An unencrypted endpoint drive on a Windows or macOS device stores data without encryption, making it vulnerable to unauthorized access if the device is lost or stolen.
To create a new Unencrypted Endpoint Drive policy:
Select + ADD:

Select Add to Windows or Add to macOS:
Coro displays the Add new device policy dialog.
Select Unencrypted Endpoint Drive from the Select policy type dropdown:
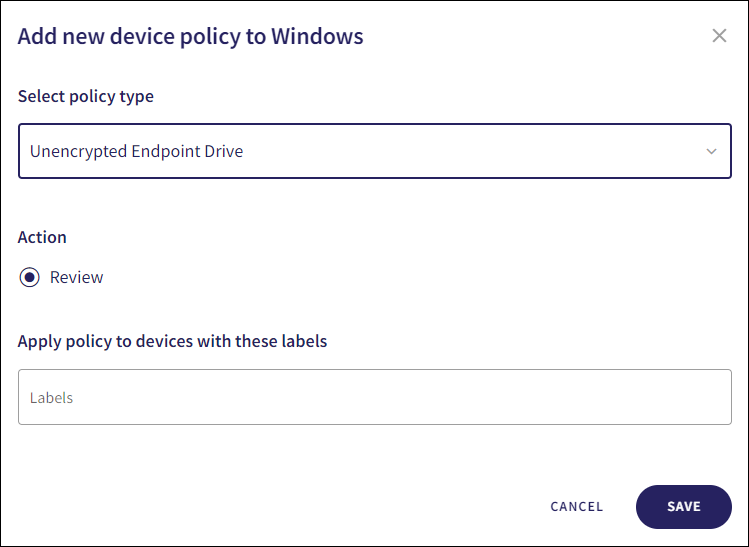
Select the policy Action:
- Review: Coro does not perform auto-remediation. It creates a review ticket that remains open for 10 days before closing automatically. During this time, Coro adds any newly detected affected devices to the ticket. Admin users can close the ticket manually at any time.
If the policy violation reoccurs after a ticket is closed, Coro automatically creates a new ticket.
To apply the policy to specific device groups, select device labels from the Labels dropdown:

To create the policy, select SAVE.
When encryption is disabled on a device drive, Coro creates an Unencrypted endpoint drive ticket.
To view the policy, select the dropdown next to Unencrypted Endpoint Drive on the Device Posture page.
Coro displays the following policy details:
The applicable policy device labels.
The selected policy action.

For more information on Windows device drive encryption, see Encrypting endpoint device drives.