Coro generates tickets relating to data governance when it identifies security incidents involving sensitive data policy violations.
Coro creates the following ticket types for sensitive data detection:
- Cloud Share Containing Senstive Data: The user shared a file from a connected cloud service that contains monitored sensitive data.
- Email Containing Sensitive Data: The user sent an email containing monitored sensitive data in the subject, body, or in attachments.
Use the Module and Type filters in the Ticket Log to find tickets of each type. To filter results by specific sensitive data types, Coro provides an additional Data Type filter:
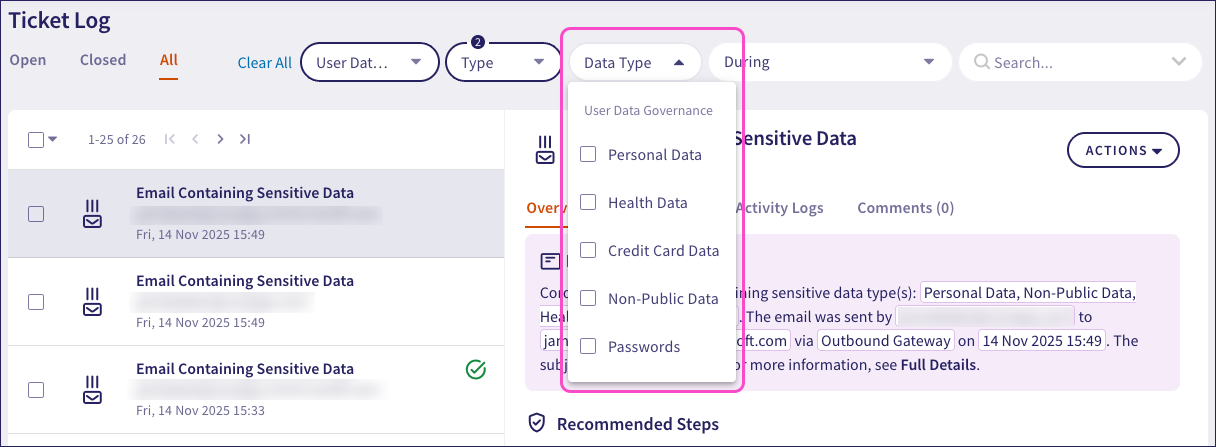
This filter is present only for the types listed above.
Coro deprecated the following ticket types in version 3.7:
- Credit Card Data
- Health Data
- Non-Public Data
- Personal Data
- Suspicious Exposure of Certificate
- Suspicious Exposure of Critical Data
- Suspicious Exposure of File Type
- Suspicious Exposure of Password
- Suspicious Exposure of Source Code
Coro now consolidates all policy violations for these data types for a single event into one sensitive data ticket.
To enable admin users to view historic tickets raised for deprecated types, Coro shows both deprecated and current ticket types in the left pane of the Ticket Log when you use the Type filter.
For an admin user to view sensitive data in the email content and findings sections of tickets related to User Data Governance, content inspection must be enabled. When disabled, these sections display a message stating Access to sensitive data is restricted if they contain sensitive data. For more information, see Managing admin users.
Depending on your configured User Data Governance monitoring settings, Coro creates a user data governance ticket when it detects one or more of the monitored data types in a file share or email. The raised ticket contains details of all occurrences of monitored sensitive data detected during the event, enabling admin users to review all violations of all data types for a single event in one place.
Coro raises separate tickets for exposure or access violations and, where a user exists in more than one connected cloud application, for each user account individually.
Coro categorizes detected sensitive data into the following types:
- Credit Card Data
- Health Data
- Non-Public Data
- Personal Data
- Certificates
- Critical data
- Selected file types
- Passwords
- Source code
To learn more about what information constitutes these sensitive data types, see Regulatory sensitive information types.
Admin users can configure permissions policies to control access and prevent exposure of sensitive data.
Additionally, if you have configured Coro's Outbound Gateway proxy for your organization's outgoing email, Coro can block emails that contain sensitive data, preventing data loss and unauthorized access. Admin users can release emails blocked by the Outbound Gateway from the corresponding tickets if the data exposure is deemed harmless, or delete emails permanently if the data exposure is confirmed as unwanted.
