Endpoint Security
What level of Windows User Account Control (UAC) must be enabled for Coro to enforce a UAC Notification Missing policy?
Coro enforces the UAC Notification Missing policy when Windows User Account Control settings are set to:
- Default
- Low
- Medium
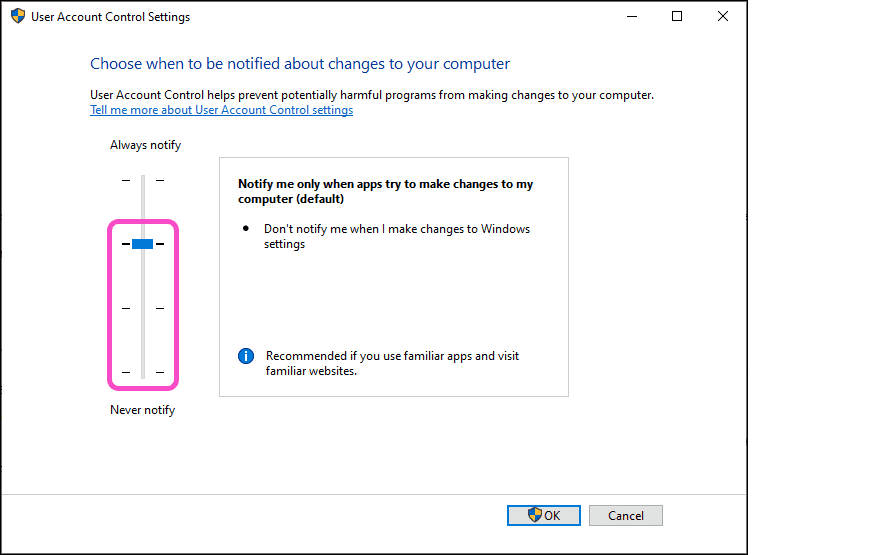
For more information, see UAC Notification.
If an admin user configures a Remote Password & Session Locking policy on my workspace, how does the Coro agent detect how old my existing password is?
The Coro agent is capable of extracting user profile information directly from your device to determine the age of your existing password.
For more information, see Remote password and session locking.
Does Coro have the capability to auto-enforce hard drive encryption without allowing the end user to disable it?
While Coro can perform hard drive encryption, there is no method to ensure this functionality is auto-enforced. It is a manual remediation action performed by an admin user in the Coro console, either from the Devices page or from the Ticket Log.
For more information, see Encrypting endpoint device drives
For specific devices, how far back does Coro log recently signed-in users?
Coro maintains a record of the previous three signed-in users.
If I am running another Antivirus (AV) product, and it detects and quarantines a potentially malicious file, will Coro still detect this already quarantined file?
No, if a potentially malicious file has already been quarantined by another AV product, Coro does not detect it.
Important
Coro advises against running another AV product in addition to Coro. For more details, see Running other antivirus software with Coro.
Where are encryption keys stored?
Encryption keys are stored on both the device (by BitLocker) and on the Coro servers.
Additionally, BitLocker recovery keys are displayed for all encrypted drives on a device. The recovery key is displayed within the expanded Drives section of the affected device on the Devices and Global devices pages:
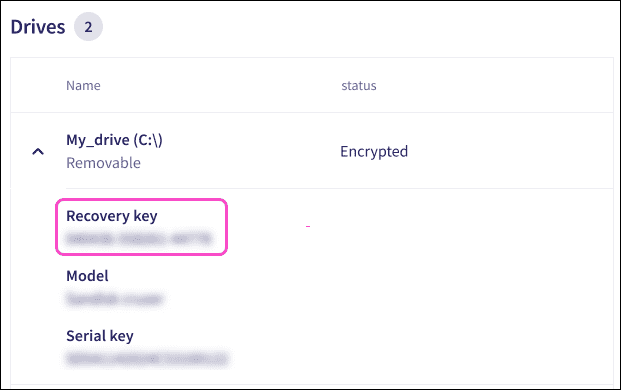
For more information, see Encrypting endpoint device drives
When an employee or contractor leaves the company, can an admin user remove their endpoint device from Coro protection?
