Admin users with sufficient permissions can set and manage device posture policies for endpoint devices via the Device Posture page. Coro collects and analyzes data from connected devices to ensure compliance with these policies.
Device posture policies are grouped according to the following device vulnerabilities:
Coro restricts certain device posture policies to specific operating systems.
Coro applies device posture policies to groups of devices by assigning device labels to each policy. Device labels enable Coro to apply policies to groups of devices that share the same label. Unless otherwise specified, Coro generates an Endpoint Security ticket and initiates the specified remediation action if a device fails to comply with a posture policy.
Coro lists device posture policies under each vulnerability, along with their corresponding device labels and remediation actions:
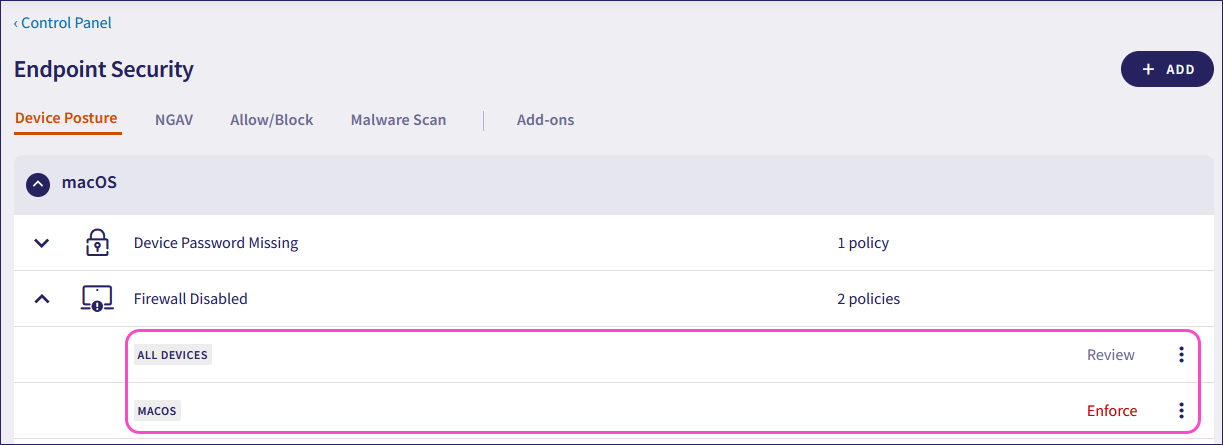
To access the Device Posture page:
Select Device Posture:
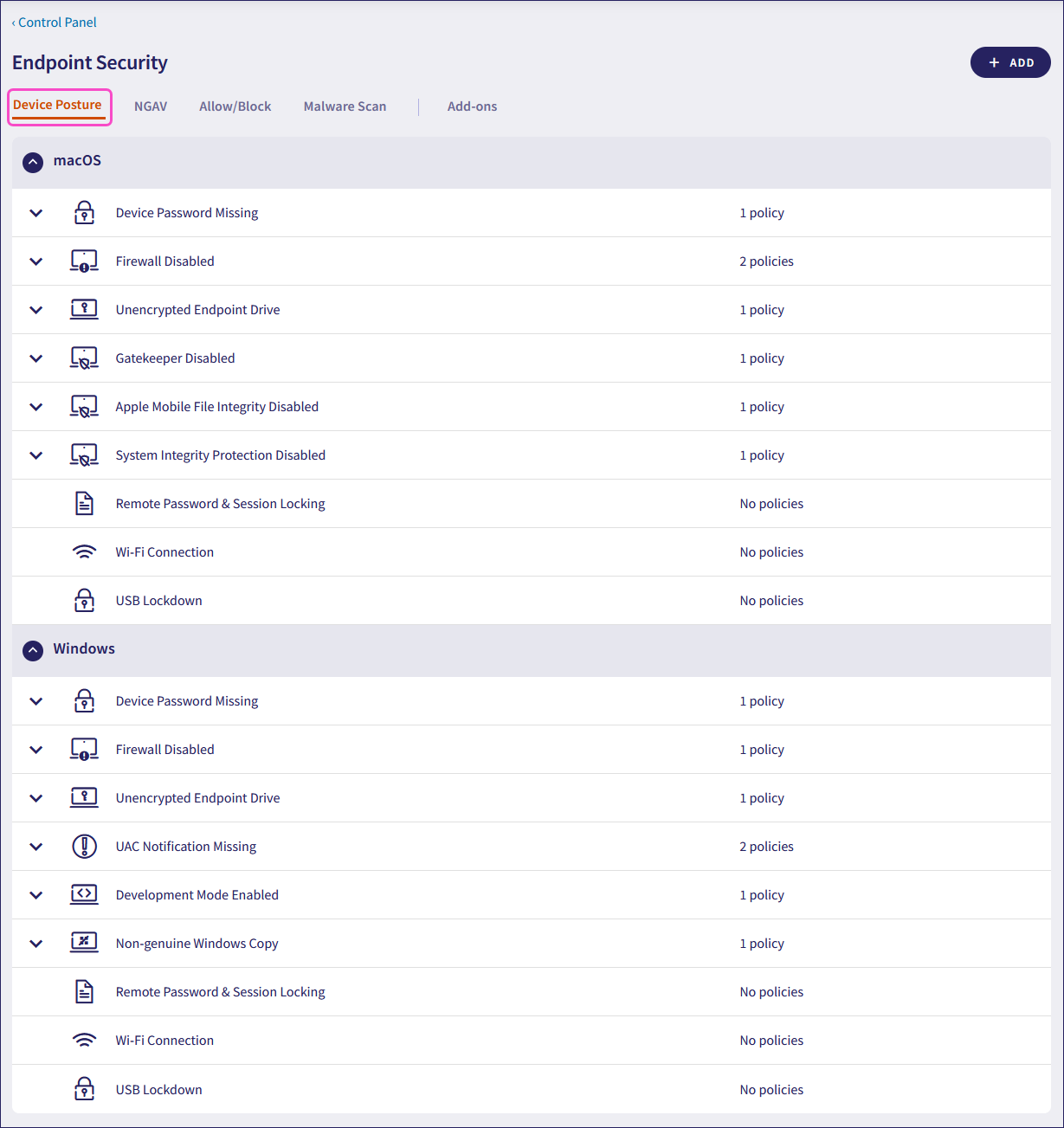
To edit an existing device posture policy:
Select the dropdown next to the desired policy group name:
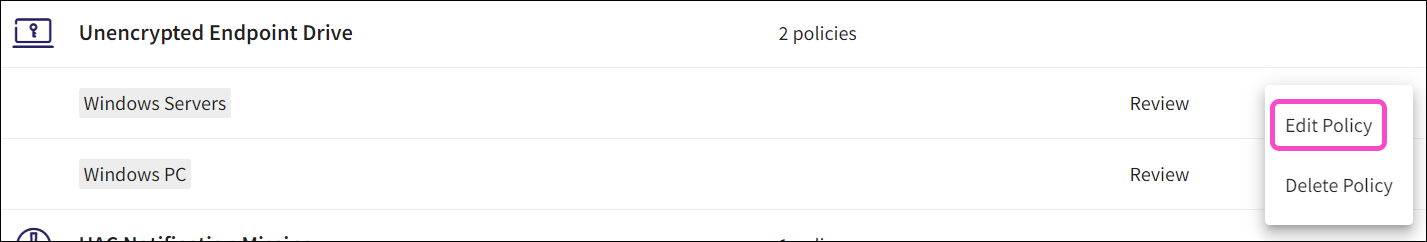
Select the three-dot menu next to the desired policy:
Select Edit policy:
Select the remediation action for the policy:
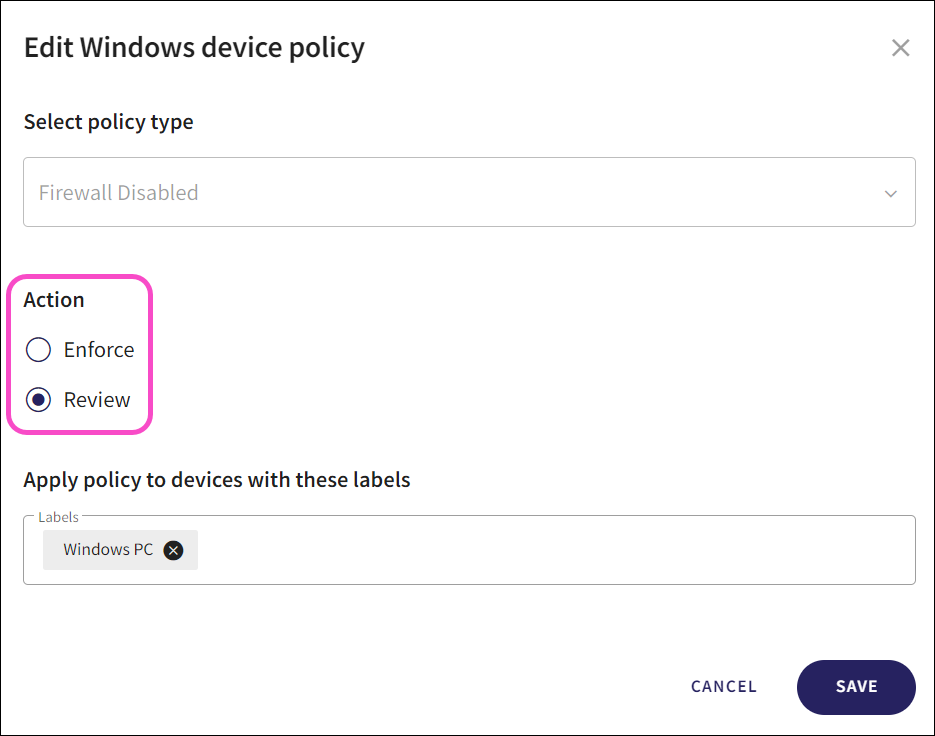
You can select the following remediation actions, depending on the policy:
Review: No auto-remediation is performed, and the ticket is classified as requiring review. The ticket remains open until either an admin user closes it manually or the vulnerability is observed by the Coro endpoint agent as being resolved.
