Introducing Coro Endpoint Security
Coro Endpoint Security is a robust solution that utilizes the Coro Agent to automatically recognize any endpoint devices that have the Coro Agent installed on them. Coro Endpoint Security records and logs all endpoint activity, analyzing all activity related to data movement to detect anomalies, including human error, and automatically remediate 95% of security incidents found.
Coro Endpoint Security:
- Seamlessly integrates with the Coro Console and full range of security modules.
- Protects businesses from Wi-Fi phishing and malware.
- Provides Antivirus (AV) and Next Generation Antivirus (NGAV) protection.
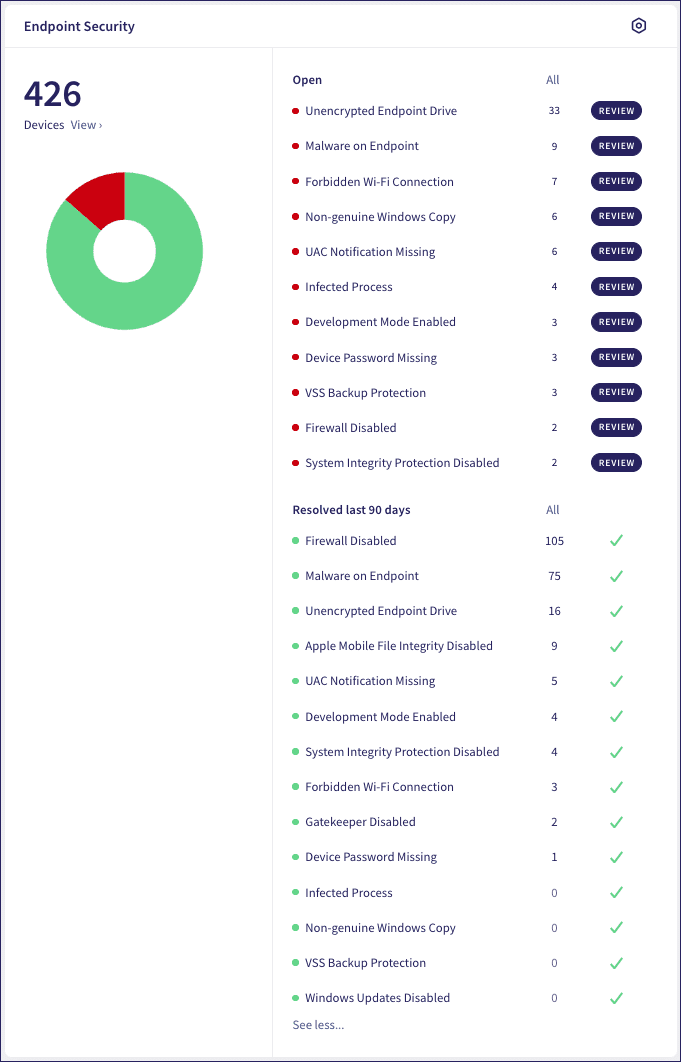
Coro further classifies endpoint security specific ticket types, each pertaining to one or more related findings. To see the full list of Coro's Endpoint Security ticket types and the corresponding outcomes, see Endpoint Security ticket types.
In the Coro Console, view all email security tickets by selecting the Endpoint Security component of the Actionboard:
To learn more about all Actionboard components, see Actionboard overview.
To learn more about how Coro processes and presents tickets for review, see Ticket log.
To learn more about deploying the Coro Agent, see the following guides: