v1.9
Coro version 1.9 provides new features, enhancements, and fixes:
New features
This section describes the new features that we're releasing with version 1.9.
Data governance logic updated
We have updated the way our logic and code run, which is designed to significantly improve the quality of protection, and overall performance.
NPI & data governance
In support of the GLBA regulations, Coro now supports data governance and data loss protection for sensitive data classified as nonpublic personal information (NPI).
Configuration
Administrators with permissions to do so can manage NPI configuration, and related granular administrator permissions configurations from the Coro Console in the Control Panel.
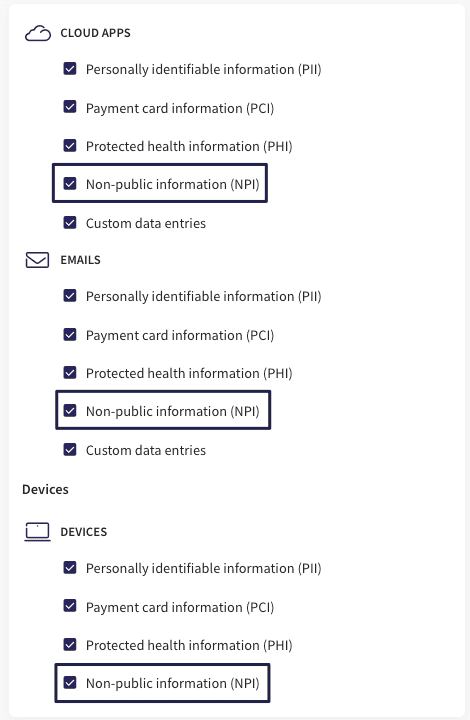
By default, Coro Console is configured to monitor cloud apps, emails and devices for NPI from the Monitoring tab in the Control Panel:
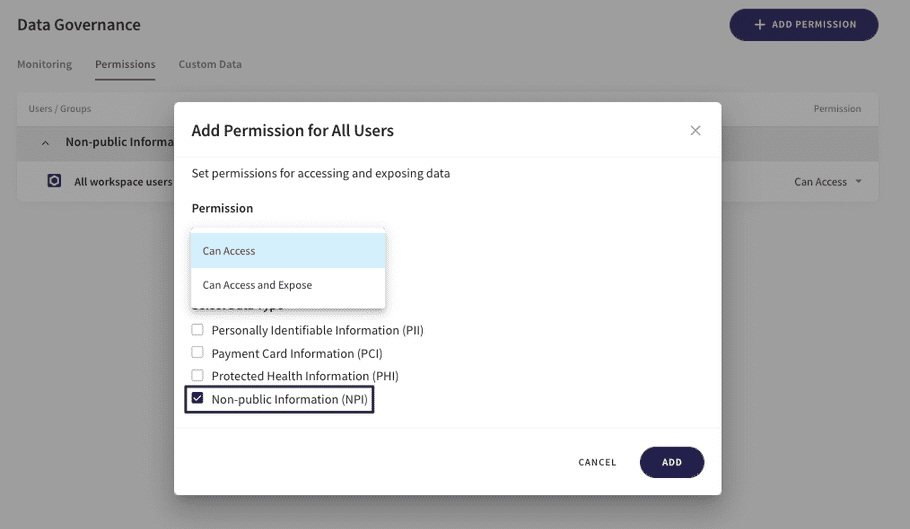
Administrator permissions can be configured granularly, by user groups, specific users or domains, or for all users, from the Permissions tab:
Actionboard
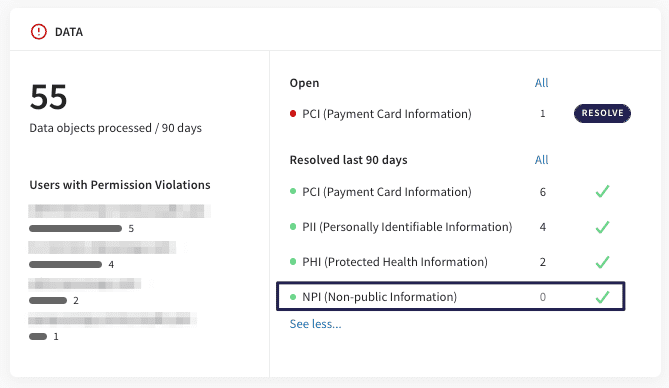
When configured, all NPI tickets created based on email and cloud app scans now appear in the Data widget on the Actionboard.
