Configuring monitoring settings
Strong data monitoring and detection controls are necessary to prevent sensitive information from being shared with, or accessed by, unauthorized users. One way to achieve this is by detecting sensitive information through the use of technologies for data governance.
Coro's data governance capability monitors in real-time and scans all outgoing communications for sensitive information, flagging to the administrator any instances where such information is sent to an unauthorized user or group of users.
Coro recommends monitoring the information types critical to your business or industry to achieve optimal results. For example:
- A company providing accounting services might collect personal customer information to effectively deliver its services. In this case, Coro recommends monitoring for PII and PCI .
- A company providing nursing services to patients would need to collect personal and health information as part of the service. Coro recommends monitoring for PHI , PII , and PCI .
- Automotive agency that provides loan services collects personal and financial information. Coro recommends monitoring NPI as the agency must comply with GLBA regulations.
note
When a new workspace is created, all User Data Governance options are disabled by default. Permission settings only take effect after monitoring is enabled for one or more User Data Governance options.
To configure data monitoring:
-
Log into the Coro console
and select
Control Panel
from the toolbar.

- Select User Data Governance .
-
Select the
Monitoring
tab:
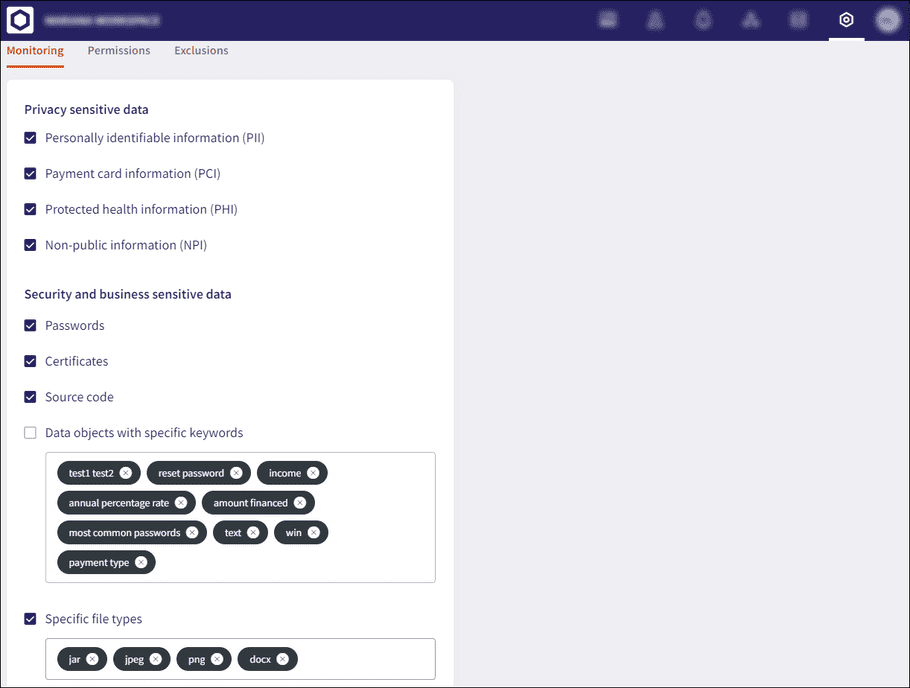
The Monitoring tab consists of the following sections:
Privacy sensitive data
The Privacy sensitive data section allows you to specify the types of sensitive data to monitor (on access and exposure) within email and shared cloud drive data. The following Privacy sensitive data can be monitored:
- Personally identifiable information (PII)
- Protected health information (PHI)
- Payment card information (PCI)
- Non-public information (NPI)

Enable or disable each option based on your needs. Coro recommends enabling information types according to the following table of industry sectors and typical regulatory needs:
Caution
This list is non-exhaustive, nor warrantied in any way, and is included for guidance only.
| Sector | Regulation | Data Type | Comment |
|---|---|---|---|
| Accounting Services | SOX, State Privacy , ISO 27001 | PII | |
| Agriculture & Food | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| Automotive | State Privacy , GLBA | NPI | |
| Business & Marketing | State Privacy | PII | |
| Business Services | State Privacy | PII | |
| Colleges & Universities | State Privacy , GLBA, ISO 27001, FERPA | NPI & PII | |
| Construction | State Privacy | PII | |
| Consulting | State Privacy | PII | |
| Consumer Services | State Privacy | PII | |
| Education | State Privacy , FERPA | PII | |
| Energy, Utilities & Waste | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| Finance | State Privacy, GLBA, SOX, ISO 27001 | NPI | |
| Government | FISMA, State Privacy | PII | |
| Health | HIPAA, State Privacy | PHI & PII & PCI | |
| Holding Companies & Conglomerates | State Privacy | PII | |
| Hospitality | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| HR | State Privacy | PII | |
| Insurance | State Privacy, GLBA, SOX, ISO 27001 | NPI | |
| IT services | State Privacy | PII & PCI | |
| Law Firms & Legal Services | State Privacy | PII | |
| Manufacturing | State Privacy | PII | |
| Media & Internet | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| Minerals & Mining | State Privacy | PII | |
| Organizations | State Privacy | PII | |
| Pharma | HIPAA, State Privacy | PHI & PII & PCI | |
| Real Estate | State Privacy | PII | |
| Retail | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| Software | State Privacy , SOC 2 | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| Telecommunications | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
| Transportation | State Privacy | PII & PCI | PCI is relevant for establishment that receive credit card payments |
Security and business sensitive data
The Security and business sensitive data section allows you to enable monitoring of additional data types that are important to your individual organization.
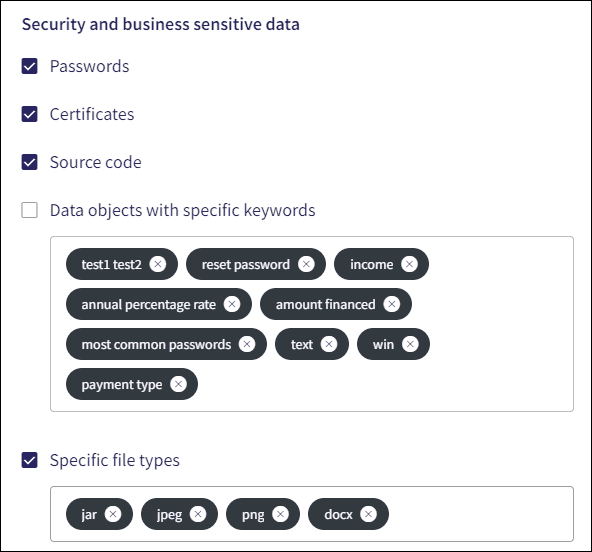
The following Security and business sensitive data can be monitored:
- Passwords : Monitors for potential password exposure.
- Certificates : Monitors security certificate files, such as SSL certificates, which are used to establish secure connections between web servers and browsers.
- Source code : Monitors source code files (such as * .md, * .yaml, * .sh, * .slx, * .mdl, * .m, and * .json).
- Data objects with specific keywords : Identifies and matches defined keywords in email and shared file content, including subject, body, and attachment filenames. Keyword matching is case validated, and Coro removes duplicate keywords, keeping only the lowercase version. Email domains and sender/recipient names are not used for keyword matching.
- Specific file types : Monitors files added as email attachments and in shared drive content that match one of the defined file extentions.