Yes, an admin user with sufficient permissions can disable protection for a device in the Coro console and then remove the device from Coro monitoring.
To disable protection on endpoint devices as an admin user:
- Access the Devices page.
-
Locate and select the required device, then select
Actions > Disable protection
.
After the set heartbeat interval elapses, Coro disables protection on the devices, allowing the user to uninstall Coro.
Does Coro detect data governance issues within Computer-Aided Design (CAD) files?
No, Coro does not detect data governance issues within CAD files.
Does Coro remediate existing tickets if you reactivate your workspace through a trial extension or subscription purchase?
No. Coro does not remediate tickets retroactively. Coro monitors, generates, and remediates tickets only while the workspace is active. If the workspace becomes inactive before remediation occurs, Coro does not take action on existing tickets, even if the workspace is later reactivated through a trial extension or subscription purchase.
Is it safe to use other installed antivirus (AV) products alongside Coro?
Running other AV software alongside Coro is discouraged because it can cause performance conflicts.
For more information, see Running other antivirus software with Coro.
How does Coro resolve malicious software detected on an endpoint or device?
Coro monitors all processes and terminates them if suspicious behavior is detected.
When Advanced Threat Control is enabled, Coro monitors active processes for known and potential threats, and blocks processes (that are not explicitly allowlisted) that exhibit suspicious behavior.
How do I add a process to the Allow/Block list?
The Endpoint Security and EDR module Allow/Block lists allow you to manage your processes by allowing those that are safe to be accessed.
For more information, see:
Does Coro support Linux endpoint protection?
Yes. For more information, see Deploying Coro on Linux devices.
Does Coro provide protection for Chromebooks as endpoint devices?
No.
Can Coro detect malicious scripts embedded in Word, PDF, PPT, and other documents?
Yes.
What gets backed up within secure shadow backup snapshots?
The entire hard drive of the device. Windows uses the Volume Shadow Copy Service (VSS) to perform the backup.
For further information, see Secured shadow backups.
Where are secure shadow backup snapshots stored?
Windows uses the Volume Shadow Copy Service (VSS) to store secure shadow backup snapshots in the hidden System Volume Information folder. You can manage these backups through the device’s system protection settings.
For further information, see Using VSS backup protection on your Windows endpoints.
How do I restore secure shadow backup snapshots?
For instructions on how to restore secure shadow backup snapshots, see Restoring secure shadow backup snapshots.
What does the USB Lockdown device posture policy do?
The USB Lockdown device posture policy blocks mass storage devices on macOS devices. For Windows devices, this extends to block both mass storage and other USB-connected devices, such as media players and smartphones.
For more information, see Endpoint device USB Lockdown.
I'm traveling outside my usual Wi-Fi network area, and when I try to connect my device to a public Wi-Fi network, the Coro Agent displays a notification: "Connection to <network> is not permitted by your administrator". What should I do?
Your device has a Wi-Fi connection policy enabled. Wi-Fi connection policies prevent devices from connecting to public Wi-Fi networks, only allowing connections to secure, password protected networks.
Admin users can allow the connection by ensuring no device labels that enforce this Wi-Fi connection policy are assigned to your device. Alternatively, they can remove the Wi-Fi connection policy from all devices.
Your device must first connect to a secure network to update its policy. After the policy update, your device is able to connect to public Wi-Fi networks.
note
The time taken for the Wi-Fi connection policy to update depends on your workspace's heartbeat interval.
For more information, see Configuring Wi-Fi connectivity policies.
Does the "Approve This File" and "Exclude Folder from Malware Scan" ticket action apply only to the specific device, or does it extend to all devices within the workspace?
The Approve This File and Exclude Folder from Malware Scan actions extend to all devices within the workspace.
How do Coro password policies interact with existing Active Directory password policies?