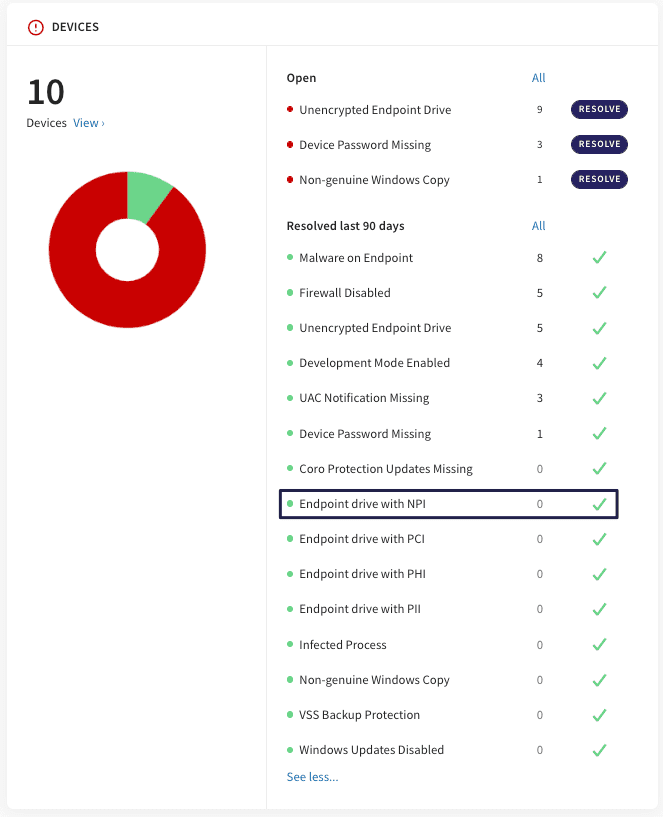
When configured, all NPI tickets created based on device scans now appear in the Devices widget on the Actionboard:
Devices: endpoint management
Coro Console and the Coro endpoint agent support data governance and data loss protection from Windows endpoint devices.
Note: the agent is in beta status and will be upgraded to Stable approximately 1 week following the initial release of v1.9. As indicated in v1.8, beta and stable versions can be accessed from the Coro Console at Control Panel > Endpoint Devices > Agent Deployment.
Note: In order to enable scanning of sensitive data inside images on endpoint devices, first install the OCR software Tesseract on Windows endpoints or macOS endpoints. You should install Tesseract prior to installing the agent, or alternatively reboot the device once you've installed both.
