Suspected identity compromise
Suspected Identity Compromise tickets report instances of potential user account breaches and abnormal admin activity, focusing on actions that pose a significant threat to customer data.
These tickets present key details of the event, including the access point location and descriptions of the specific activities deemed suspicious:
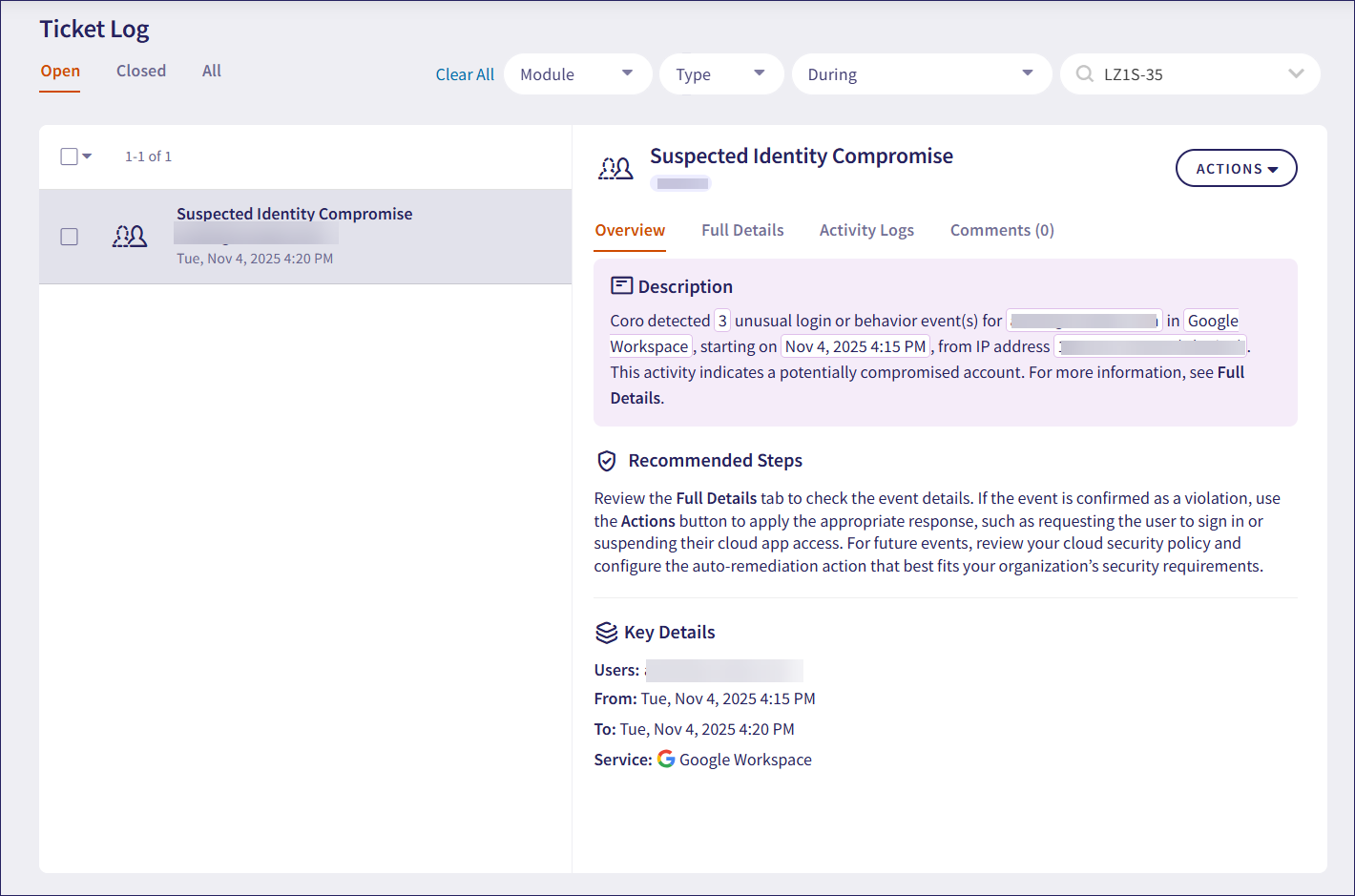
Suspected Identity Compromise tickets are triggered not only by password attempts but also by changes in the location or pattern of sign-in activity, which may indicate a potential compromise of the user's account.
If an access permissions policy applies to the user, Coro checks for access permissions policy violations and does not check for suspected identity compromise.
For more information, see Access permissions violation.
Suspected Identity Compromise tickets are classified as open for review, and are automatically closed after a review period of 10 days.