Coro determines the ticket state (open for review or automatically closed) based on the severity of the violation of policy or regulation. Events that have a high potential of direct violation of regulatory requirements or involve very sensitive information result in a ticket marked open for admin review. Coro closes these tickets after 10 days.
Events that involve detection of certain sensitive information in an email or shared file, but are considered less severe, result in automatically closed tickets. Coro includes these tickets for audit and analysis; however, they require no immediate action. Data compliance officers might need to review privacy-sensitive tickets to meet regulatory standards, such as GDPR and HIPAA.
For further information on data governance ticket state, see Ticket management.
Privacy-sensitive data tickets include the following actions:
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for selected sensitive data types. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |
To review policy violations and detected data items, select Full details from the ticket details pane:
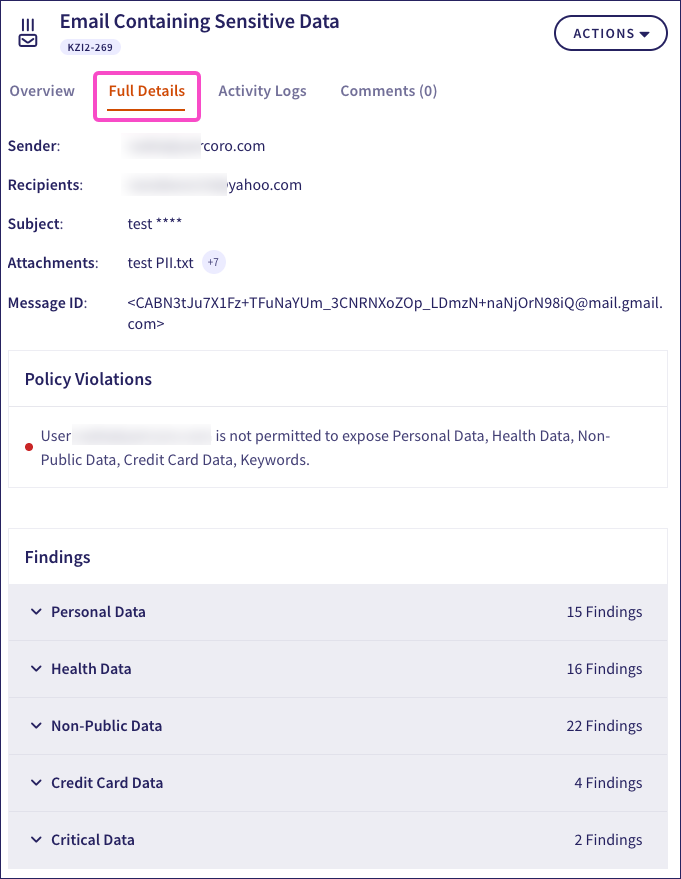
In this tab, Coro includes:
Event details: Main details of the exposure and the users involved.