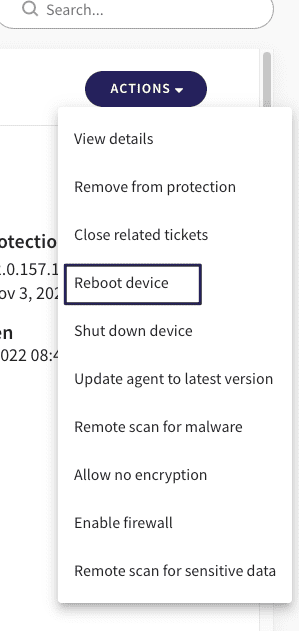
From the Coro Console, administrators can run a scan remotely on single or multiple devices to discover all sensitive data issues. From the Devices section, navigate to the relevant device, select Actions and choose Remote scan for sensitive data:
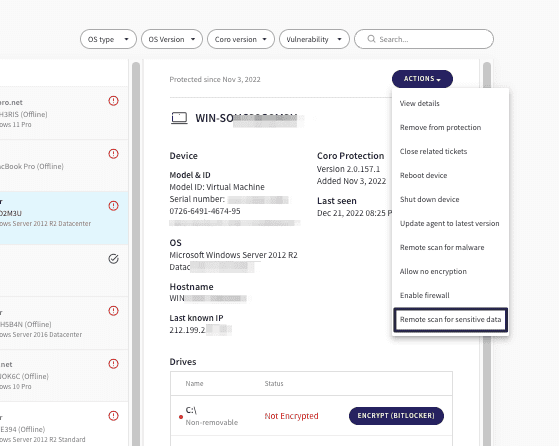
Tickets and the Ticket log
When configured, all NPI-related tickets are created according to the logic for data violations, which attempts to find the balance between the need to:
- detect and log everything for audit that might constitute a privacy/compliance breach
- primarily focus on particularly problematic private information exposures.
Accordingly, data governance tickets are classified as follows:
- detections that, according to the best practices of data governance regulations (GDPR, HIPAA, SOC2, etc.), require attention of the data compliance officers - tickets are classified as suggested for review (G2), with a review time window of two weeks
- all other tickets are classified as G3, and are automatically closed by the system
Classifications are described in detail here.
Each NPI ticket contains a complete list of all related events and their details, enabling the operator to understand why the ticket was created and where the issue is within the network; this set of details is uniquely organized depending on the origin of the ticket.
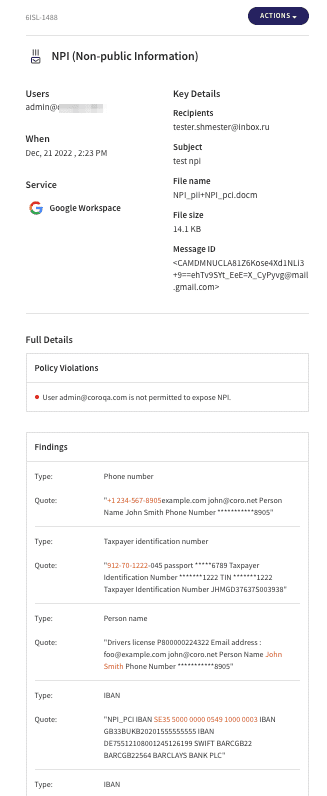
View tickets related to emails and cloud apps from the Ticket log using the filter for Data. These tickets appear similar to the following:
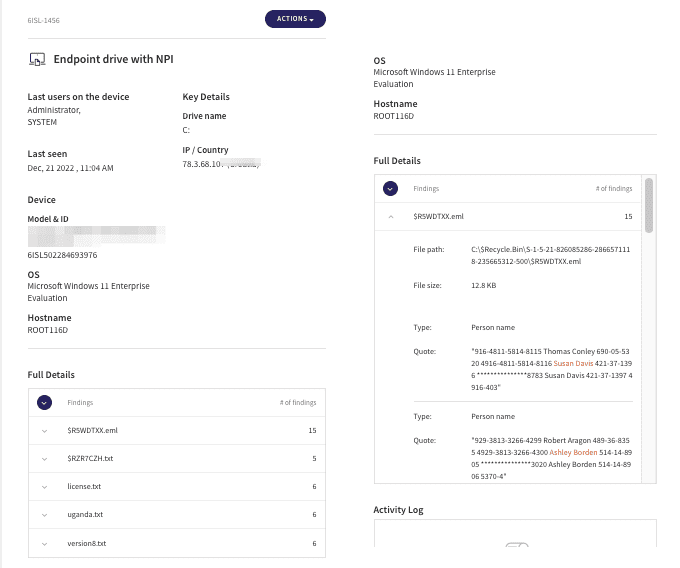
