The NGAV page is used to configure settings for device monitoring using the Coro Agent. These settings apply to all devices in the workspace.
To access the NGAV page:
Select NGAV:
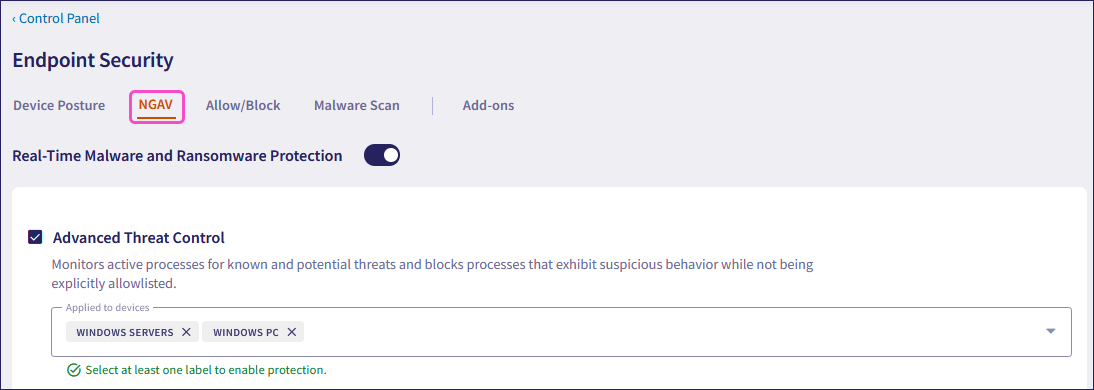
Enable Real-Time Malware and Ransomware Protection to configure the following settings:
- Advanced threat control
- Secured shadow backups
- Quarantine infected containers
- Enable an initial malware and ransomware scan
Disabling Real-Time Malware and Ransomware Protection leaves your device vulnerable to threats such as malware, viruses, and ransomware.
The settings below can be applied to groups of devices using predefined or custom device labels.
When you enable a setting, Coro automatically applies the All devices label, which you can change as required.
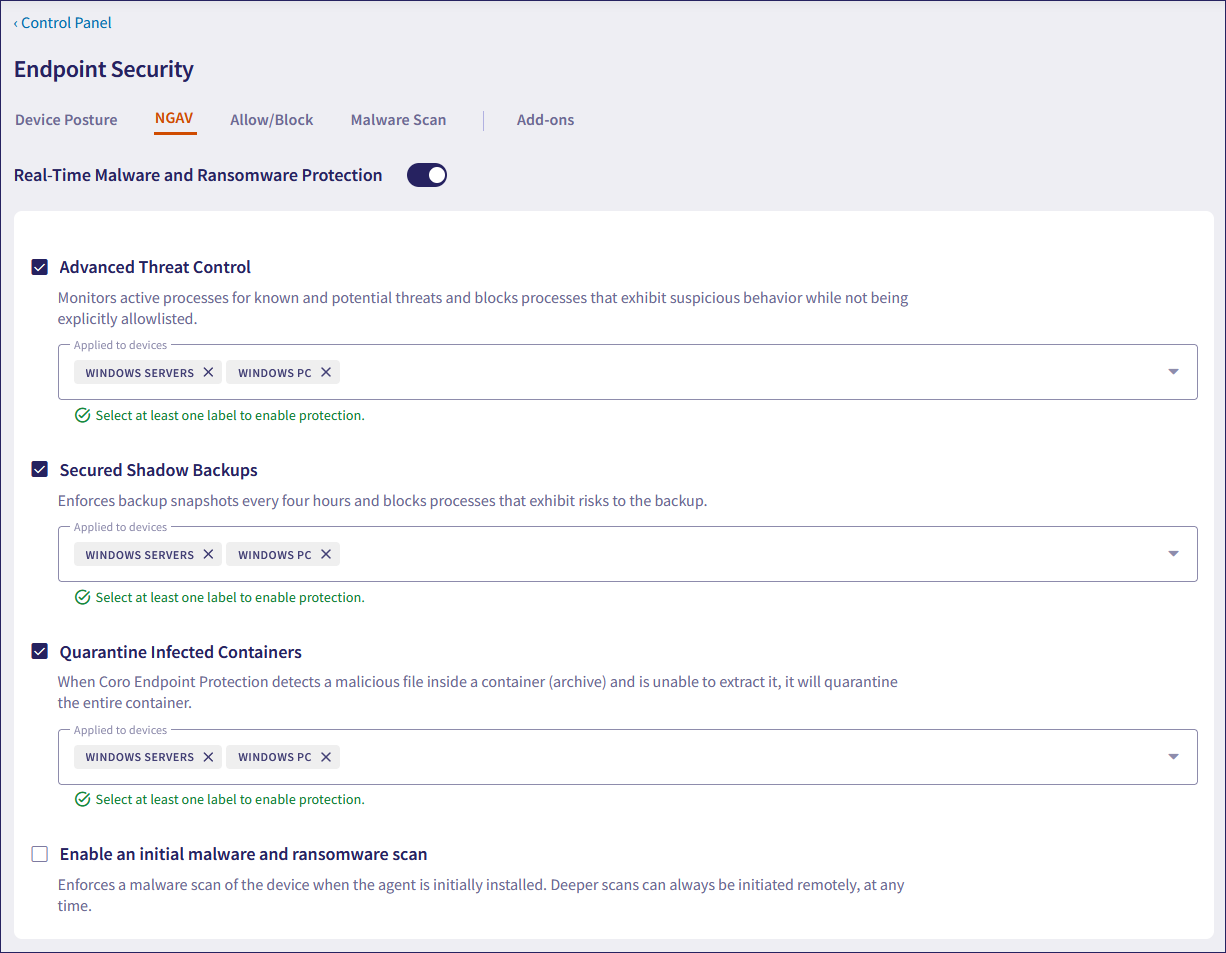
When enabled, Coro monitors active processes for known and potential threats, and terminates processes that exhibit suspicious behavior.
