Using Coro to protect against data loss and misuse
Organizations typically have regulatory, contractual, or ethical obligations to protect the data they hold about individuals.
To ensure the security and privacy of sensitive information, organizations must be able to demonstrate they have robust data protection measures in place. This includes the ability to manage access to sensitive information, to monitor data sharing and sending, and to store data securely.
What counts as sensitive information
Sensitive information refers to data that is confidential, private, or otherwise protected by law, policy, or contractual obligation, and requires special care in handling, storage, and access.
Sensitive information typically falls under one of the following types:
Personal data: Data that allows a reasonable inference of the identity of a person either directly or indirectly, such as full name, email address, passport number, or social security number. Personal data is covered by data protection regulations such as GDPR in Europe and state privacy law in the United States (for example, CCPA, NYPA, CPA).
Credit dard data: Data found on or associated with credit cards, such as card numbers, expiration dates, card verification values (CVVs), and cardholder names, that can be used to complete transactions or identify the cardholder.
Health data: Data about an individual's health or medical history that is collected, stored, used, or disclosed in the course of providing health care services, such as patient name, medical history, and health insurance details. Health data is protected by law under legislation such as the Health Insurance Portability and Accountability Act (HIPAA).
Non-public data: Personal financial data that is collected and stored by financial institutions, such as social security number, financial account numbers, home address, email address, income details, and employment data. Non-public data is protected by law under legislation such as the Gramm-Leach-Bliley Act (GLBA).
For information on the sensitive data that Coro recognizes, see Sensitive data recognized by Coro.
To learn more about the standards enforced for protecting sensitive information, see Compliance.
What are the threats
A number of threats can place your company's data at risk and it is important to be aware of them and take measures to limit their impact:
- Cyber attacks: Cybercriminals use a variety of methods to access sensitive information, such as hacking into systems, phishing scams, and malware.
- Human error: Mistakes, such as accidentally sending sensitive information to the wrong person, can result in data breaches.
- Insider threats: Employees and contractors may intentionally or unintentionally access or misuse sensitive information.
- Physical theft: Sensitive information can be stolen or lost through physical theft or misplacement of devices, such as laptops and smartphones.
How does Coro protect against such threats
Coro provides a number of features to protect sensitive information from unauthorized access and misuse, helping to reduce the risk of data breaches.
Use the Coro console to configure your protection features and to monitor the activity by protected and protectable users in your organization. Sign in to the Coro console to get started.
Coro provides the following:
Device monitoring
Coro remotely scans endpoint device drives for sensitive data. This feature enables organizations to proactively identify and monitor the storage of sensitive information on user's devices.
The remote scan feature scans specified drives and detects files that contain sensitive data.
To initiate a remote scan on a device:
From the sidebar, select Views > Devices:
Coro displays the Devices page:
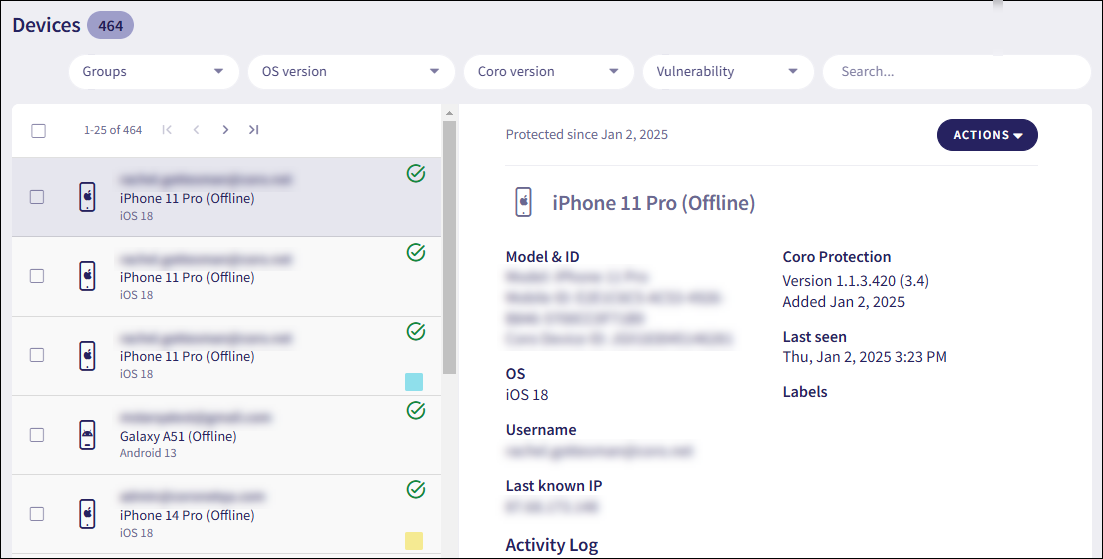
Select an active device (not marked Offline).
