Configuring data governance settings
Effective Data Loss Prevention (DLP) policies help prevent unauthorized access to sensitive information and prevent accidental exposure to unauthorized third parties.
Coro's User Data Governance module enables admin users to configure DLP to scan outgoing email communications in real-time. If Coro detects sensitive information exposure that violates your DLP settings, Coro can respond in one of the following ways:
- Coro monitors breaches of configured data policy, but does not prevent the action taking place.
- Coro blocks all attempts to expose or share identified sensitive data items.
In both modes, Coro alerts admin users to policy breaches through User Data Governance tickets.
When a new workspace is created, all User Data Governance options are disabled by default. Permissions settings take effect after monitoring is enabled for one or more User Data Governance options.
To configure Coro's DLP settings:
From the sidebar, select Control Panel:
Select User Data Governance:
Select Monitoring.
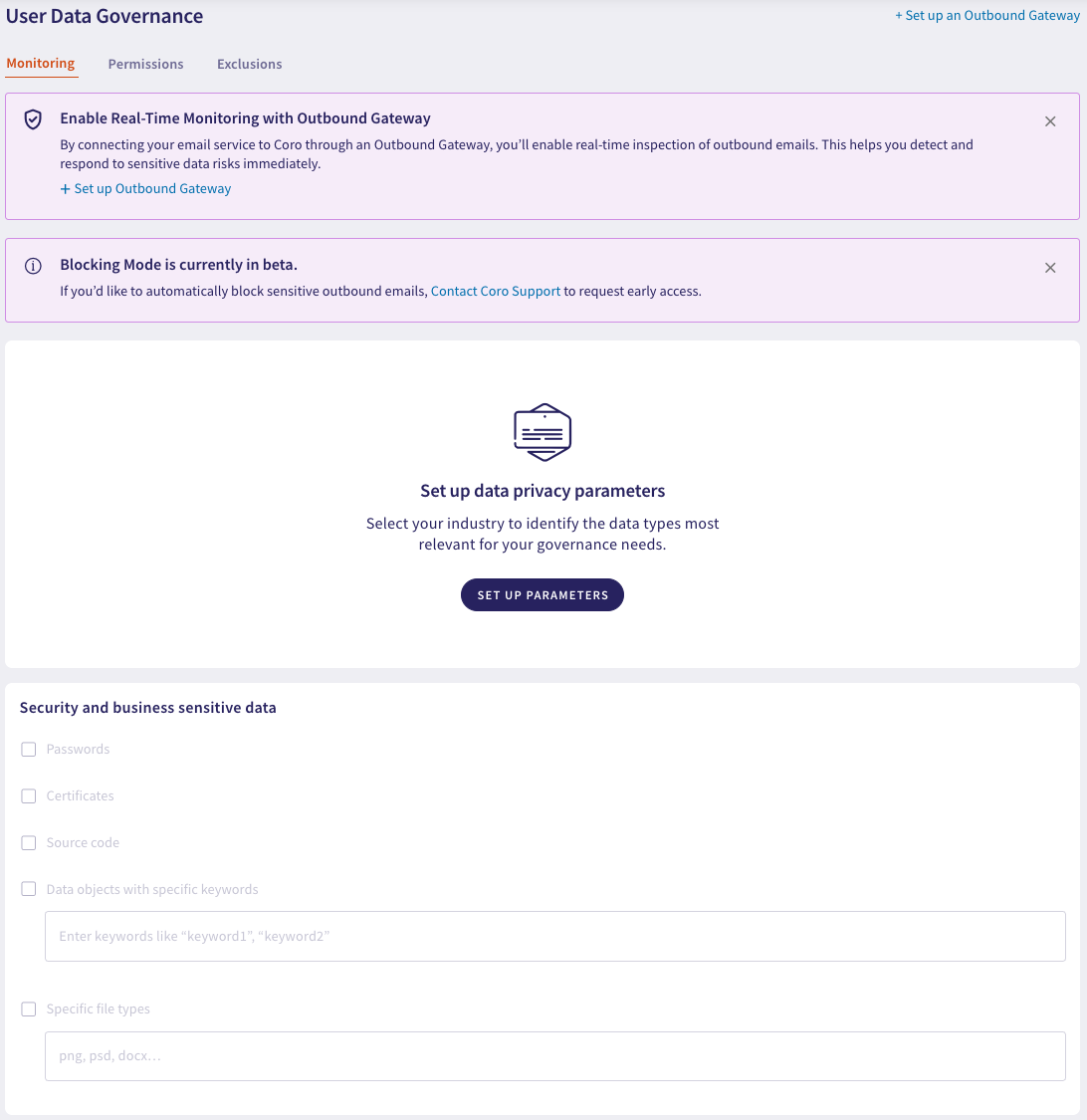
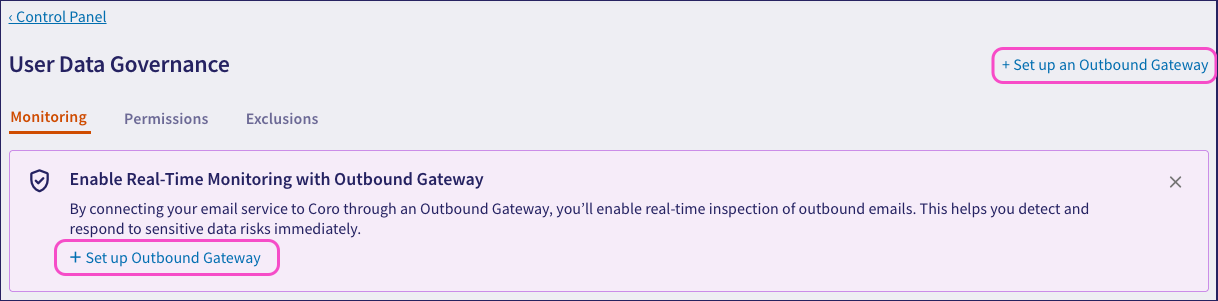
In an unconfigured state, Coro provides banners to get started:
In a configured state, Coro shows your currently selected DLP settings:
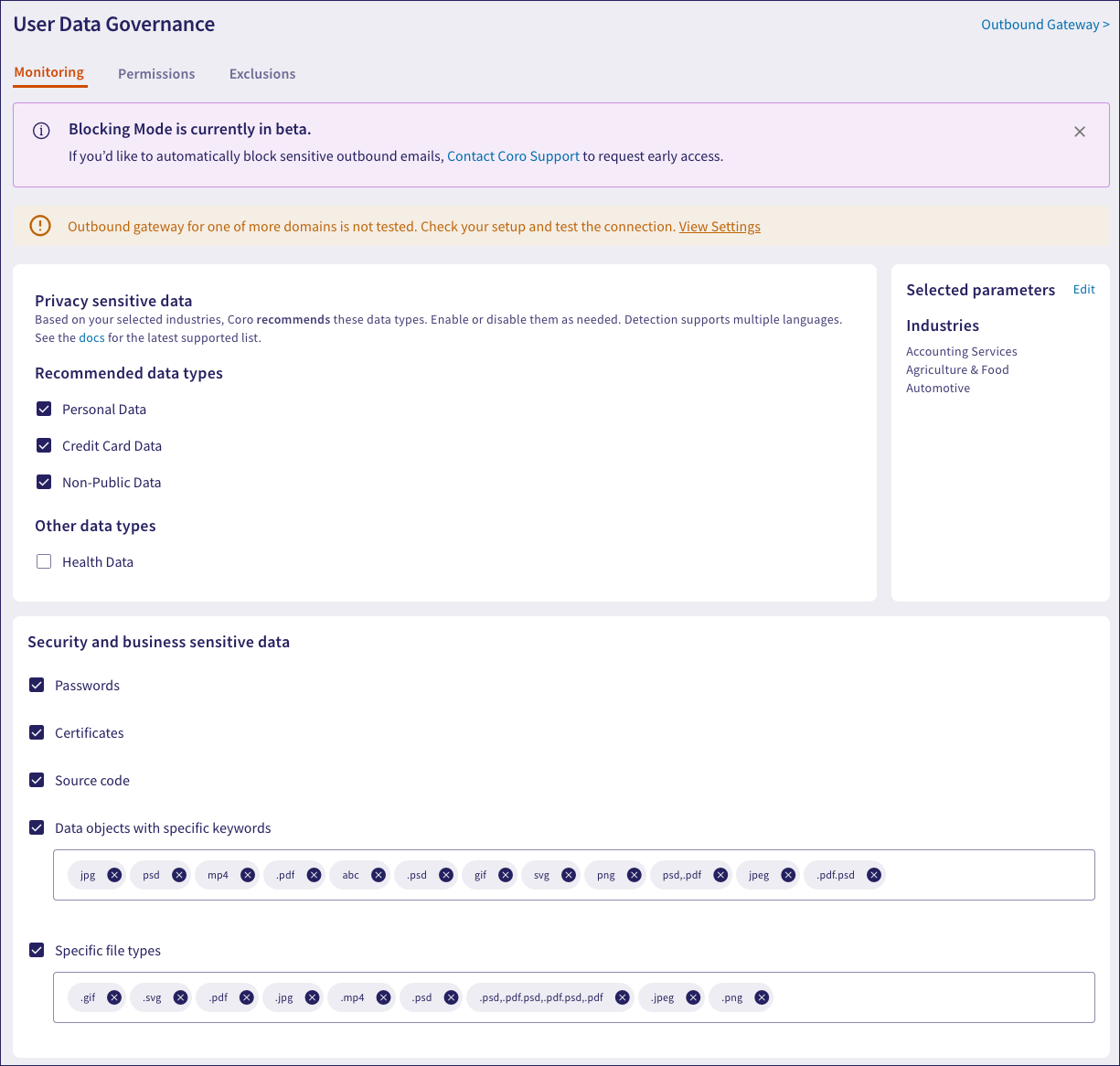
The Monitoring tab consists of the following sections:
User Data Governance mode
This is a beta feature and available only on request. Coro operates in Monitor only mode by default. Contact Coro Support to enable Block mode.
