Tickets play a central role in Coro. They serve as records for detected events or a series of events where Coro identifies suspicious behavior.
For example, if you set up Coro to protect users against email phishing attacks, a ticket is generated each time a phishing attempt is detected.
The detection process is based on three principles:
- Admin users define the expected behavior of users and devices in the organization. For example, enabling firewall features on endpoint devices or restricting access to Microsoft 365 accounts from outside a specific country.
- These detections are predefined based on the configuration set by Admin users in the Coro console.
- Coro follows industry best practices for deletion, modification, and remediation. For example, it verifies the authenticity of email servers used for specific domains.
- It also detects malware fingerprints based on best practices, even if not explicitly specified by an admin user.
- Coro employs adaptive data-driven or artificial intelligence (AI) driven decisions for detection, alerting, and remediation. For example, text classification for email phishing detection or anomaly analysis for identifying suspicious access to cloud app accounts.
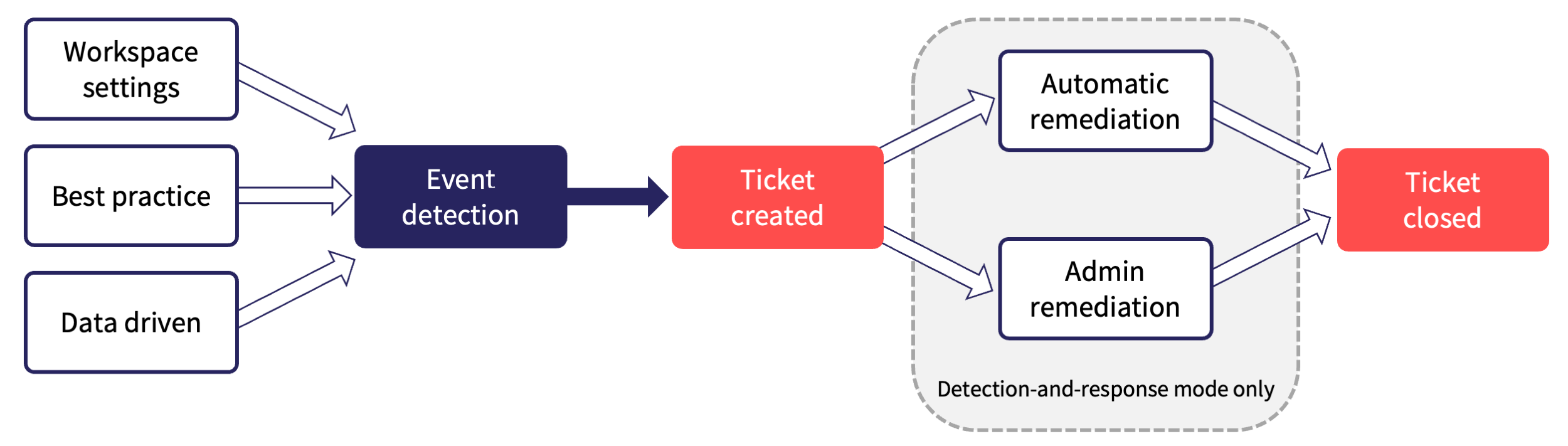
Each of the principles above is used by Coro to detect suspicious behavior. The event could be a single suspicious detection or a series of detections that triggers the creation of a ticket. In most cases, Coro takes the appropriate action and closes the ticket without intervention.
With tickets raised for users that are not currently protected, but classified as protectable, remediation is not applicable and Coro automatically moves opened tickets to a closed state immediately.
When manual review and remediation is required, the ticket remains open on the Coro Console for admin review. Admin users can access a categorized list of open tickets that require manual review and remediation. If a ticket remains unresolved after a period of time, Coro automatically closes the ticket and logs the event in the Activity Log.
Coro records all actions taken to generate and remediate tickets, as well as actions performed by admin users, in the Activity Log. Data recorded in the log can be used for audit and tracking purposes.
To view tickets in the Coro console, use the following:
| Location | Information shown |
|---|---|
| The Actionboard | Shows a summary and statistical information for the tickets generated for protected users, sorted by individual protection module, in a workspace. |
| The Ticket Log | Shows detailed information for tickets generated for all protected and protectable users in a workspace. |
| The Activity Log | Provides a record of ticket activity and the actions taken in a workspace. |
| The Global Actionboard | (Only for channel workspaces) Shows a summary of the tickets generated for protected users of a channel workspace and its descendant workspaces. |
| The Global Ticket Log | (Only for channel workspaces) Shows detailed information for tickets generated for all protected and protectable users in a channel workspace and its descendant workspaces. |
A ticket provides details to understand the cause, findings, duration, and context of an event. Admin users may need to take action on the ticket via the Ticket Log, depending on the ticket type and status. After tickets are selected for Admin remediation, Coro provides an option to close the ticket and consider it remediated. Unremediated tickets are closed automatically after a set period of time.
An admin user can re-open a closed ticket for further review as required.
Coro prioritizes protected users but also monitors the activity of protectable users who have not yet been added for protection. This allows organizations to observe patterns of behavior across their entire user base.
Tickets for protectable users are not represented in the Actionboard and appear in the Ticket Log for information only. Admin users are unable to perform actions to remediate tickets raised for protectable users, and Coro's automatic remediation mechanism ignores them. In addition, these tickets are not retained in the Activity Log for future reference, and there is no specified timeframe for their availability in the Coro console.
However, admin users can make decisions to add or adjust users and user groups to be protected. For more information, see Protected users and user groups.
Coro only generates tickets for protectable users when a workspace is in trial mode, or where an MSP admin user has enabled this option for channel and child workspaces. For more details on workspace types and statuses, see The Coro workspace.
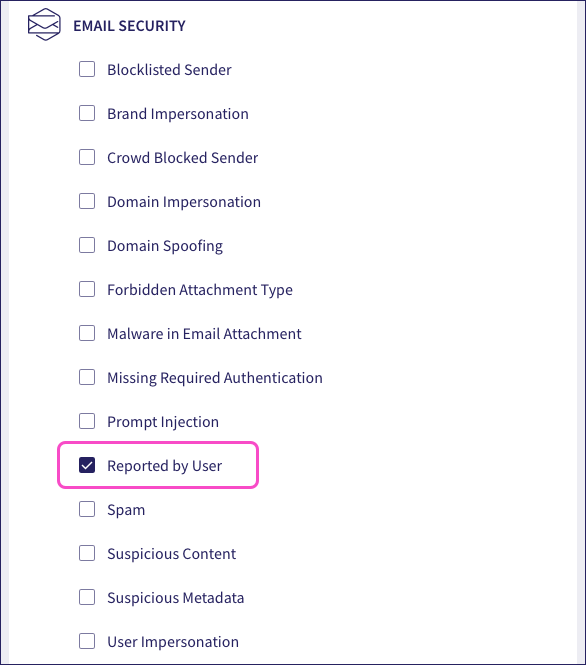
To stay informed of the ticket activity in your workspace, enable email notifications for raised tickets from the Notifications tab in your Coro console user profile. Admin users can enable or disable specific ticket notification settings in this tab to control which ticket types generate email alerts.
For example, to get a notification every time a user reports a phishing attempt through the Coro email feedback add-in, enable the Reported by user ticket notification option:
For more details, see Configuring notifications.