Select the Actions menu, then select Remote scan for sensitive data:
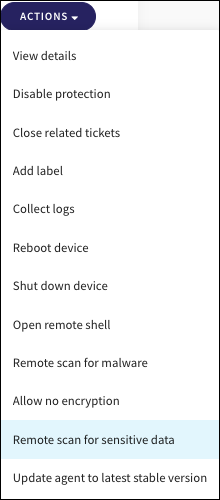
Admin users with sufficient permissions can also set up schedules to regularly scan groups of devices at defined intervals. To learn more, see Scheduling a sensitive data scan.
Coro scans each drive and creates a ticket listing files that may contain sensitive data. Admin users can use this information to review the findings and remotely encrypt the drive if needed.
To remotely encrypt a drive, go to the Endpoint Data Governance dashboard panel and select a ticket type:
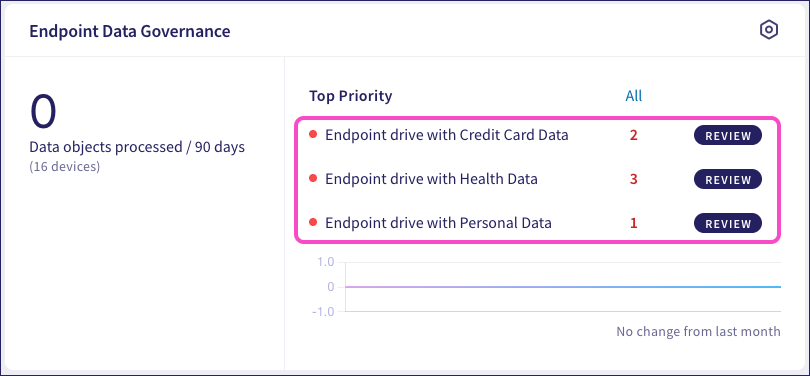
Coro displays the list of tickets where sensitive information was detected on a device. For each open ticket, review the findings and, if required, select Encrypt Drive from the Actions menu.
Permission management
On a day-to-day basis, an organization must balance legitimate data access needs by authorized employees against the risk of unauthorized access and sharing of sensitive information. To achieve this balance, Coro includes a permission management function where you define the access rights for individuals and groups of employees.
For more information on configuring permissions, see Setting access permissions.
Ticket management
In the Coro Actionboard, you can view a summary of activity across your workspace. To observe an analysis of data protection and monitoring activity, use the User Data Governance and Endpoint Data Governance panels:
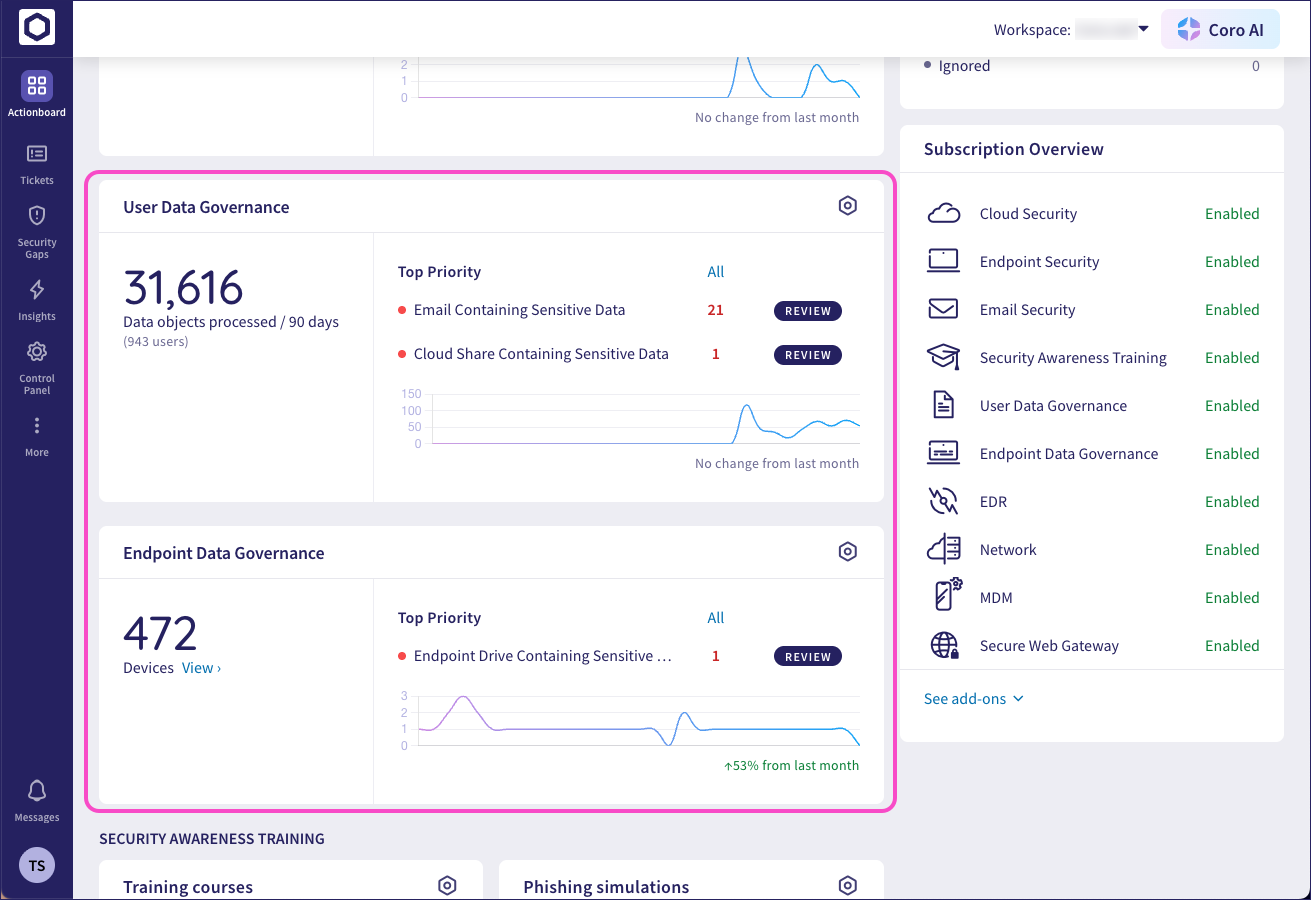
Through these panels you can identify and prioritize areas of concern, such as sensitive data exposure. This helps to ensure that security incidents are quickly addressed and resolved, and that sensitive information is being protected consistently and effectively. Use the information provided in the Actionboard as part of an overall strategy in raising awareness among your users of the importance of protecting sensitive information.
