Ticket types for Endpoint Detection and Response (EDR)
Coro EDR detects and creates tickets based on malicious processes detection rules.
EDR ticket components
EDR tickets contain the following components:
-
Description
: The EDR ticket detection rule. Select
See more
to view a description of the detection rule that triggered the creation of the EDR ticket:
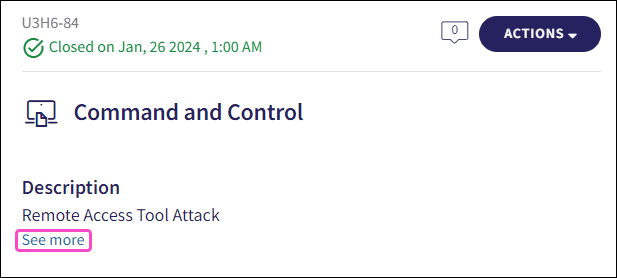
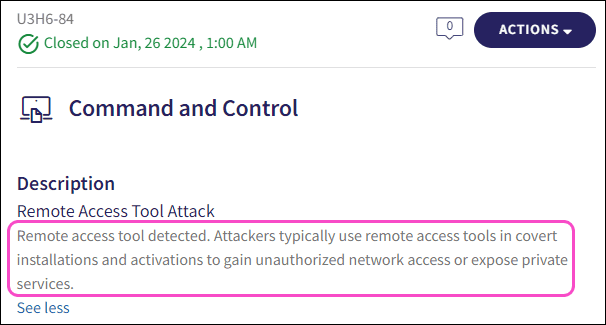
The detection rule description is displayed:
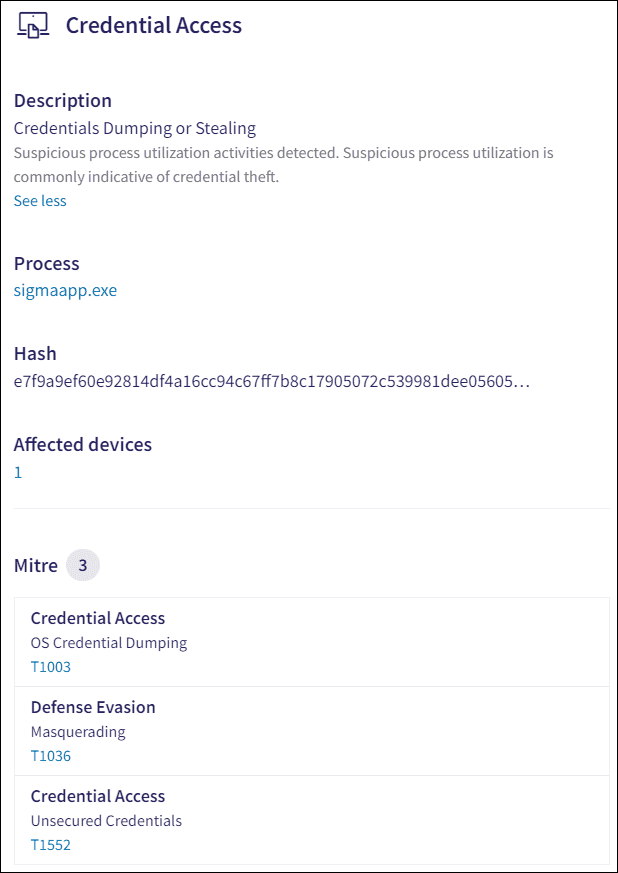
- Process : The name of the process executable file which triggered the creation of the EDR ticket.
- Hash : The unique process identifier.
- Affected devices : Select the displayed device count to view the filtered Devices page showing the affected devices related to the EDR ticket.
-
Mitre
: This section lists specific techniques and tactics from the MITRE ATT&CK framework associated with the security incident. Each entry includes the tactic category and a detailed technique description. Select a technique ID to view detailed entries in the MITRE ATT&CK database and learn more about the security incident.
-
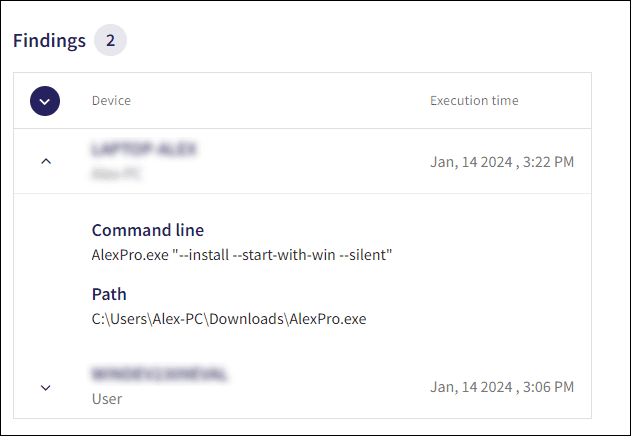
Findings
: This section displays additional details related to the process that triggered the creation of the EDR ticket:
-
Command line
: The full command used to start the process.
note
If the command line is base64 encoded, Coro automatically decodes and displays the text value.
-
Path
: The directory path of the malicious processes image file.
-
Command line
: The full command used to start the process.
EDR detection rules
Coro EDR identifies malicious processes based on detection rules and creates tickets for detected events.