View tickets related to endpoints from the Ticket log using the filter for Devices. Tickets created for endpoints include:
- Hostname
- Relevant drive
- File name, path and size
Notifications
All administrators of the Coro Console can configure notifications for NPI from the avatar menu by selecting My Account > Notifications:
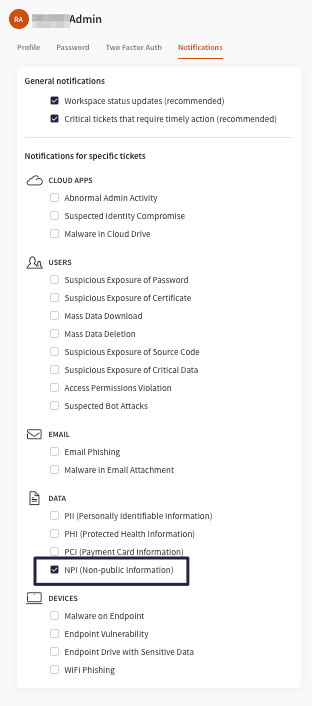
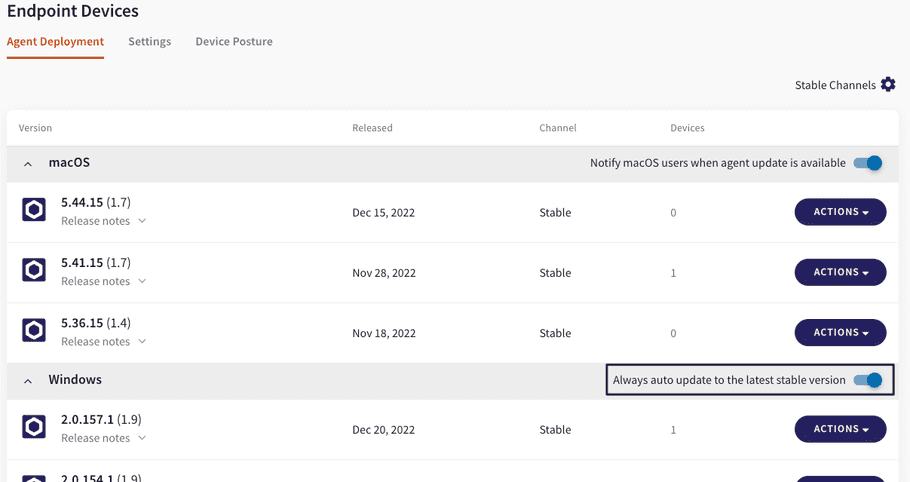
Automatic silent agent update
We are gradually updating agent updates in order to enable administrators to configure automatic silent updates remotely from the Coro Console by navigating to the Control Panel > Endpoint Devices > Agent Deployment.
Note: changes in this version apply only to Windows endpoints.
The "notify" toggle has been updated to "Always auto update to the latest stable version. This is the default for Windows endpoints. When necessary, the end user receives notification that they must restart their device. Users can opt to reboot immediately, or to delay the reboot by one hour.
Additionally, from the console in the Devices page:
- a notification appears when the agent is being updated
- administrators can force the reboot remotely for single and multiple devices
Enhancements
Following are enhancements to existing features that we’re releasing with version 1.9:
- Remote scan , which enables scanning devices remotely for malware and additional security vulnerabilities, has been renamed to Remote scan for malware .
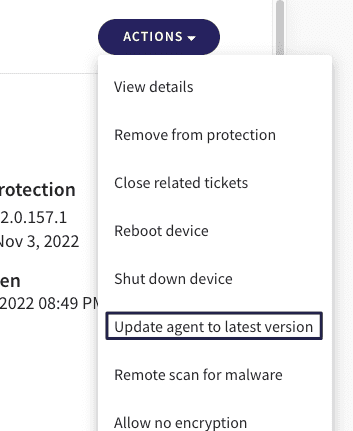
- Administrators can remotely update the agent manually from the Devices page:
- Since quarantined files can cause no harm, the ability to delete quarantined files was removed from the Coro Console . This should improve usability.
