Cloud app security
Does the Coro Security Platform offer Multi-Factor Authentication (MFA)?
Yes, you can enable MFA from the console. In addition, all individually supported cloud applications support MFA.
Can Coro control accessibility to Microsoft Sharepoint using IP restrictions?
Yes, Coro can control accessibility to Microsoft Sharepoint using Microsoft 365 Access Permissions.
For more information, see Setting permissions for your cloud applications.
Why does the Activity Log of a Malware in Cloud Drive ticket indicate that remediation of a suspected malicious file failed?
A failed remediation activity within a Malware in Cloud Drive ticket indicates that the file was remediated by the native cloud application.
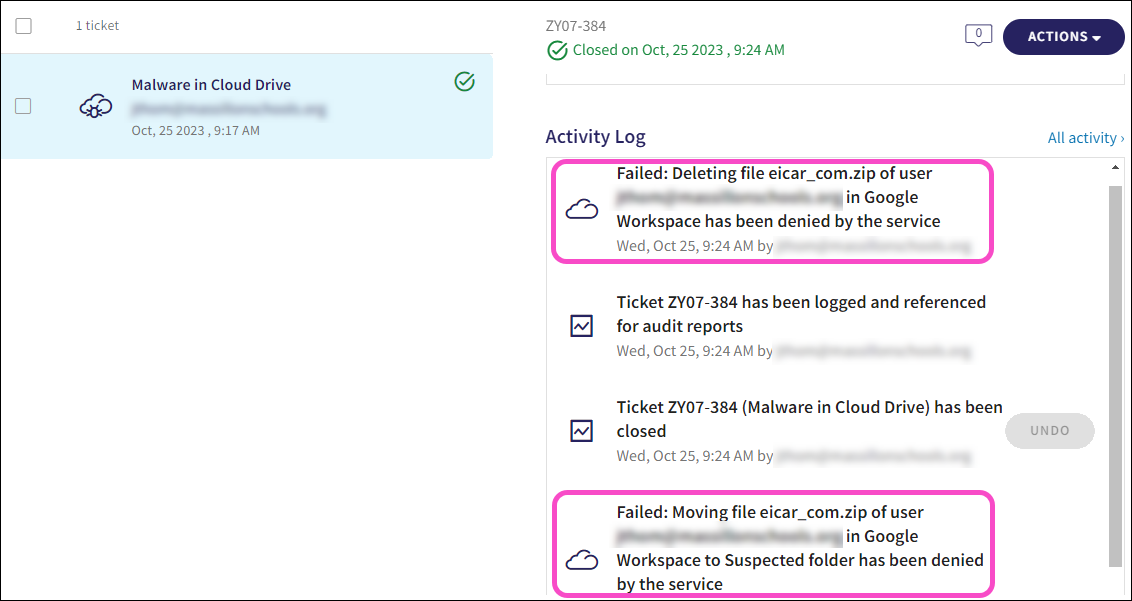
For more information, see Malware detection in cloud drives.
How does Coro's malware detection and execution process work?
Coro enhances malware detection and remediation across all monitored cloud applications, based on what each application provides natively.
To prevent possible damage, Coro moves malicious files to a quarantine folder within the cloud application and raises a Malware in Cloud Drive ticket to record the event, classified as suggested for review. Admin users can then review the ticket details in the Coro console and determine if any action is necessary.
Coro does not clean infected files.
For more information, see Malware detection in cloud drives.
What monitoring and remediation functionality does Coro’s Salesforce cloud integration provide?
Coro provides the following monitoring and remediation functionality for Salesforce integration:
- Mass data downloads
- Mass data deletions
- Abnormal admin activity
- Suspected identity compromise
- Suspected bot attacks
- Access permissions violations
- Malware scanning
For more information, see Cloud Security tickets.
When a user is added/removed from O365/AzureAD, does the process happen in real time?
Coro synchronizes protected users and groups automatically at 4:00 AM (UTC) each day. Admin users with sufficient permissions can manually trigger synchronization by selecting Synchronize users from cloud apps now from the Protected Users or Protected Groups tab on the Users page, accessible via (Control Panel > Users):
For more information, see Adding users and user groups for protection.
Can Coro protect user accounts that do not have enabled email inboxes, or are restricted from receiving external emails?