Coro creates data governance tickets when it detects sensitive information being used or shared by your protected users, or stored on your endpoint devices, in a manner that violates your permissions and monitoring policies. A ticket contains details of all sensitive data types detected during the event, whether the exposure was monitored or actively blocked, the user or device that triggered the ticket, and the context of the activity (such as the file name, when, its findings, and so on).
This information can be used to quickly and efficiently identify and respond to security incidents, such as unauthorized data sharing or data breaches. Additionally, tickets can be used to provide insight into the usage and sharing patterns of sensitive information, which can help organizations to identify data protection policies and procedures needing improvement.
Coro generates the following types of data monitoring tickets:
Tickets requiring manual review by admin users
Tickets that trigger a high level of suspicion or have a high potential of direct violation of regulatory requirements are marked as requiring review by admin users. These tickets often contain very sensitive information and it is important that action is taken.
The review period is limited to 10 days, after which a ticket is automatically closed and logged. This ensures that all potential security incidents or violations are captured and addressed promptly.
Eamples of the data types identified in this type of ticket include:
- Credit Card Data: Detection of a credit card number
- Health Data: Medical image or scan
- Non-Public Data: SSN and bank statement
- Personal Data: US passport and person name
Ticket review and remediaton options depend on the ticket type, and are listed in full in User Data Governance ticket types and Endpoint Data Governance ticket types.
Typical options include:
- Close ticket: Close the ticket immediately as reviewed.
- Suspend user from all cloud apps: Temporarily suspend the user from all Coro-protected cloud applications.
- Suspend user from <cloud application>: Temporarily suspend the user from their account in the specific named cloud application.
- Contact User: Send a direct message to the user that has violated the policy.
- Add to Data Governance Permissions: Authorize the user to access and share the sensitive data type identified in the ticket. Coro adds an access permission entry for the user.
- Remove exposing sharing: Remove all shares with people from outside of your organization.
Coro includes additional actions in tickets relating to blocked sent emails that potentially violated a sensitive data policy. In this case, admin users can allow or delete the offending email after the threat has been assessed. For more details, see Configuring data governance settings.
Automatically closed tickets
These are tickets containing sensitive information but do not require manual review by admin users.
Such tickets are included in the Coro console ticket log for audit, monitoring, analysis, and to satisfy regulatory compliance requirements. They are typically triggered automatically by events such as the detection of sensitive information in an email, file, or file sharing.
Examples of the data types identified in this type of ticket include:
- Personal Data: IP and MAC address
- Non Public Data: Monthly payment (financial content) and email address
- Health Data: Medical Records Number (MRN)
Ticket review and remediaton options depend on the ticket type, and are listed in full in User Data Governance ticket types and Endpoint Data Governance ticket types.
Typical review options include:
- Re-open: Reopen this closed ticket for manual review.
- Suspend user from all cloud apps: Temporarily suspend the user from all Coro-protected cloud applications.
- Suspend user from <cloud application>: Temporarily suspend the user from their account in the specific named cloud application.
- Contact user: Send a direct message that the user that violated the policy.
- Un-log and remove from audit reports: Exclude this ticket from the log if the ticket details constitute a false positive.
Protectable user sensitive data monitoring
Coro monitors protectable user activity across your workspace in addition to your defined protected users.
By monitoring potential data violations by protectable users, Coro enables organizations to track and document incidents in order to identify patterns or trends in user behavior. Such events might indicate systemic issues or vulnerabilities, and an organization can then mitigate the risk and amend policy and user protection accordingly.
User monitoring
Effective data monitoring and detection controls help prevent unauthorized access to sensitive information. Data governance technologies enhance security by detecting sensitive data and preventing accidental exposure.
For more information on configuring data monitoring, see Configuring monitoring settings.
To learn more about the Coro modules used in this guide, see User Data Governance and Endpoint Data Governance.