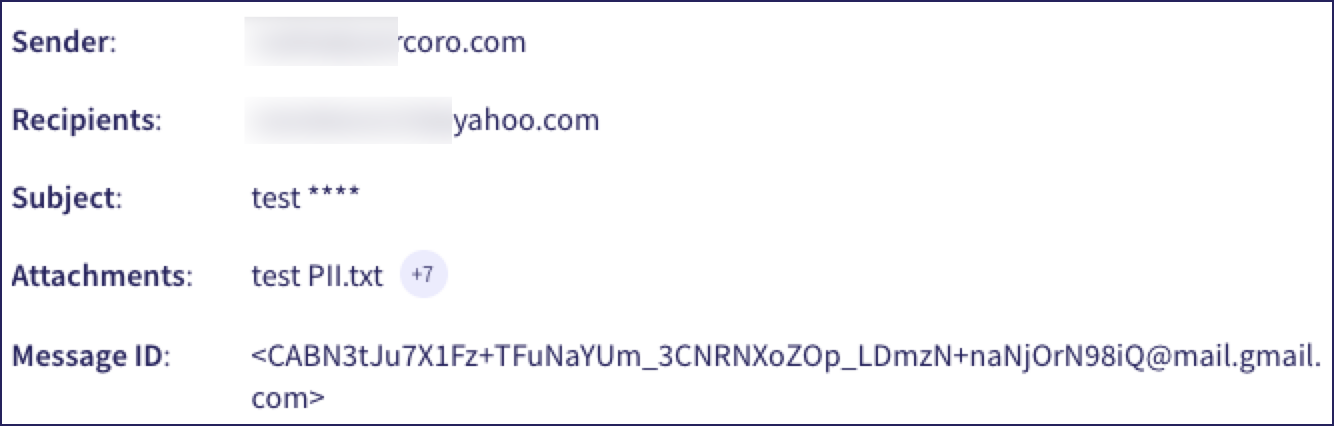
For an email event, Coro shows the sender, recipients, subject, any attachments, and the unique message identifier:
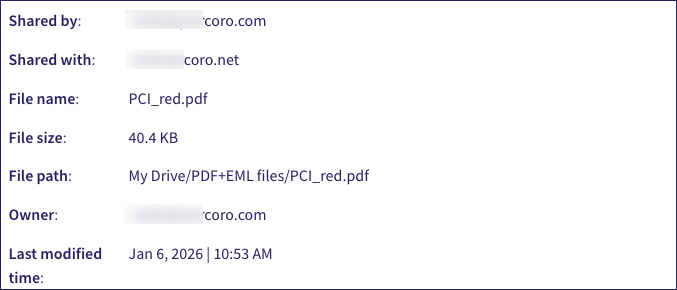
For a cloud share event, Coro shows the users and file share details:
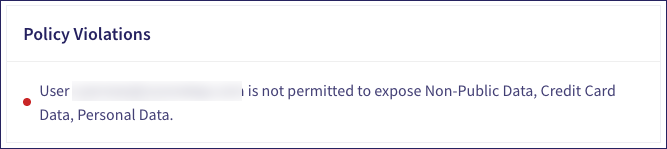
Policy violations: The policies that were violated:
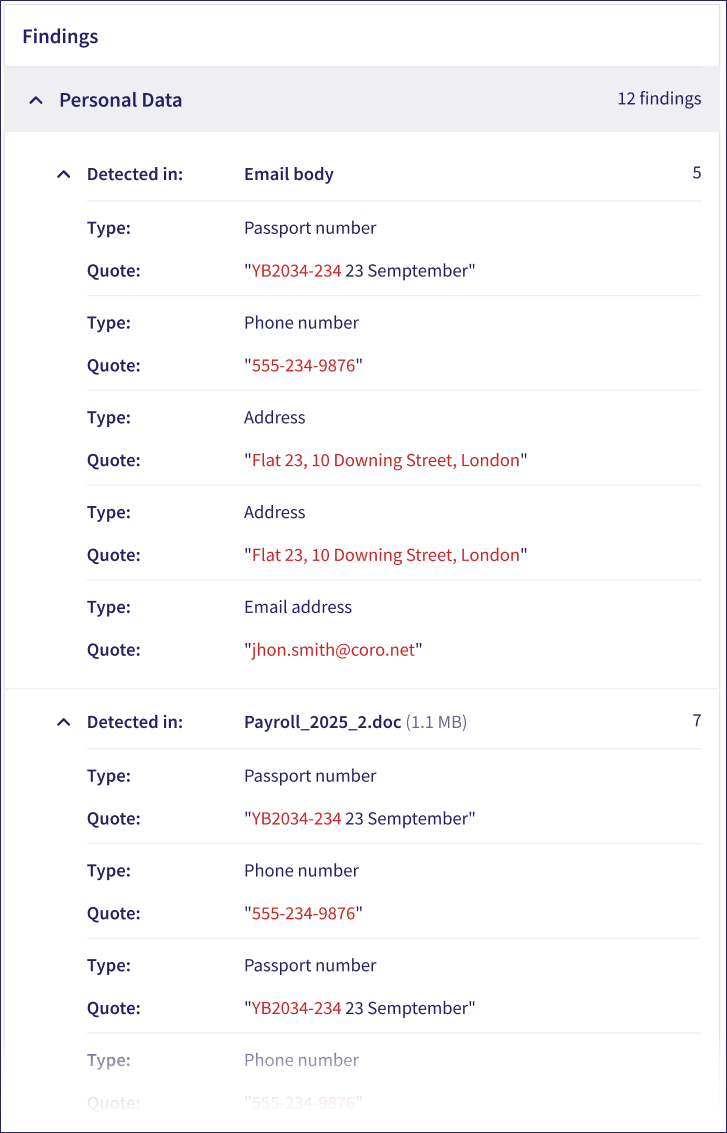
Findings: If available, Coro shows a list of the sensitive data items detected in the exposure. Coro groups detected data items by sensitive data type.