Yes, although these user accounts must be added to protection manually.
Coro identifies cloud application users by their email address, and automatically detects and synchronizes users in specified groups (or all users) from a connected cloud application. If a user account is based on an email address, but their inbox is not enabled to receive external email, Coro is unable to include them during the synchronization process. Adding these accounts manually, either individually or by uploading a user list, means Coro can add them for protection together with synchronized user accounts.
What is flagged as Abnormal Admin Activity?
Coro detects identity compromise suspicions for regular and administrative accounts by analyzing data from all customers, specific customers, and specific users behind a ticket, creating normative behavior models, and detecting anomalies from these models. The models range from simple statistical anomaly models to more complex models that cross-correlate data from various sensors throughout the system to uncover evidence of abnormal behavior.
For example, Coro can detect an admin user’s suspicious activity based on the account having been active on different IP addresses in close time proximity.
For more information, see Abnormal admin activity.
Can I view audit reports from the Coro console?
Although you don't have the ability to generate audit reports directly from the Coro console, quarterly threat reports are provided to Coro customers.
What user behaviors does Coro monitor and track for anomalies?
Coro identifies anomalies such as abnormal admin activity, access permission violations, and suspected identity compromise.
For more information, see Ticket types for Cloud Security.
What protection is offered to O365 users that are not using Outlook?
Support is provided for all protection except email-based detections.
Does Coro provide granularity regarding which folders are being affected by a mass deletion event or malware infection?
Yes, Coro displays the full file path of the affected file. This applies to both local and cloud folders (1Drive, Sharepoint, Google-Drive, Dropbox etc.)
How does Coro identify Suspected Identity Compromise?
Coro calculates the login frequency threshold of cloud application users from various locations.
Where users log in to cloud applications from different geographic locations, Coro evaluates the login frequency across each location. Coro generates a Suspected Identity Compromise ticket when the login frequency from a particular location sits below a predetermined detection threshold.
For more information, see Suspected identity compromise.
Are file locations included in Google Workspace related tickets?
No, file locations are not included in Google Workspace related tickets.
What detection and remediation functionality does Box offer?
By default, Box does not detect malware, but it offers a paid feature, Box Shield, which detects malware in Box storage and restricts downloading and sharing.
For more information, see Box detection and remediation.
What detection and remediation functionality does Dropbox offer?
Dropbox does not support malware detection.
For more information, see Dropbox detection and remediation
Does Coro detect mass data downloads/deletions on Salesforce?
Yes, mass data downloads/deletions are detected on Salesforce. With mass data downloads, Coro detects when a large amount of smaller files are exported from Salesforce.
For more information on mass data downloads/deletions, see Cloud Security tickets.
What detection and remediation functionality does Salesforce offer?
Salesforce does not provide malware detection in its repositories.
For more information, see Salesforce detection and remediation.
What monitoring and protection does Coro provide for Salesforce?
Coro Salesforce protection includes malware/ransomware detection and remediation, as well as user account access and activity control.
For more information, see Salesforce detection and remediation.
What detection and remediation functionality does Slack offer?
Slack offers limited malware detection. Slack protection features include:
Scanning files during upload to a Slack channel and halting the upload process if Slack detects malware.
Performing periodic offline scans of previously uploaded files to ensure ongoing security.
For more information, see Slack detection and remediation.
What monitoring and protection does Coro provide for Slack?
Coro protects Slack user account access while also monitoring and controlling user activity.
For more information, see Slack detection and remediation.
What detection and remediation functionality does Microsoft 365 offer?
Microsoft 365 offers limited malware detection, typically occurring 15 minutes or more after a file download. If a scan identifies a file as malicious, the system restricts its sharing capabilities, and a warning appears in the OneDrive interface, indicating the file cannot be shared. In addition, there are file types that Microsoft 365 does not detect.
For more information, see Microsoft 365 detection and remediation.
What detection and remediation functionality does Google Workspace offer?
Google Workspace offers limited malware detection, initiating scans only during file downloads, including those downloaded through the Google Download API. If a user attempts to download a malicious file, the Google Workspace interface actively alerts them with a warning. Google Workspace does not support malware detection or remediation directly on the cloud drive.
For more information, see Google Workspace detection and remediation.
What Box subscription plan is required to connect Box to Coro?
An Enterprise Box subscription plan is required to connect Box to Coro.
Does Coro scan SharePoint and OneDrive for malicious executable files (EXE, MSI, etc.)?
Yes, Coro scans all file types for malware. The entire file's content is checked for malware/ransomware.
Can Coro alerts be delivered to a Slack channel?
Yes, an email rule can be created to forward emails from Coro notifications to a Slack channel.
What is the difference between a Suspected identity compromise and an Access permission violation ticket?
Suspected identity Compromise tickets relate to suspect log-ins and abnormal user activity. Access permission violation tickets relate to someone successfully signing in from a different country.
To set up geofencing permissions:
Navigate to Settings > Cloud Security > Access Permissions.
Select New Permissions.
Select All Users or Specific Groups.
The New Access Permissions dialog is displayed.
From the Allow access from dropdown, select Country.
Select the allowed countries.
From the Automatic remediation dropdown, select an option.
The following remediation options are available when an Access Permissions policy is created:
None: No remediation steps are required.
Suspend: The user account is automatically suspended.
Sign in: The user must re-enter their credentials.
Select Save Permissions.
If geofencing is not set up, Coro creates a Suspected identity compromise ticket.
For more information, see Setting permissions for your cloud applications.
Can an admin user approve an Access Permission Violation ticket when automatic remediation is enforced for sign-in activities? For example, permission is granted to all users in the United States only, but a user then travels to another country and cannot log in.
An admin user can undo the automatic remediation activity as follows:
Locate the automatic remediation activity in the Activity Log inside the Access Permission Violation ticket.
Select UNDO.
Add the user to a specific group.
Allow country-level access permissions to the specific group (Control Panel > Cloud Security > Access Permissions)
For more information, see Setting permissions for your cloud applications.
Is it safe for Coro to use my Microsoft 365 or Google Workspace global admin account in order to connect to Coro?
Yes, direct Oauth authentication is performed with the cloud app. OAuth permits Coro to use only the information that the user consents to share. OAuth also protects your passwords from being compromised.
For more information, see Sign in to the Coro Console.
Are the contents of slack messages monitored and flagged for data governance violations?
No, the contents of slack messages are not monitored and flagged for data governance violations.
For more information, see Slack detection and remediation.
Can Coro detect when a file has been deleted from a cloud drive?
Yes, Coro detects mass file deletions in cloud drives, and creates a Mass Data Deletion ticket.
For more information, see Mass data deletion.
Does Coro indicate which folder was affected when a file is deleted from a cloud drive folder?
When larger files are deleted from cloud drives, Coro records and organizes them by folder in a Mass Data Deletion ticket.
For more information, see Mass data deletion.
Can a prospect initiate a trial if they use M365 while hosting their Active Directory (AD) in-house on a local virtual machine? For the purposes of the Coro trial, would this setup be classified as on-premises?
Coro integrates directly with M365. They can connect a trial, even with an AD.
Does Coro perform an initial scan of OneDrive and SharePoint after they connect?
No, Coro does not perform an initial scan of OneDrive and SharePoint after they connect.
Does Coro detect malware in Microsoft OneDrive and SharePoint, or does it only monitor for data governance violations?
Coro detects malware in OneDrive and SharePoint files as soon as they are uploaded to cloud storage from an external source.
For more information, see Microsoft 365 detection and remediation.
Can I create exclusion groups for certain cloud accounts, so that every time a new service account is created in Active Directory (AD), Coro won't sync that service automatically with a Coro license?
No, you cannot create exclusion groups for cloud accounts.
Does Coro detect mass data downloads and deletions on endpoint devices?
No, Coro detects abnormal data deletions or downloads from individual users' cloud application accounts.
How quickly does Coro respond to an access permission violation?
Coro immediately responds to access permission violations by creating an Access permissions violation ticket when a user successfully logs into a protected service from an unauthorized origin, violating configured access rules.
What defines a mass data download as an anomaly?
A mass data download is considered anomalous when it deviates from typical usage patterns. There is no fixed threshold for what constitutes a mass data download. Instead, anomalies are identified based on activity that significantly differs from the established norm for each specific customer or application.