Enforce: Auto-remediation is performed, recorded in the ticket, and the ticket is auto-closed.
After you create a workspace for new customers, Coro sets all Device Posture settings to "Review" by default. This setup enables you to configure your Device Posture settings according to your preferences and security requirements.
Device Posture settings for existing customers remain unchanged.
Select device labels to apply to the policy from the Apply policy to devices with these labels field:
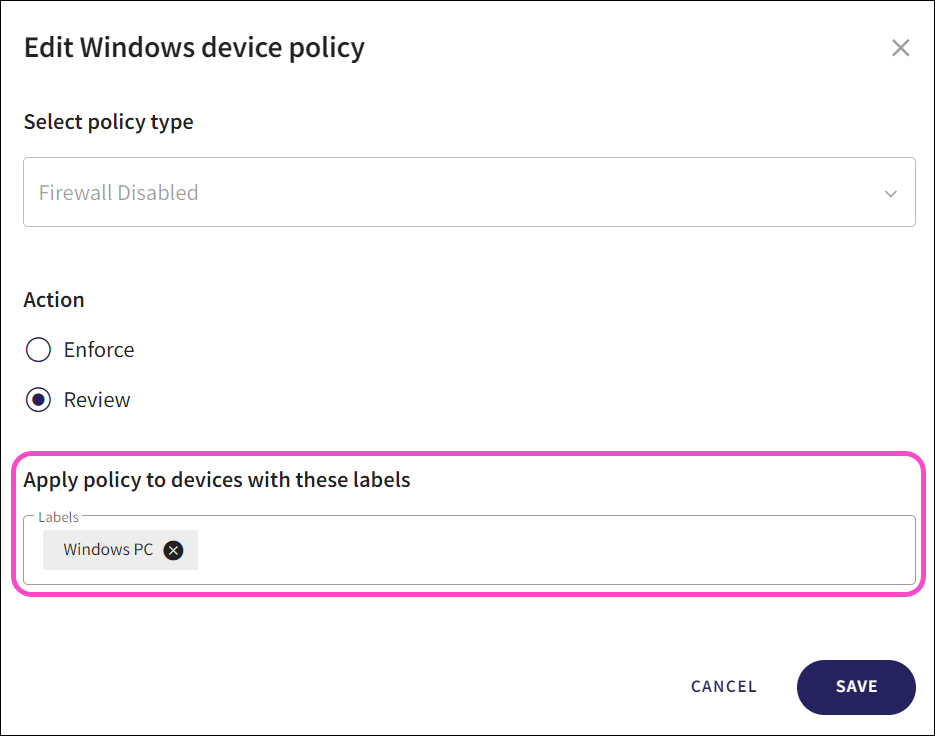
Select SAVE to apply your changes.
To remove an existing device posture policy:
Select the dropdown next to the desired policy group name:

Select the three-dot menu next to the desired policy:

Select Delete policy:
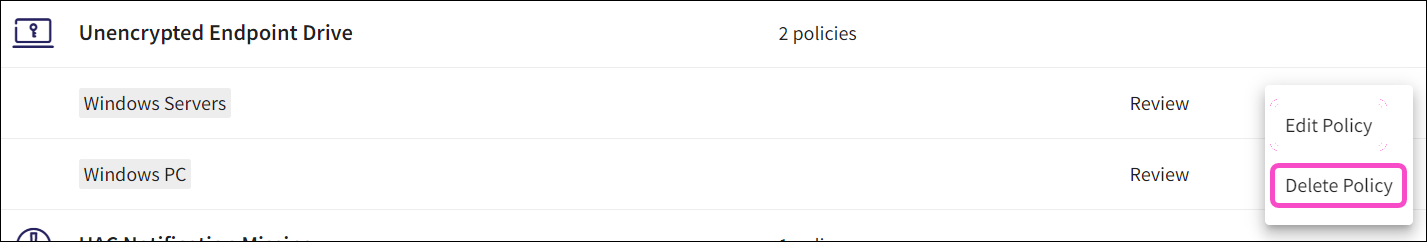
Coro displays the Delete policy dialog.
Select CONFIRM:
Coro removes the device posture policy.