- Remote encryption from the Coro console for macOS devices is now available.

- Windows and macOS agents have been upgraded to the latest antivirus version available.
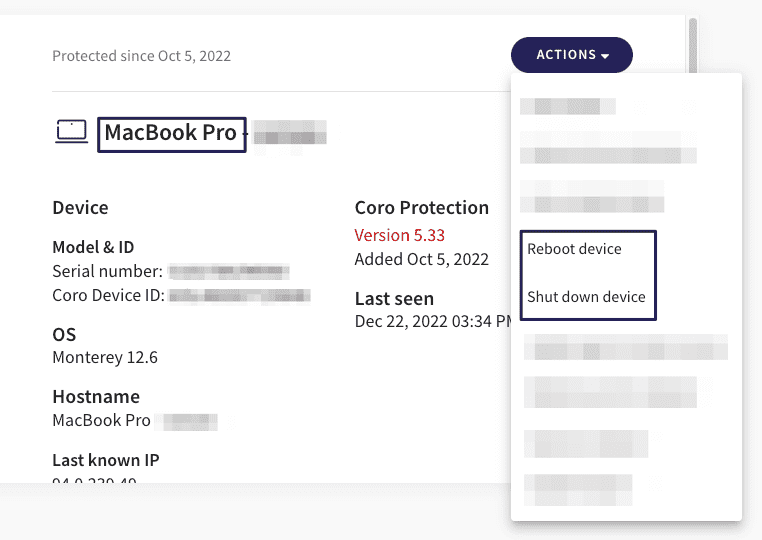
- Remote shutdown and reboot device actions are available from the Coro Console for macOS devices.
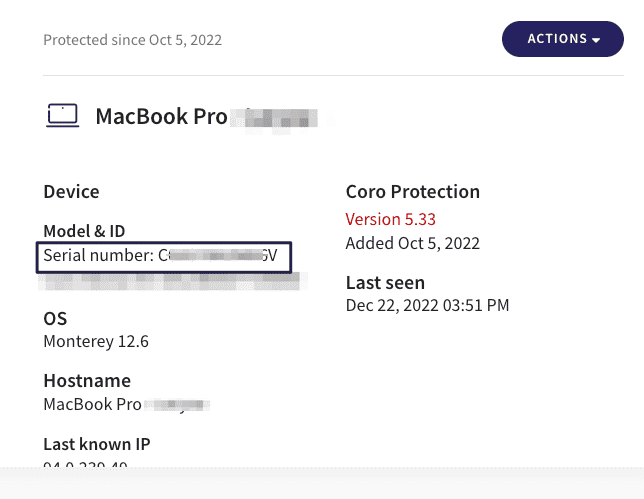
- Serial number for macOS devices is now displayed in the Coro Console on the Devices page:
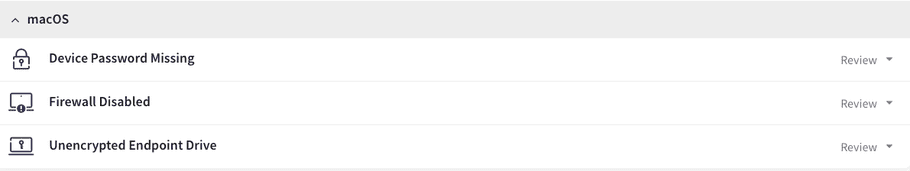
- Both manual and automatic remediation are now available for the firewall vulnerability on macOS:
Fixed issues
- Volume Shadow Copy Service (VSS) enables backup applications to safely back up files. With VSS protection, Coro enforces backup snapshot creation and does not allow any processes to remove backups that were created by Coro. Other backup applications on endpoint devices now run and are no longer blocked.
