Overview of malware detection in cloud drives
Most types of files are susceptible to malicious code. In most cases, when a file containing such code is opened, the malware process is triggered, and can then infect an entire connected ecosystem. In other words, when a file with malware is uploaded to a cloud app, or downloaded from an app to a device, the risk escalates.
The majority of cloud applications natively offer some level of protection against these risks. Coro enhances malware detection and remediation across all supported cloud applications based on the specific level of protection offered by each. Coro searches for and removes files containing malware to prevent the spread of malware via cloud drives. The cloud applications currently monitored by Coro are:
- Box
- Dropbox
- Google Workspace
- Microsoft 365
- Salesforce
- Slack
Coro enhances malware detection and remediation across all cloud applications, based on what each application provides natively.
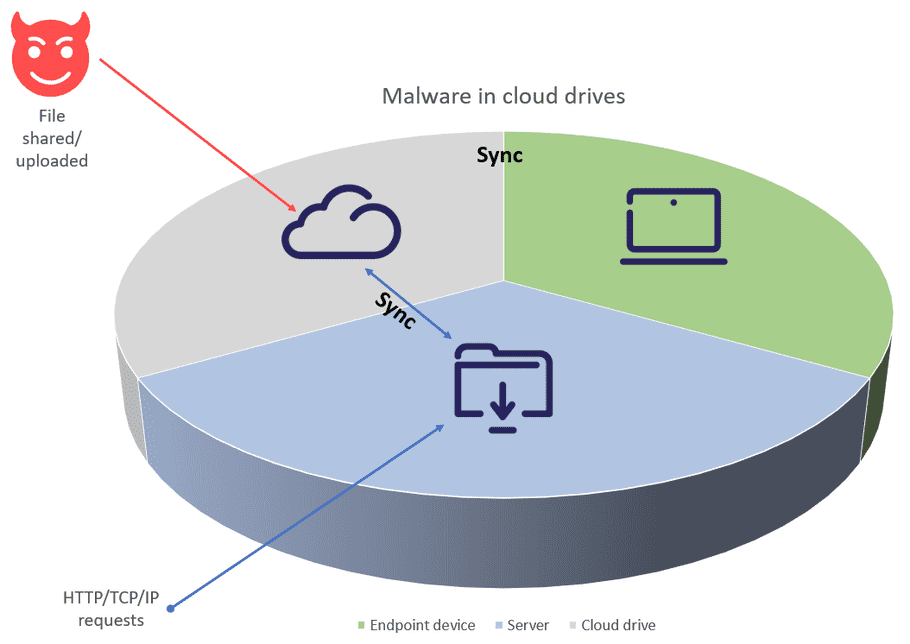
To prevent possible damage, Coro moves malicious files to a quarantine folder within the cloud application and raises a Malware in Cloud Drive ticket to record the event, classified as suggested for review. Admin users can then review the ticket details in the Coro console and determine if any action is necessary.
For further information about available ticket actions, see Malware in cloud drive ticket actions.
To learn more about malware detection and remediation in each cloud application, see the following articles: