Apple Mobile File Integrity Disabled
Apple Mobile File Integrity (AMFI) enhances the security of the macOS platform by enforcing code signature validation for all apps and executable files that run on macOS devices. During development, temporarily disabling AMFI may be required in order to run and test unsigned or self-signed applications.
Creating a new Apple Mobile File Integrity Disabled policy
To create a new Apple Mobile File Integrity Disabled policy:
From Device Posture, select + ADD:

Select Add to macOS.
Coro displays the Add new device policy to macOS dialog.
The Apple Mobile File Integrity Disabled device policy is currently supported for macOS devices.
Select Apple Mobile File Integrity Disabled from the Select policy type dropdown:
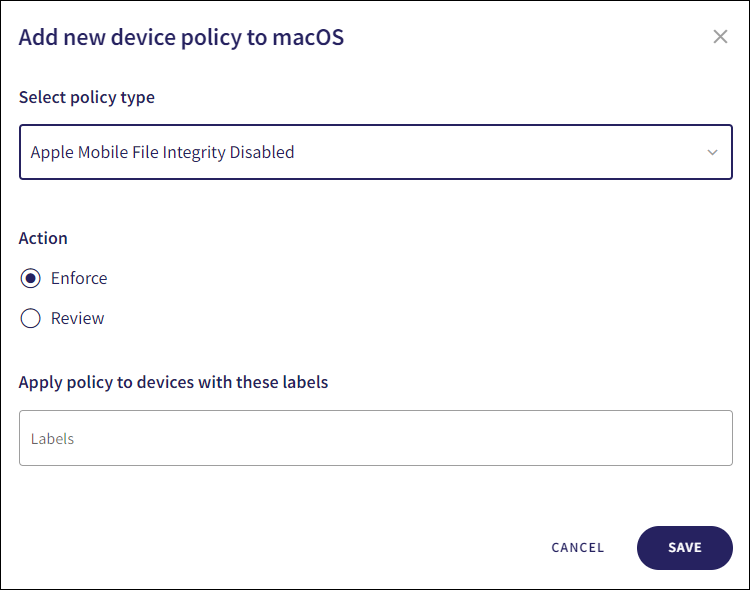
Select the policy Action:
- Review: Coro does not perform auto-remediation. It creates a review ticket that remains open for 10 days before closing automatically. During this time, Coro adds any newly detected affected devices to the ticket. Admin users can close the ticket manually at any time.
- Enforce: Coro performs auto-remediation, records the action in a ticket, and closes the ticket automatically.
If the policy violation reoccurs after a ticket is closed, Coro automatically creates a new ticket.
Enter label names (predefined or custom) to the Labels field listed under Apply policy to devices with these labels to apply the new policy to specific groups of devices.

Select SAVE.
Coro creates the policy with the configured settings.
When Apple Mobile File Integrity is disabled on a macOS device, an Apple Mobile File Integrity disabled ticket type is created.
Select the dropdown next to Apple Mobile File Integrity Disabled on the Device Posture tab to view the policy. See Device posture configuration overview.
Coro displays the following policy details:
Device labels applicable to the policy.
The action(s) applicable to the policy, for example, Enforce.