- Command and Control
- Credential Access
- Defense Evasion
- Discovery
- Execution
- Initial Access
- Persistence
Command and Control
Command and Control refers to a type of cyber threat where an attacker takes control of a compromised device to steal data, spread malware, or create a botnet. The attacker uses a command and control server to send commands to compromised devices and receive stolen data from them. Coro EDR detects and creates tickets for the following Command and Control rules:
Remote Access Tool Attack
Coro EDR detected a remote access tool on one or more devices. Attackers typically use remote access tools in covert installations and activations to gain unauthorized network access or expose private services. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Suspicious Usage of a LOLBin
Coro EDR detected a Living Off The Land Binary (LOLBin) on one or more devices. LOLBins are legitimate system tools that are often exploited to discreetly download/execute malicious activities and avoid detection by mimicking normal system processes. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Credential Access
Credential Access refers to any attempt to steal or unlawfully use login credentials to gain unauthorized access to data or devices. Coro EDR detects and creates tickets for the following Credential Access rules:
- Brute force attempt using a non-existent username
- Repeated brute force attempts using wrong passwords
Brute force attempt using a non-existent username
Coro EDR detected suspicious account activity on one or more devices. Such activity is indicative of attempts at account manipulation or brute force attacks, aimed at exploiting user credentials and potentially leading to unauthorized system access. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Repeated brute force attempts using wrong passwords
Coro EDR detected suspicious account activity on one or more devices. Such activity is indicative of attempts at account manipulation or brute force attacks, aimed at exploiting user credentials and potentially leading to unauthorized system access. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Defense Evasion
Defense Evasion refers to techniques and strategies that attackers use to avoid detection and bypass security mechanisms. Coro EDR detects and creates tickets for the following Defense Evasion rules:
Malicious UAC Bypass
Coro EDR detected User Account Control (UAC) bypass. UAC bypass techniques are indicative of an attacker attempting to gain elevated system privileges. Tickets remain in an open state for Admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Execution of a renamed tool
Coro EDR detected a renamed tool. Renamed tools are indicative of a masquerading technique used to avoid detection. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Discovery
Discovery refers to actions or behaviors by an attacker aimed at gathering information about the devices, networks, or infrastructure they have infiltrated. Coro EDR detects and creates tickets for the following Discovery rules:
Unauthorized System Discovery Activity
Coro EDR detected 'whoami' command usage on one or more devices. 'whoami' command usage is potentially indicative of attackers performing system discovery, which assists them in determining user identities and system privileges. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Execution
Execution refers to techniques and strategies used by attackers to run malicious code on a target device or network. Coro EDR detects and creates tickets for the following Execution rules:
- Suspicious Usage of a LOLBin
- Malicious File Download and/or Execution
- Malicious PowerShell Download from External Source
- Malicious Base64-Encoded PowerShell Command Usage
Malicious File Download and/or Execution
Coro EDR detected 'curl' usage. 'curl' usage is potentially indicative of attackers downloading and remotely executing payloads, allowing discreet transfer and execution of malicious files. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Malicious PowerShell Download from External Source
Coro EDR detected PowerShell execution with indicative file download attempts. PowerShell's legitimate scripting features are commonly exploited to covertly transport and execute malicious payloads. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Malicious Base64-Encoded PowerShell Command Usage
Coro EDR detected Base64 encoded PowerShell commands. Base64 encoded PowerShell commands are commonly indicative of an attempt to hide malicious scripts from detection tools. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Initial Access
Initial Access refers to the techniques and strategies used by attackers to gain entry into a network or device for the first time. Coro EDR detects and creates tickets for the following Initial Access rules:
Persistence
Persistence refers to techniques and strategies used by attackers to maintain control of a device or network over an extended period, often stealthily. Coro EDR detects and creates tickets for the following Persistence rules:
Malicious Scheduled Task Creation/Execution
Coro EDR detected scheduled task creation or execution, which can indicate an attempt by attackers to gain persistence or execute malicious code at predetermined times. Tickets remain in an open state for Admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Modification of User Accounts in Elevated Groups
Coro EDR detected suspicious account activity, indicative of attempts at account manipulation or brute force attacks, aimed at exploiting user credentials and potentially leading to unauthorized system access. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Password spray attack involving 200 login attempts
Coro EDR detected suspicious account activity on one or more devices. Such activity is indicative of attempts at account manipulation or brute force attacks, aimed at exploiting user credentials and potentially leading to unauthorized system access. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |
Password spray attack involving 100 login attempts
Coro EDR detected suspicious account activity on one or more devices. Such activity is indicative of attempts at account manipulation or brute force attacks, aimed at exploiting user credentials and potentially leading to unauthorized system access. Tickets remain in an open state for admin user review and close automatically after a period of 48 hours.
| Action | Outcomes |
|---|---|
| Close ticket | (Open tickets only) Closes the ticket and does not take any remediation action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Re-open | (Closed tickets only) Reopens the ticket for admin user intervention and manual remediation. |
| Reboot devices | Reboots the affected device(s). For further information, see EDR Processes |
| Shut down devices | Shuts down the affected device(s). For further information, see EDR Processes |
| Un-log and remove from audit reports | (Closed tickets only) Removes the ticket from your workspace status update emails. Note: Un-logged tickets include a Log and reference for audit reports action to re-include the ticket in your update emails. |
| Block process | Blocks the execution of a process. An entry is added to the EDR and Endpoint Security Blocked list. For further information, see Endpoint Security Allow/Block lists, Block proccesses, and EDR Processes. |
| Isolate affected devices from network | Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. The Coro process remains functional in order to communicate with the Coro server via a command prompt. For further information, see EDR Processes |