The Actionboard
Your Coro service is managed through the Coro console, a web-based portal accessible through most common browsers. The console provides all the tools needed to manage and monitor your Coro workspace.
Using the Actionboard
After you sign in to the Coro console, Coro presents the Actionboard. This is the main dashboard to monitor and manage ticket activity for all protected apps, users, and devices.
The Actionboard is divided into the sections marked in the following image:
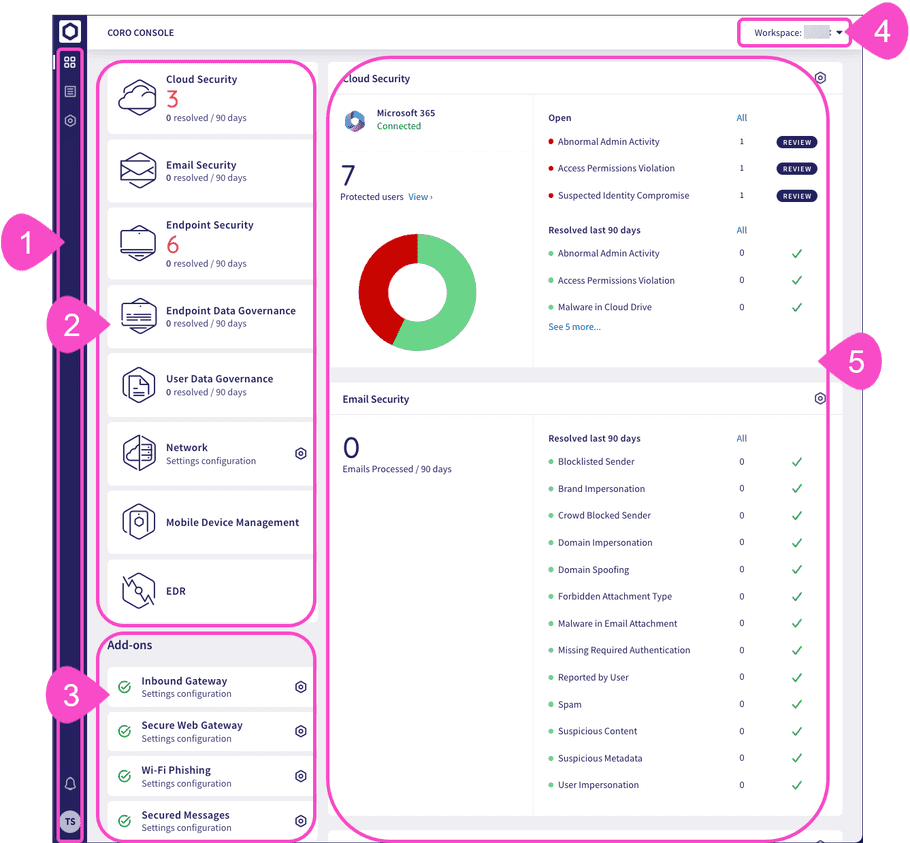
| Element | Description |
|---|---|

|
Sidebar Access and configure the following areas of your workspace: • Lists: • Devices: A list of your protected endpoint devices. • Protected Users: A list of your protected users. • Ticket Log: Full details of all open and closed tickets. • Control Panel: Your protection, security, and workspace settings. • Messages: View your system messages. • User Profile - Update profile and login settings. |

|
Modules Modules are the security components to which you are currently subscribed. Each module provides a different type of protection. Select a module tile to view the corresponding ticket information dashboard in the right-hand panel. For more information, see Modules and add-ons. |

|
Add ons Add-ons provide optional extra layers of security for certain modules. Select a tile to view Control Panel settings for that add-on. For more information, see Modules and add-ons. |

|
Workspace name Coro displays your current workspace name at the top-left of every screen. Admin users with access to multiple workspaces can switch between workspaces from the dropdown. |

|
Dashboards Detailed ticket and activity dashboard panels for each enabled protection module in your Coro service. When you select one of your protection module tiles, Coro scrolls the page to display the corresponding dashboard panel. |
Modules and add-ons
Coro provides modular cybersecurity protection and monitoring. Users can subscribe to any combination of interconnected modules and pay for only those options that they need, with add-ons offered as optional extensions to particular modules where specific extra functionality is required.
By default, Coro's modular protection is split into the following primary types:
- Cloud Security : Advanced malware and ransomware detection and remediation in cloud drives, including access violations, malware in cloud and mass data download/delete. Admins configure geo-fencing and network-fencing. Consolidated data analysis that optimizes real-timeness of incident detection.
- Email Security : Protection against domain impersonation, or any email with the intention to mislead the recipient and against malware in email attachments.
- Endpoint Security : Protection against real-time malware and ransomware with NGAV, plus management of critical device security features including drive scans, agent updates, activity monitoring, customizable enforcement settings, firewall management, and UAC notifications.
- User Data Governance : Anomaly analysis of exposure of sensitive data (via both: email and files sharing) based on workspace configurations; includes exposure of PHI/PCI/PII/NPI and business sensitive data.
- Endpoint Data Governance : Scanning endpoints for sensitive data based on the workspace configurations; includes exposure of PHI/PCI/PII/NPI.
- EDR : Management of processes and device access to network, telemetry, and post-breach analysis.
- Network : Cloud based virtual office network, providing protection against external and internal attacks.
- Mobile Device Management : Manage iOS, iPadOS, and Android mobile devices for end users across an organization.
In addition, Coro includes add-ons to certain modules providing extra functionality:
| Add-on | Module | Description |
|---|---|---|
| Wi-fi Phishing | Endpoint Security | Endpoint protection from dangerous or risky wifi connections. |
| Secured Messages | Email Security | Sender-to-recipient (outbound) email encryption service offering a secure digital messaging system based on an advanced 2-part encryption mechanism that initiates as soon as a message is sent. |
| Secure Web Gateway | Network | Domain name system (DNS) filtering to restrict or allow access to domains. |
To learn more about Coro's current offerings and prices, or to enable any of these modules, speak to your Coro sales representative or contact Support.