Control panel
Accessing the control panel
The Control Panel enables you to configure protection settings for your subscribed security modules and add-ons. The Control Panel is also where you administer your workspace, cloud applications, protected users, and their devices.
To access the Control Panel, sign in to the Coro console and from the sidebar, select
![]() .
.
In addition, each dashboard panel (and optional module or add-on) in the Actionboard includes a Control panel icon, designed to enable you to quickly access the relevant settings page:
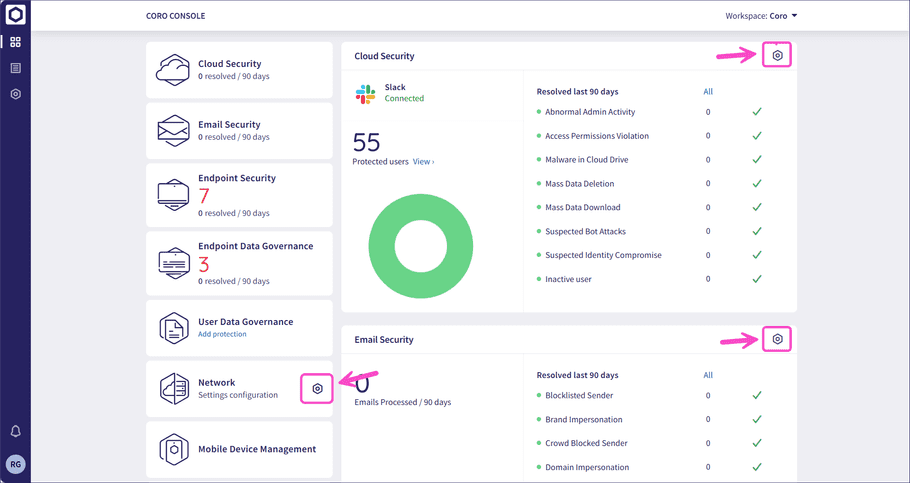
Using the Control Panel
The Control Panel contains the following options, separated into Protection and Workspace:
note
Coro displays modules that aren't part of your subscription as disabled.
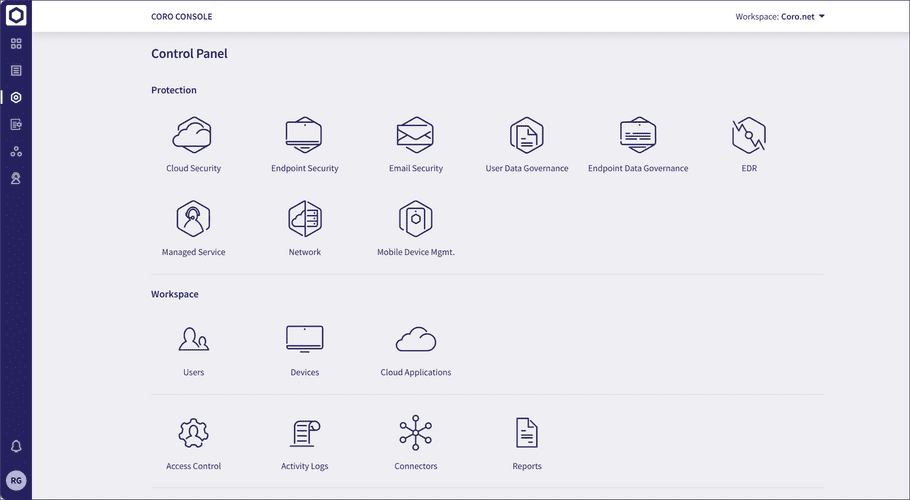
Select an object to access the settings page for that component.
At the bottom of the page, Coro displays your workspace name and ID.

Protection
Cloud Security
Monitor and control access to connected cloud applications and data. See Setting permissions for your cloud applications.
Endpoint Security
Manage the protection features for endpoint devices. See Introducing Coro Endpoint Security.
Email Security
Configure email security settings, including trusted and untrusted domain lists. See Introducing Email Security.
User Data Governance
Manage your users' access to sensitive information and configure how Coro monitors data sharing. See Introducing User Data Governance.
Endpoint Data Governance
Configure monitoring for storage of sensitive information on your users' endpoint devices. See Introducing Endpoint Data Governance.
EDR
Access the Endpoint Detection and Response module page. See Coro Endpoint Detection and Response (EDR).
Managed Service
Access the Managed Service page. See Managed Service.
Network
Access the Network module page. See Network.
Workspace
Users
Manage lists of your users and user groups. See Adding users and user groups for protection.
Devices
Get Coro Agent deployment packages, manage device labels, and configure monitoring settings. See Introducing devices.
Cloud Applications
Connect cloud applications to be monitored for users. See Introducing cloud security.
Access Control
Manage admin users, add new admin users, set roles and permissions, and review active sessions. See Introducing Access Control.
Activity Logs
View the activity logs for your workspace. See Activity Log.
Connectors
Configure connectors for integrating Coro with external Security Information and Event Management (SIEM) services. See Security Information and Event Management (SIEM) integration.
Reports
View, download, and export activity summary reports for your workspace. See Viewing reports.