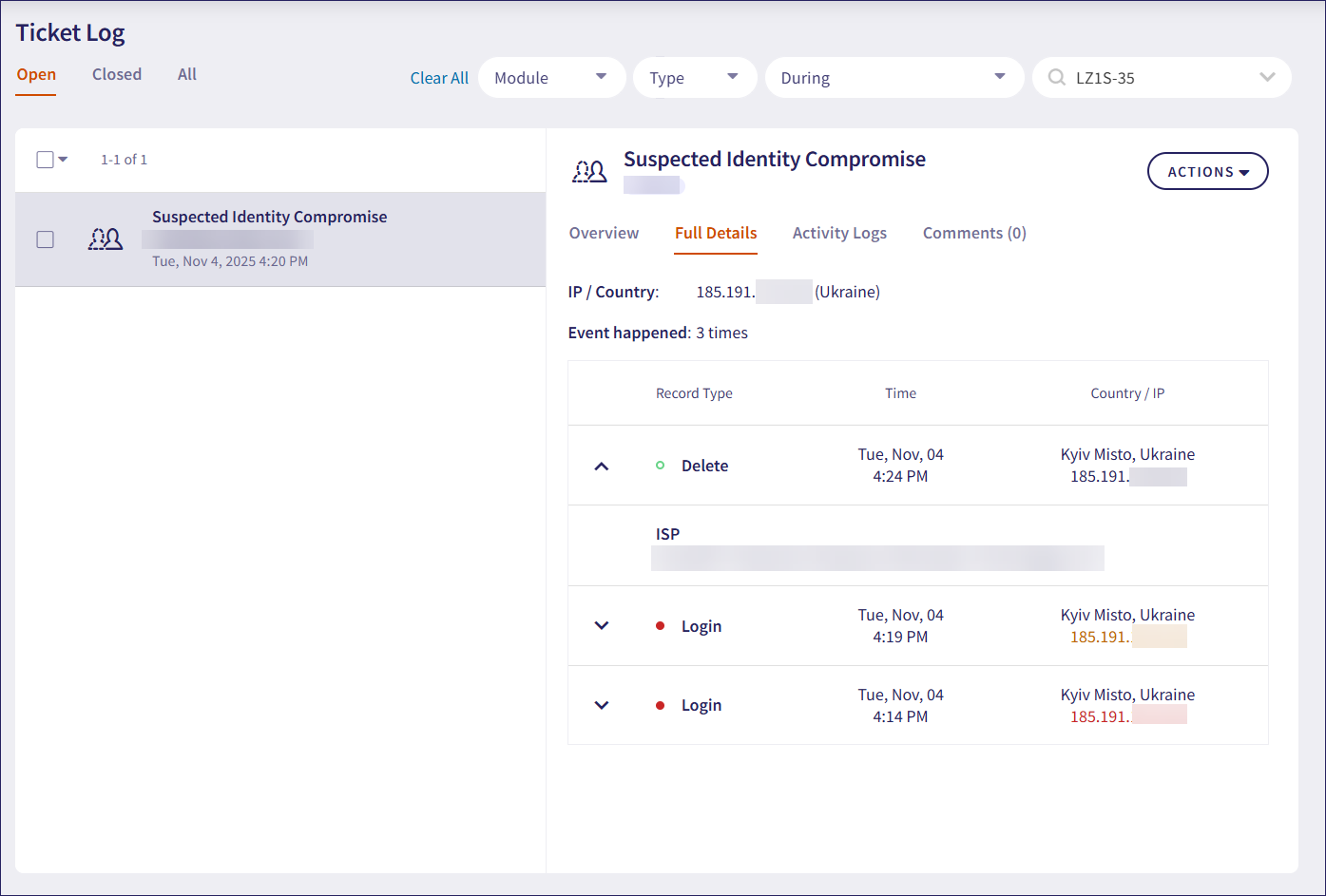
The Full Details tab provides references to normative actions taken in close proximity to suspected activities. Suspected activities are shown in red, while typical activities are shown in green. Coro uses IP lookup providers to derive metadata about connecting IP addresses to help admin users identify suspicious patterns. If the threat level associated with an IP address is high, the IP address is red. If the threat level is medium, the IP address is yellow. Select the dropdown next to an activity to view identified details, such as service provider, proxy, organization name, or threat type (where one is identified).
In the example below, Coro flagged suspicious Login activity. Use the dropdown next to each activity to view metadata related to the IP address, such as the service provider (ISP):
For more information about ticket types, see Ticket types for Cloud Security.