Does Coro automatically create the quarantine folder within my cloud storage service?
Yes, Coro creates a quarantine folder (named Suspected folder) at the point of malware detection. This folder is visible within the respective cloud storage service and Coro recommends that admin users restrict access in line with your organization's security policies.
Coro does not extend malware detection and file quarantine to Slack cloud storage due to limitations of the Slack API.
For further information, see malware detection in cloud drives.
What do the red and green indicators in Suspected Identity Compromise tickets mean?
In the Full Details section of Suspected Identity Compromise tickets, the red and green indicators distinguish between different types of activities. A red indicator marks activities suspected of compromise, while a green indicator marks activities presumed to be normative and safe.
For further information, see Suspected identity compromise.
Why is the same location being flagged as both abnormal and normal activity in the "Full Details" section of a Suspected Identity Compromise ticket?
This occurs because Coro has determined that the country in question is acceptable for this particular user or workspace. As such, activities from this location may initially appear as abnormal due to unusual patterns or timings but are ultimately recognized as normal when the context of the user's or workspace's settings is considered.
How can I monitor which cloud applications my protected users are accessing?
Coro provides visibility into cloud application usage. As an admin user, you can see which protected users are connected to which applications directly from the Coro console. This visibility helps you manage access control, detect anomalies, enforce compliance, and safeguard sensitive data. By monitoring cloud application usage, you can ensure only authorized users access protected applications and identify potential security threats.
Can Coro inform me about user inactivity?
Yes, Coro provides insights into user inactivity. A user is flagged as inactive if they haven't signed into their connected cloud applications or generated any loggable activity for 30 days. Admin users can customize the number of days from the Cloud Security Settings tab. Examples of a loggable activity include downloading files, deleting files, and signing in.
For more information, see Adding users and user groups for protection.
Why should I monitor user inactivity?
Monitoring user inactivity is crucial because inactive accounts can become targets for unauthorized access, potentially compromising sensitive systems or data. These accounts may retain access privileges, creating insider threats or compliance risks, and they can also consume unnecessary resources. Regularly reviewing and deactivating inactive accounts minimizes the attack surface, safeguards sensitive information, and ensures proper access management.
For more information, see Adding users and user groups for protection.
When is a cloud application user considered inactive?
By default, a cloud application user is considered inactive 30 days after their last recorded activity, triggering an Inactive user ticket. Admin users can customize the number of days from the Cloud Security Settings tab.
For more information, see Adding users and user groups for protection.
What actions can an admin user take when an unauthorized third-party application is identified by Coro?
An admin user can block an unauthorized third-party app from being installed. After it is blocked, the application appears in the Third-party applications blocklist.
For more information, see Third-party applications.
Which cloud applications are supported for connection and permissions management in Coro?
Coro supports connection and permissions management for Microsoft 365 and Google Workspace applications.
For more information, see Setting permissions for your cloud applications
Which cloud applications are supported for third-party application management in Coro?
Coro supports third-party application management for Microsoft 365 and Google Workspace applications.
For more information, see Third-party applications.
How do I unsuspend and restore access for a suspended user?
Cloud Security and User Data Governance tickets in Coro include an action to suspend a user from a named cloud application, or from all connected cloud applications. For more information, see Ticket types for Cloud Security or Ticket types for User Data Governance.
If the issue is resolved and you want to restore access for the user, you can unsuspend them via the original ticket.
For details, see Undoing actions.
What is impossible traveler detection?
Coro detects impossible travel when a user signs in from two distant locations within a time period too short for realistic travel. It calculates the minimum required travel time based on distance and adds a buffer for delays. Coro flags the activity and creates an Impossible Traveler ticket if the time between sign-ins is shorter than this threshold, indicating potential credential compromise or unauthorized access.
What are threat detection policies?
Threat detection policies enable admin users to define how Coro detects and responds to risky or suspicious activity in connected cloud applications.
Admin users can apply these policies to:
All users
Individual users
Specific user groups
Specific user labels
For more information, see Threat types.
What does MFA enrollment status show?
The multi-factor authentication (MFA) enrollment status on the Protected Users page shows whether protected users in Microsoft 365 and Google Workspace have MFA enabled.
For more information, see Protected Users.