Wi-Fi Connection
Configure remote device permission policies to manage public Wi-Fi connectivity. Use these policies to block public Wi-Fi access for specific devices or groups. You can apply policies to both Windows and macOS devices.
Public Wi-Fi networks
Public Wi-Fi networks in coffee shops, airports, and hotels provide convenient internet access but come with security risks. These unsecured networks often become targets for cybercriminals, exposing your sensitive data to potential threats. Protect your privacy and security by exercising caution and blocking public Wi-Fi access.
Blocking public Wi-Fi on a device provides these benefits:
- Enhances security
- Protects data privacy
- Minimizes exposure to threats
Wi-Fi connectivity policies
Coro provides two Wi-Fi connectivity policies:
- Deny connection to all unencrypted networks : Blocks access to all public Wi-Fi networks, and only allows access to WPA+ networks.
- Allow connection to specific connections : Enter the SSIDs (unique network names) of trusted networks to create a restricted list. Use this option to block all other public Wi-Fi networks. Select the Enter or Tab key to separate multiple SSIDs.
note
If no policy is applied to a device, that device has no restrictions on Wi-Fi connectivity.
Configuring Wi-Fi connectivity policies
To configure a new public Wi-Fi blocking policy:
-
From the
Device Posture
tab, select
+ ADD
:

-
Select the operating system (
Add to macOS
or
Add to Windows
) where you want to apply the new policy.
Coro displays the Add new device policy dialog.
-
Select
Wi-Fi Connection
from the
Select policy type
dropdown:
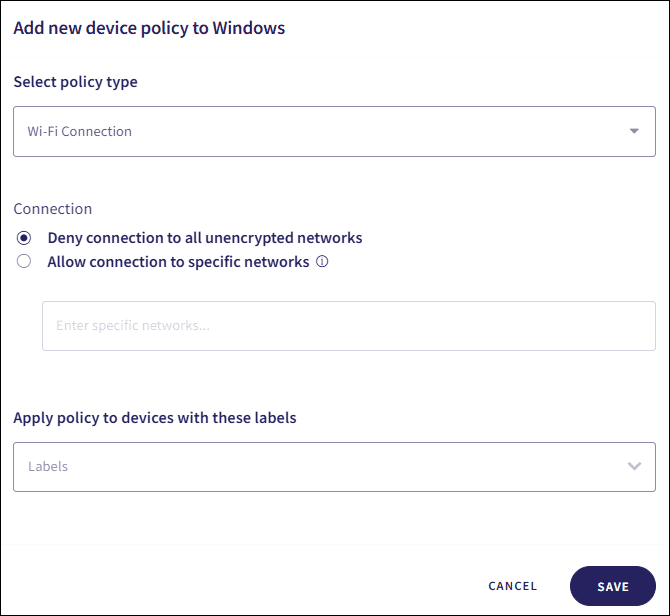
- Select a Connection option, see Wi-Fi connectivity policies .
-
Enter device
Labels
(predefined or custom) to apply the policy to specific device groups:

-
Select
SAVE
to save your new policy with the configured settings.
Coro creates the policy with the configured settings.
View the policy by selecting the dropdown next to Wi-Fi Connection on the Device Posture tab. See Device posture.
Coro displays the following policy details:
- Device labels applicable to the policy.
-
Number of allowed Wi-Fi networks (if
Allow connection to specific connections
is selected):
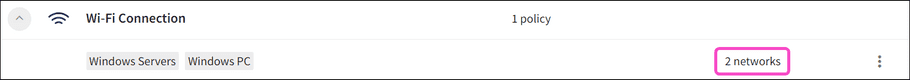 .
. -
Encrypted
(if
Block all unencrypted networks
is selected):
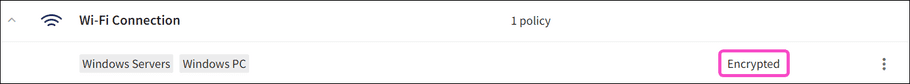 .
.
Policy enforcement
When the policy is active and you attempt to connect to a public Wi-Fi network, the connection fails. Coro creates and automatically closes a Forbidden Wi-Fi Connection ticket with no available actions:
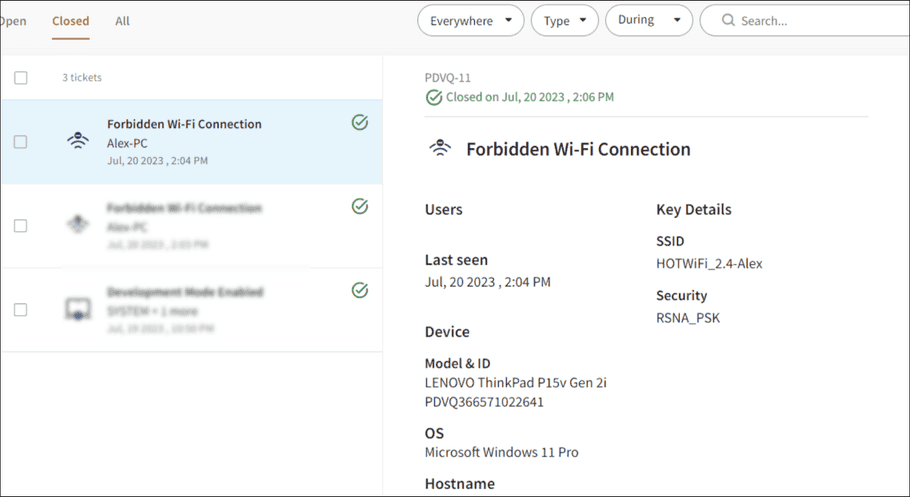 .
.
The Coro Agent displays the following notification:
 .
.
Additionally, the Coro Agent displays a pop-up notification:
 .
.