- Users can now change the size of their view and continue to enjoy a clear interface experience from the Devices page.
- From email tickets, when admins try to add a sender that is a user in their organization to the blocklist, a message appears that the action is not possible for the specified user.
- Email notifications appear clearly now, regardless of the length of the message ID.
Additional updates
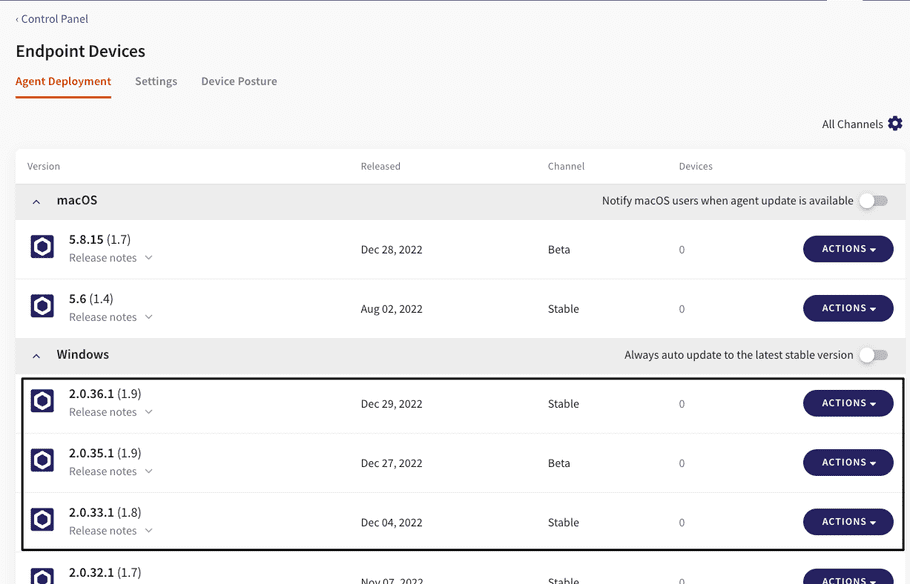
Remote scan for malware in the Action menu from the Devices page, originally available in the release notes for v1.5, was redesigned and is now available starting with v1.8 for endpoints that are updated with the relevant agent version. Agents and their versioning can be found and downloaded from your workspace at Control Panel > Endpoint Devices.
Known issues
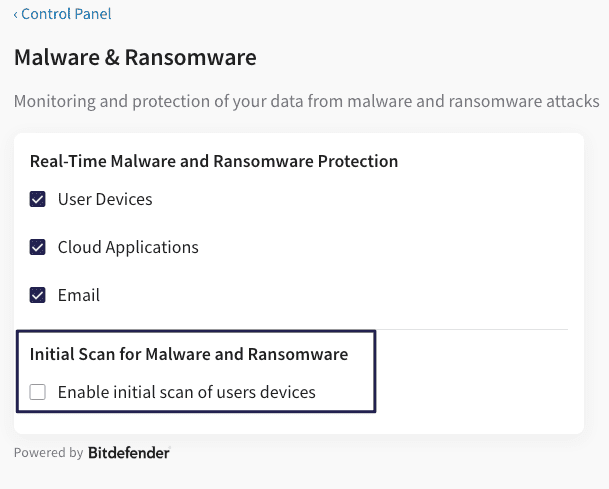
- For Windows endpoint devices with the 1.9 agent installed, the Initial scan option for endpoints is now available at Control Panel > Malware&Ransomware .
- In order to enable scanning of sensitive data inside images on endpoint devices, first install the OCR software Tesseract on Windows endpoints or macOS endpoints . You should install Tesseract prior to installing the agent, or alternatively reboot the device once you've installed both.
- Users should avoid installing Bitdefender products external to the Coro agent on their endpoint devices. In addition, if Bitdefender products were removed from endpoint devices, we recommend that you double-check to ensure all artifacts were successfully removed as well.