Introducing cloud security
Coro's Cloud Security module is a Cloud Access Security Broker (CASB) based solution, providing advanced malware and ransomware detection and remediation for connected users and their cloud drives.
Coro can connect to an organization's cloud applications to monitor user activity, protect against threats, and control access permissions. To learn more about connecting cloud applications to Coro, see Connecting cloud applications to Coro.
Coro provides detection and remediation for the following threat types:
- Abnormal admin activity
- Access permissions violations
- Impossible traveler
- Malware in cloud drives
- Mass data download or deletion
- Suspected bot attacks
- Suspected identity compromise
Configuring cloud security settings
Coro's Cloud Security module provides settings to control your users' access permissions, threat detection policies, and access to third-party applications.
To configure cloud security settings:
From the sidebar, select Control Panel. Then, select Cloud Security:
Coro displays the Cloud Security page:
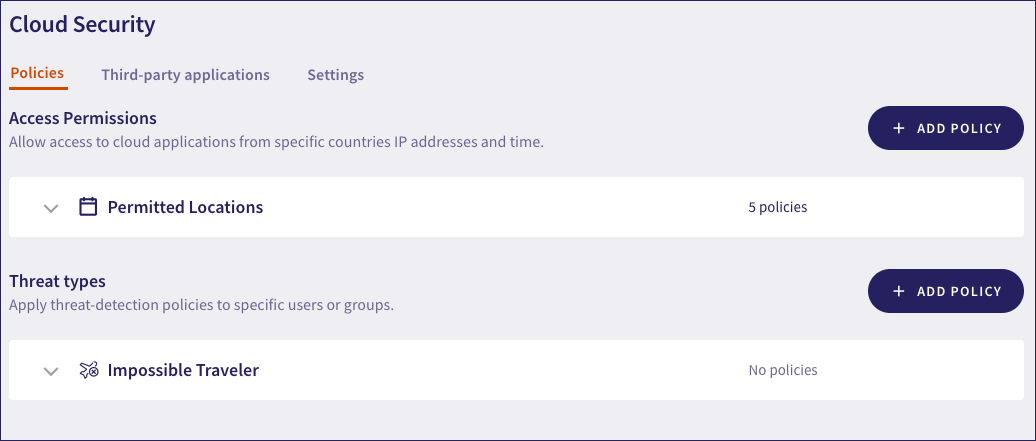
Choose from the following tabs:
Policies: Configure policies for your cloud security relating to access permissions and types of threat.
Third-party applications: Block or allow access to the third-party applications your users access through a connected cloud application.
Settings: Additional cloud security settings.