Setting access permissions for your cloud applications
Coro supports the ability to set access permissions for connected cloud applications. Admin users with sufficient permissions can allow access to a cloud application based on whether a user meets a defined set of criteria.
For Coro to monitor and report security issues, at least one cloud application must be connected.
note
To see a list of supported cloud applications, see Introducing cloud security.
Configuring new access permissions
To configure new access permissions for a connected cloud application:
- Sign in to the Coro console .
-
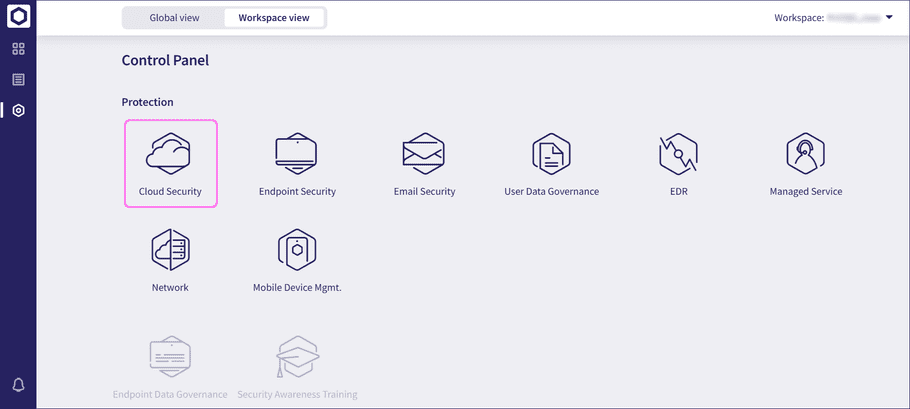
From the sidebar, select
 to access the
Control Panel
. Then, select
Cloud Security
:
to access the
Control Panel
. Then, select
Cloud Security
:
-
From the
Cloud Security
page, select
Access permission
:
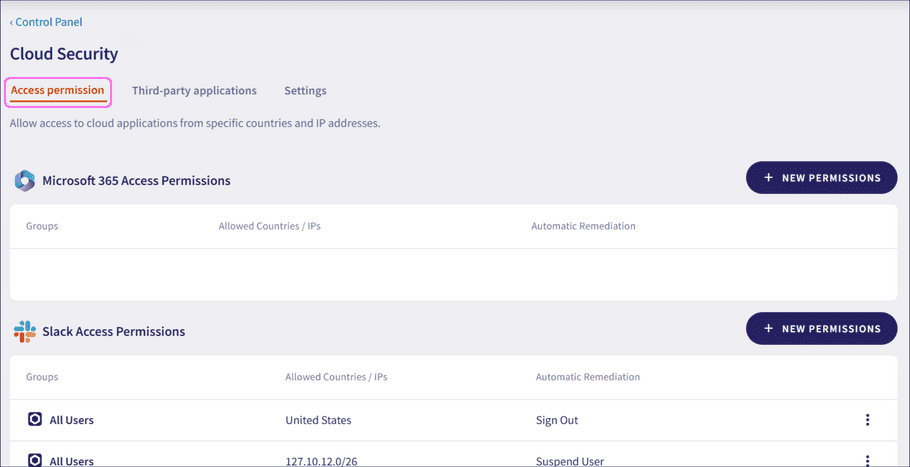
Coro displays the access permissions defined for the connected cloud applications.
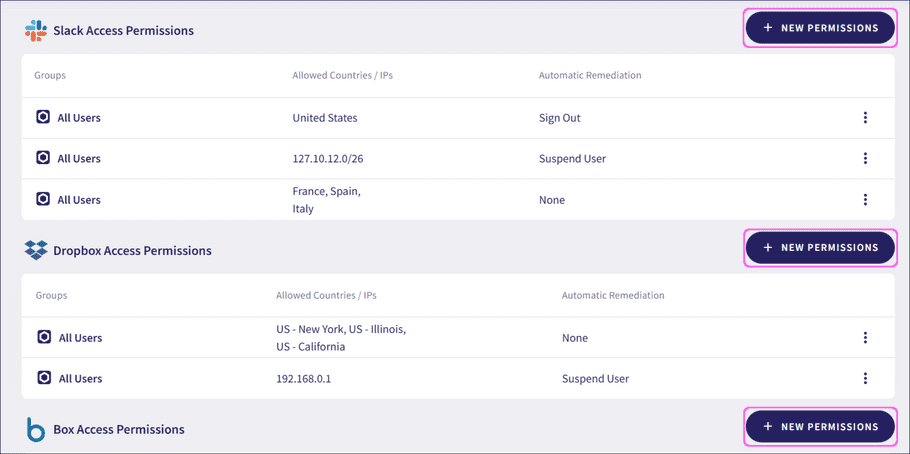
-
To add a new access permission for a cloud application, select
+ NEW PERMISSIONS
for that cloud application:
attention
If your selected application has no current access permissions set, select NEW PERMISSIONS to start the process.
-
Select from the permission levels displayed:
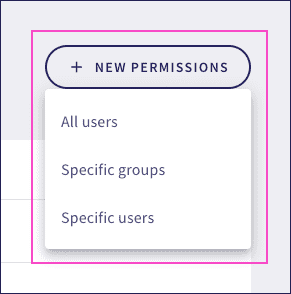
- All users : The new permission applies to protected and protectable users.
-
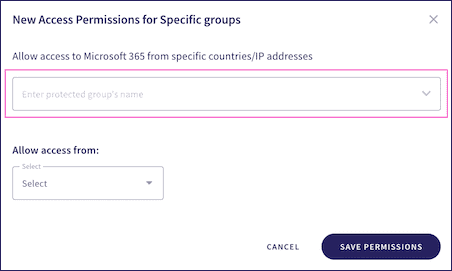
Specific groups
: The new permission applies to a named group within the corresponding cloud application:
note
When a user belongs to several groups, they inherit the collective permissions of all those groups.
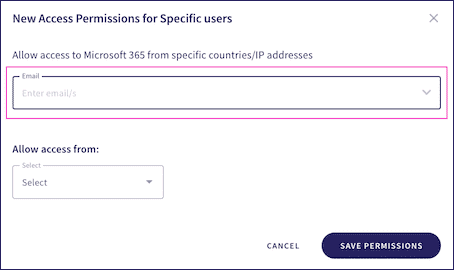
-
Specific users
: The new permission applies to users within the application, specified by their email addresses:
note
You can assign access permissions to existing admin users within the corresponding cloud application.
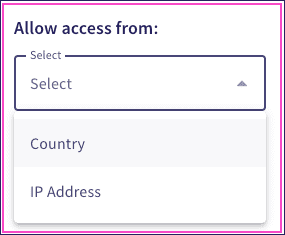
-
Select
IP Address
or
Country
from the following
Allow access from
options:
-
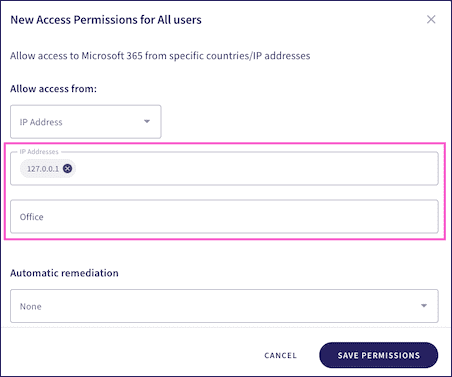
IP Address:
Restricts access to a defined range of IP addresses. Enter the allowed IP addresses into the
IP Addresses
field and provide an optional short description:
-
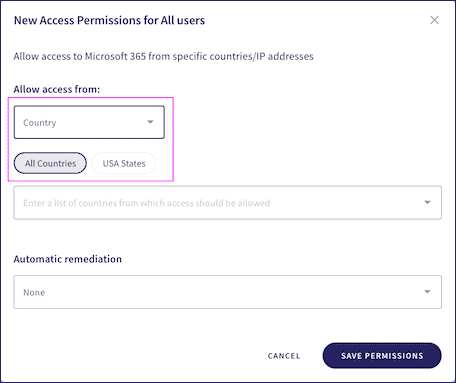
Country:
Restricts access to named countries or US States. Select either
All Countries
or
USA states
:
warning
US state permissions are independent of country permissions. You can select several countries and/or states. If United States is selected as a Country then permissions apply to all US states.
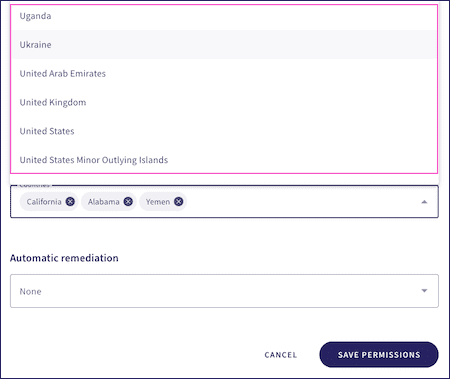
Coro displays a list of countries or US states based on your selection for Allow access from. Select the US states and/or countries to allow access from:
-
IP Address:
Restricts access to a defined range of IP addresses. Enter the allowed IP addresses into the
IP Addresses
field and provide an optional short description:
-
Set the type of automatic remediation Coro should apply when a user that does not meet the permission criteria attempts to access the application. Choose from:
- None : No remediation steps are required.
- Suspend : The user account is automatically suspended.
- Sign in : The user must re-enter their credentials.
Coro creates an Access permissions violation ticket if a user successfully logs into a protected service from an origin in violation of the configured access rules.
-
Select
SAVE PERMISSIONS
to save your changes.
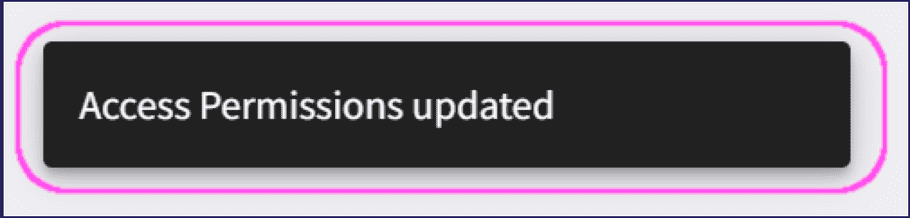
Coro closes the New Access Permissions dialog and displays a confirmation message on the Cloud Security page:
Editing and deleting existing access permissions
Admin users with sufficient permissions can edit and delete existing access permissions.
To edit or delete existing access permissions for a connected cloud service:
- Sign in to the Coro console .
-
From the sidebar, select
 to access the
Control Panel
. Then, select
Cloud Security
:
to access the
Control Panel
. Then, select
Cloud Security
:

-
From the
Cloud Security
page, select
Access permission
:

Coro displays the access permissions defined for the connected cloud applications.
-
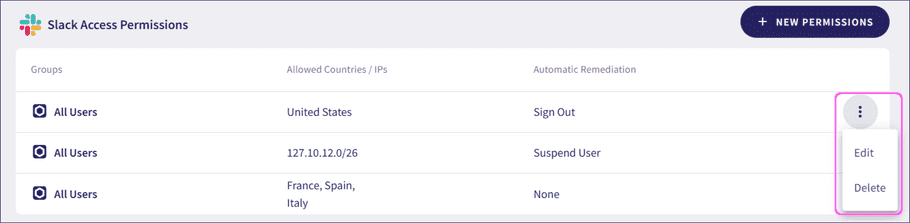
From your list of connected cloud applications, select the corresponding action from the three-dot menu:
- Select Edit to change an existing access permission.
- Select Delete to remove an existing access permission.