Windows Agent 3.4
Windows Agent 3.4 includes the following:
2.1 - Multi-language support
The Coro Agent UI now supports the following three languages:
- English
- Spanish (Spain)
- Italian (Italy)
2.2 - Enhanced malware detection for persistence-based threats
The Coro Agent now monitors Windows devices to detect persistence-based malware, such as scheduled tasks and registry modifications that might execute malware. This monitoring examines critical areas, including startup folders and registry entries, to ensure no malicious tools or processes execute.
2.3 - Bug fixes
General bug fixes were made for this release.