If you set password policies via Active Directory, then you do not need to configure password policies in Coro. Active Directory password policies override Coro password policies.
When running a malware and ransomware scan on an endpoint device, I do not see the results of the scan in the audit log. However, the device itself displays a notification saying admin has requested the scan. Is there any additional place to view more information on the scan results?
If the scan detects malware or ransomware on a device, corresponding tickets are created and are viewable in the ticket log.
For further information, see Ticket types for Endpoint Security.
How can I make an exception for a process or file flagged by Coro as malicious?
Coro groups related processes into process groups (collections of processes that share a common origin or behavior) when it generates infected process tickets. If Coro creates an Infected process ticket, you can select Approve process group from the ticket actions menu. When an admin user with sufficient permission approves the process group, the Coro Agent applies the approval across all devices in the same workspace. Coro also considers identical process groups safe and no longer terminates them.
If Coro creates a Malware on endpoint ticket, you can either select Approve this file or Exclude folder from malware scan from the ticket actions menu:
- Approve this file : The Agent removes the file from quarantine (if applicable) and applies the approval to all devices in the workspace. Identical files are not quarantined in the future.
- Exclude folder from malware scan : Coro skips the specified folder in future malware and ransomware scans.
For further information, see Ticket types for Endpoint Security.
Does Coro's antivirus (AV) have a ransomware rollback feature?
No, Coro's AV does not have a ransomware rollback feature. However, admin users with sufficient permissions can enable Secured Shadow Backups on Windows devices. When enabled, Coro enforces backup snapshots every four hours and blocks processes that exhibit risks to the backup. The Coro Agent utilizes the Windows Volume Shadow Copy Service (VSS) mechanism to automatically save a snapshot of your device's files.
Does Coro automatically retrieve and store device encryption recovery keys, even if Coro did not initiate the encryption?
Yes, Coro automatically retrieves and stores device encryption recovery keys, even if Coro did not initiate the encryption.
note
Coro supports this functionality for Windows devices only.
Does the USB lockdown device posture policy prevent mobile devices from charging?
No, mobile devices can still charge while a USB lockdown device posture policy is active on the device. A USB lockdown device posture policy can block:
- Portable devices : (Windows devices) USB-connected mobile devices.
- Mass storage devices : (Windows and macOS devices) USB flash drives and external hard drives.
For more information, see USB Lockdown.
Does enforcing BitLocker encryption through Coro encrypt the entire disk?
Yes, Coro encrypts the entire disk drive by default. BitLocker encryption through Coro is applied per drive. The primary system drive must be encrypted first. If your device has multiple drives, you have the option to encrypt each one individually.
For more information, see Encrypting endpoint device drives.
Will I receive a notification if a sensitive data scan is missed because the endpoint device was offline?
If a device is offline during a scheduled scan, the scan automatically starts when the device reconnects to Coro.
For more information, see Scheduling a sensitive data scan.
Can an admin user enforce the Remote Password & Session Locking policy, or does it only detect non-compliance?
Coro enforces Remote Password & Session Locking policies.
Coro immediately implements screen lockout policies and applies password policies when:
- The user logs off the device.
- The device restarts.
- The device enters screen lock.
What do the "Lockout duration" and "Lockout threshold" attributes mean in a screen lockout policy?
- Lockout duration : Specifies how long a user's screen remains locked after the lockout is activated (maximum value 3 hours.)
- Lockout threshold : (attempts): Specifies the number of consecutive failed login attempts that triggers a screen lockout (maximum value 10).
note
You must set both parameters to configure a screen lockout policy.
For further information, see Remote password and session locking.
Can I schedule antivirus scans?
Coro is designed to provide real-time antivirus scanning for continuous protection of your endpoint devices. Consequently, Coro does not provide the ability to selectively schedule antivirus scans. The Coro Agent operates in real-time, scanning files whenever a user or process attempts to access them. If a file is identified as malicious, Coro quarantines it. Coro also detects and terminates potentially malicious processes.