Advanced threat control (ATC) provides an additional layer of real-time monitoring by analyzing processes for known and potential threats. ATC blocks any processes that exhibit suspicious behavior.
Processes that are not explicitly allowlisted are displayed on the Allow/Block list as Blocked, see Endpoint Security Allow/Block list.
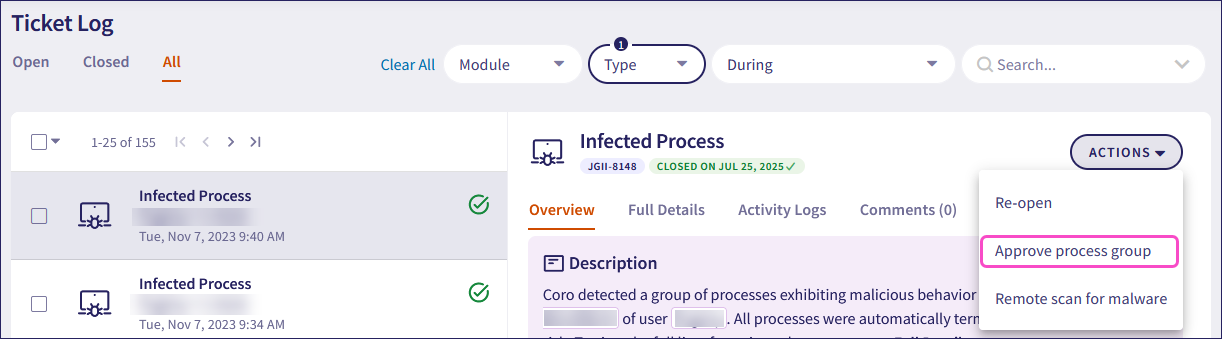
You can enable a blocked process to run on a device from the respective Infected Process ticket using the Approve process group action:
By default, Advanced Threat Control is enabled.
To learn more, see Infected process.
When enabled, Coro creates backup snapshots every four hours and blocks processes that pose risks to backups. Coro uses Windows VSS (Volume Shadow Copy Service) to save snapshots of device files.
Coro protects its backups from corruption or deletion, while other shadow copies, such as those created by Windows, remain vulnerable. Frequent backups protect against ransomware, which typically encrypts or corrupts local files, enabling faster recovery and reducing business impact.
Coro stores quarantined files in a dedicated folder with no maximum size limit. Coro deletes quarantined files after 30 days.
By default, Secured Shadow Backups is enabled.
To learn more, see Using VSS backup protection on your Windows endpoints.
When enabled, if Coro detects a malicious file inside a container (archives such as ZIP, RAR, other compressed formats, or self-extracting installers such as .exe files) and is unable to remove the file, Coro quarantines the entire container and creates a Malware on endpoint ticket.
Coro currently does not extend protection to containerized application workloads, such as those running on Docker or Kubernetes.
By default, Quarantine Infected Containers is enabled.
When enabled, a malware scan of the device is performed upon initial installation of the Coro Agent. Deeper scans can be initiated remotely at any time.
By default, Enable an initial malware and ransomware scan is disabled.
To learn more, see Endpoint Security ticket types.
Coro has deprecated Enhanced EDR block mode. During deployment, Coro now registers itself as the primary security product in Windows Security Center (WSC), which causes Microsoft Defender Antivirus to disable itself. No additional configuration is required.
Protected users do not need to take any action.
When Coro Endpoint Protection is used side-by-side with Windows Defender antivirus, Coro provides added endpoint detection and response (EDR) from potential threats. Enhanced EDR block mode enforces this added protection by ensuring access to timely data that may otherwise be suppressed by the environment.