For email exposures, within each type, Coro groups relevant findings by detection source (email subject, body, or attachment).
Use the dropdown arrows to expand or close each section:
The following ticket types are deprecated. This information is provided for reference only in addressing historic tickets.
Coro detected that a user shared or emailed information that includes monitored sensitive data, based on the following types:
- Credit Card Data
- Health Data
- Non-Public Data
- Personal Data
Coro determines the ticket state (open for review or automatically closed) based on the severity of the violation of policy or regulation. Events that have a high potential of direct violation of regulatory requirements or involve very sensitive information result in a ticket marked open for admin review. Coro closes these tickets after 10 days.
Events that involve detection of certain sensitive information in an email, file, or file sharing, but are considered less severe, result in automatically closed tickets. Coro includes these tickets for audit and analysis; however, they require no immediate action. Data compliance officers might need to review privacy-sensitive tickets to meet regulatory standards, such as GDPR and HIPAA.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for this sensitive data type. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |
Coro identified a user account that was involved in a potential data exposure event with monitored security certificates (files with a .crt or .pem extension used to establish a secure connection between a client and a server). This occurs where monitoring for Certificates was enabled (see Monitoring). Tickets remain open for review by an admin user until Coro closes them automatically after 10 days.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for this sensitive data type. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |
Coro identified a user account that was involved in a potential data exposure event with monitored critical data (specific defined keywords in email and shared file content). This occurs where monitoring for Specific keywords was enabled (see Monitoring). Tickets remain open for review by an admin user until Coro closes them automatically after 10 days.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for this sensitive data type. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |
Coro identified a user account that was involved in a potential data exposure event with monitored file types (specific defined file types added as email attachements and in shared drive content). This occurs where monitoring for Specific file types was enabled (see Monitoring). Tickets remain open for review by an admin user until Coro closes them automatically after 10 days.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for this sensitive data type. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |
Coro identified a user account that was involved in a potential data exposure event that included passwords. This occurs where monitoring for Passwords was enabled (see Monitoring). Tickets remain open for review by an admin user until Coro closes them automatically after 10 days.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for this sensitive data type. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |
Coro identified a user account that was involved in a potential data exposure event that included monitored source code files (files with a known code or script extension such as .md, .yaml, .sh). This occurs where monitoring for Source code was enabled (see Monitoring). Tickets remain open for review by an admin user until Coro closes them automatically after 10 days.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, Coro automatically closes all open tickets associated with the device. |
| Suspend user from all cloud apps | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their accounts on all protected cloud applications. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Suspend user from <cloud service> | (Not applicable for events involving emails sent through Coro's Outbound Gateway) Coro suspends the user's access to their account on the designated cloud application. Coro updates the ticket activity log with a corresponding entry for the event. To remove the suspension and restore access, select UNDO adjacent to the activity log entry. |
| Remove exposed sharing | For tickets involving data shared on cloud drives, remove the exposed data share and render any link to it as inactive. |
| Contact user | Coro sends an email to the recipient containing a message about the ticket. Coro adds a record of the action to the ticket and the activity log. |
| Add to data governance permissions | Extend the identified user's data governance permissions to allow access and exposure for this sensitive data type. To learn more, see data permissions. |
| Allow email | (Applies only to emails blocked by Coro's Outbound Gateway) Release the blocked email to all named recipients, or to a selected sub-set of the original recipients. |
| Delete email | (Applies only to emails blocked by Coro's Outbound Gateway) Permanently delete the email. |