Advanced threat control (ATC) provides an additional layer of real-time monitoring by analyzing processes as they run/execute for known and potential threats. ATC blocks any processes that exhibit suspicious behavior.
Does the USB Lockdown policy prevent external webcams and printers from functioning?
No, the USB Lockdown policy only blocks:
- Portable devices : (Windows devices) USB-connected mobile devices.
- Mass storage devices : (Windows and macOS devices) USB flash drives and external hard drives.
For further information, see Endpoint device USB Lockdown.
Where are quarantined malicious files stored on an endpoint device by Coro?
When Coro quarantines a malicious file on a device, it moves the file to the following location:
-
Windows:
C:\ProgramData\CoroAgent1SRV\p\BD\quar -
macOS:
/Library/Coro/RunShield/BD/quar
Can Coro encrypt devices running Windows Home edition?
No. Windows Home editions include only a limited version of BitLocker. Coro requires the full version of BitLocker, which is available only in Windows Professional, Enterprise, or Education editions.
Is there a limit or recommendation for the number of endpoint devices that can be protected within a single Coro workspace?
No.
Can I access a device remotely from the Coro console?
Yes, select Open remote shell from any online device listed on the Devices or Global devices page. This action starts a command prompt on the device, allowing you to run commands remotely.
For more information, see Device information and options
What does the Disable protection endpoint device action do?
The Disable protection action deactivates Coro protection on a device. To re-enable Coro protection, go to the Activity Log, find the related entry, and select UNDO.
What happens if a Remote Password & Session Locking policy is set and the user exceeds the password expiration time limit?
After your password expires, the operating system typically displays a prompt for the user to update it during their next sign in.
What is the difference between the Wi-Fi Connection posture policy and the Wi-Fi Phishing add-on?
The Wi-Fi Connection policy blocks access to public wireless networks for specific devices or groups. The Wi-Fi Phishing add-on integrates with the Endpoint Security module to detect potentially malicious wireless network connections, such as those used in Man-in-the-Middle attacks that can steal or manipulate data.
What does the Wi-Fi Connection policy consider an encrypted network?
Coro considers a network encrypted if it uses WPA or a higher standard.
Why can I apply non-Windows device labels to Coro features designed for Windows devices, such as Secured Shadow Backups?
Coro applies policies to all supported devices linked to a label, regardless of operating system. Features activate only on devices that support them.
If I reimage a device by duplicating a Coro-installed hard drive or installation image, will it have the same device ID as the original?
Yes.
Can Coro render an endpoint device unusable through encryption?
No. Coro uses built-in tools (BitLocker on Windows and FileVault on macOS) to enforce encryption on a device’s drives. This protects data in case the device is lost or stolen, but does not make the device unusable.
Can the Endpoint Security module exclude folders from monitoring?
Yes. For more information, see Endpoint Security allowlist and blocklist.
If I delete an unencrypted endpoint drive policy, does Coro continue to generate tickets for detected unencrypted device drives?
When you delete an unencrypted endpoint drive policy for a specific group of devices (specified by a device label), Coro no longer creates tickets for unencrypted endpoint drives assigned to that device label.
Can I use wildcard characters in the Endpoint Security allowlists and blocklists?
While Coro does not support wildcard characters, the Windows and macOS Agents support environment variables. Use these variables in place of specific file or folder paths to simplify policy configuration and reduce the number of manual entries.
For more information, see Using environment variables.
Can I disable BitLocker on my Windows device from the Coro console?
No. Coro does not provide an option to disable BitLocker itself. You must disable it directly in Windows.
For more information, refer to Microsoft's BitLocker documentation (https://learn.microsoft.com/en-us/powershell/module/bitlocker/?view=windowsserver2025-ps).
Can I allowlist specific USB devices?
No. The USB Lockdown device posture policy blocks mass storage devices on macOS devices. For Windows devices, Coro extends this functionality to block both mass storage and other USB-connected devices, such as media players and smartphones. Admin users can apply this policy to groups of devices using device labels.
For more information, see USB Lockdown.
Can Coro detect whether the Agent was installed on a company-managed device or personal (BYOD) device?
No. Coro does not automatically distinguish between company-owned and personal (BYOD) devices. However, admin users can view device names on the Devices page and manually disable protection on unauthorized devices. To maintain control, Coro recommends deploying the agent through a remote monitoring and management (RMM) tool. This approach enables admin users to control exactly which devices receive the Agent.
Do endpoint device actions take effect immediately or only after the next heartbeat interval?
Device actions take effect after the device checks in at its next heartbeat interval.
Can Coro scan password protected files?
No.
Can I migrate an endpoint device from one workspace to another?
No. The Coro installation file includes a workspace-specific activation key. To move a device to a different workspace, you must uninstall Coro from the device and reinstall it using the installer from the correct workspace.
Does Coro detect partially encrypted drives?
Yes. Coro detects a drive as encrypted even if only the used space is encrypted. However, Coro does not indicate whether the encryption is full or partial.
In what format must I enter network names in the Wi-Fi Connection device posture policy?
Enter each wireless network name as its SSID.
Important
SSIDs are case-sensitive.
For more information, see Wi-Fi Connection.
Does Coro’s Wi-Fi Phishing protection detect attacks involving fake networks that use the same SSID as legitimate ones?
Yes.
For more information, see Wi-Fi Phishing.
Does Coro display the progress of a malware scan on a device?
No, Coro does not show real-time scan progress. However, Coro logs the scan initiation in the Activity Log and notifies the end user in the Agent app when the scan starts and completes.
Does Coro set a storage threshold for Volume Shadow Copy Service (VSS) automatic backup snapshots?
Coro does not control VSS storage settings; Windows manages them. Coro recommends setting the threshold to 15–20% of the total drive capacity.
note
Coro automatically sets the threshold to 10% if it detects the value is below 9%.
If I replace my current device with a new one, does Coro automatically remove the old device from my workspace?
No. When you start using a new device, Coro treats it as an additional device rather than a replacement. Coro does not automatically remove the old device from your workspace. To remove the old device, go to the Devices page, open the action menu for that device, and select Actions > Disable protection.
For more information, see:
Does the Wi-Fi Phishing add-on alert a user when they try to join a malicious wireless network?
Yes. When a user attempts to connect to a suspicious wireless network, Coro displays a notification on the device. Coro also creates a WiFi Phishing ticket for the admin user to review.
Which macOS setting does the Gatekeeper Disabled device policy monitor?
Coro monitors the Allow applications downloaded from setting on macOS devices. If this setting is set to Anywhere, Coro creates a Gatekeeper Disabled ticket.
How does Coro isolate a device from the network?
When Coro isolates a device, it uses the device’s local firewall to block all inbound and outbound network communication. The only connection that remains active is to Coro’s servers, allowing Coro to continue managing the device and perform actions remotely.
Can Coro detect malicious files inside a container?
Yes, Coro detects malicious files inside containers (archives such as ZIP, RAR, other compressed formats, or self-extracting installers like .exe files).
For more information, see Quarantine infected containers.
Can Coro encrypt macOS endpoint device drives?
Yes, Coro supports encryption on macOS internal drives and external Apple File System drives.
Can Coro remove a quarantined malware-infected file from a device?
No, Coro quarantines the infected file to prevent it from causing harm but does not delete it from the device.
Does Coro protect Volume Shadow Copy Service (VSS) backups from ransomware?
Yes, Coro actively protects VSS backups by enforcing automatic snapshots every four hours and blocking processes that pose a risk to those backups.
If I create two Wi-Fi Connection policies, one configured to Deny connection to all unencrypted networks and the other configured to Allow connection to specific networks for a particular open wireless network, does Coro allow my device to connect to the open wireless network?
Yes. When both policies are in place, Coro allows the device to connect to the specified open (unencrypted) wireless network. The allow rule takes precedence over the restriction on unencrypted wireless networks.