Coro enacts DLP decisions for selected privacy sensitive data items and security and business sensitive data items based on the selected mode:
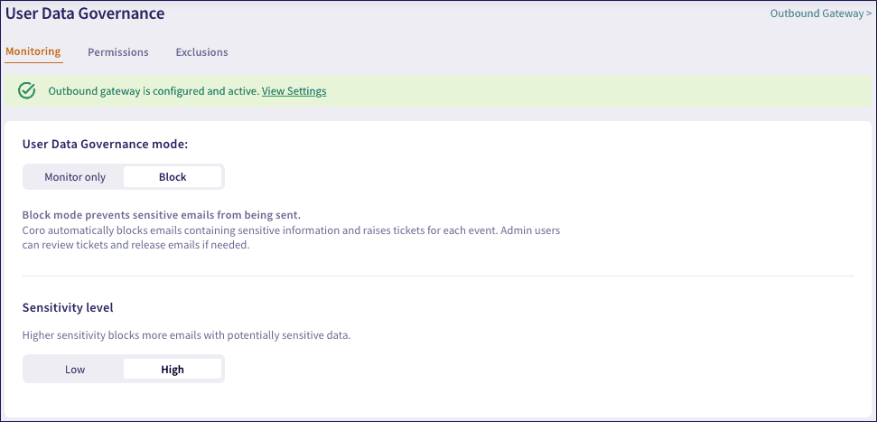
Monitor only: Tracks sensitive data exposure inside emails sent to external unauthorized recipients, but does not prevent the action. The email is not blocked inside your organization and continues on to the named recipients.
Block: Detects sensitive data exposure inside emails, preventing them from being sent. An admin user can review the breach and choose to permanently delete the email, or release it if the event is determined to be safe.
To use block mode, admin users must configure an Outbound Gateway proxy to handle email processing.
Select either of the highlighted links at the top of the page to start the process:
If emails are blocked, the admin user can review breaches through raised User Data Governance tickets. Tickets for blocked emails contain actions to either permanently delete the email message or to approve and release the email to recipients.
Where block mode is activated, select the Sensitivity level you want Coro to apply to decisions. Choose from:
Low sensitivity: Coro blocks only those emails that contain sensitive data items that would result in an open ticket. This is the default setting.
High sensitivity: Coro blocks emails that contain sensitive data items that would result in both open and automatically closed tickets.
Privacy sensitive data
The Privacy sensitive data section lets you create a data privacy configuration tailored to your organization’s needs. Based on your selected industry, Coro automatically selects the sensitive data types to monitor for access and exposure within email and shared cloud drive data. This streamlines data privacy setup and enables:
Industry-based configuration: Select your industry to tailor data privacy settings to your organization.
Automated sensitive data type recommendations: Coro automatically selects sensitive data types based on your industry to help reduce ticket fatigue by minimizing unnecessary ticket generation. For more information, see Sensitive data types assigned per industry.
Configuration customization: Modify industry selections and data types to fit your organization’s needs.
For information on the sensitive data that Coro recognizes, see Sensitive data recognized by Coro.
For information on sensitive data type tickets, see Ticket types for User Data Governance.
Creating a data privacy configuration
Use the Privacy sensitive data section on the Monitoring tab to create a data privacy configuration tailored to your organizational requirements.
Coro automatically assigns sensitive data types based on your selected industry.
To create a configuration:
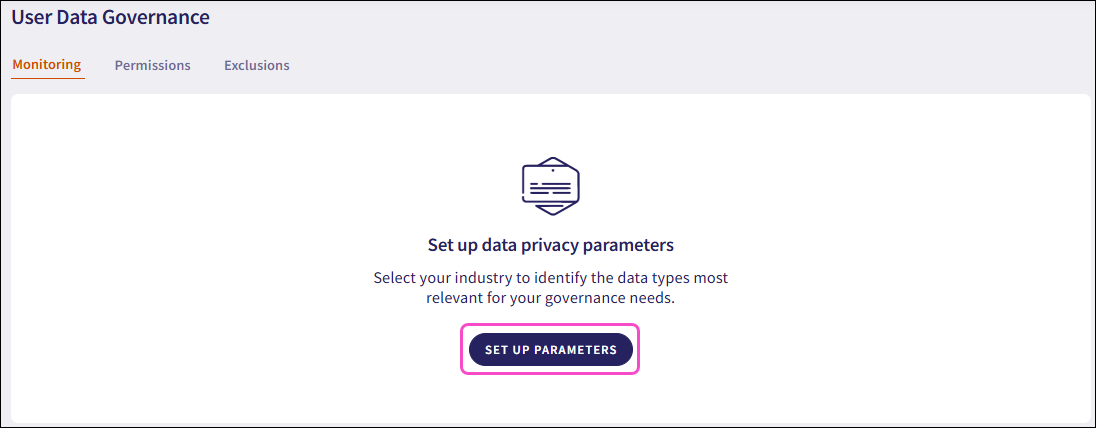
From the Monitoring tab, select SET UP PARAMETERS:
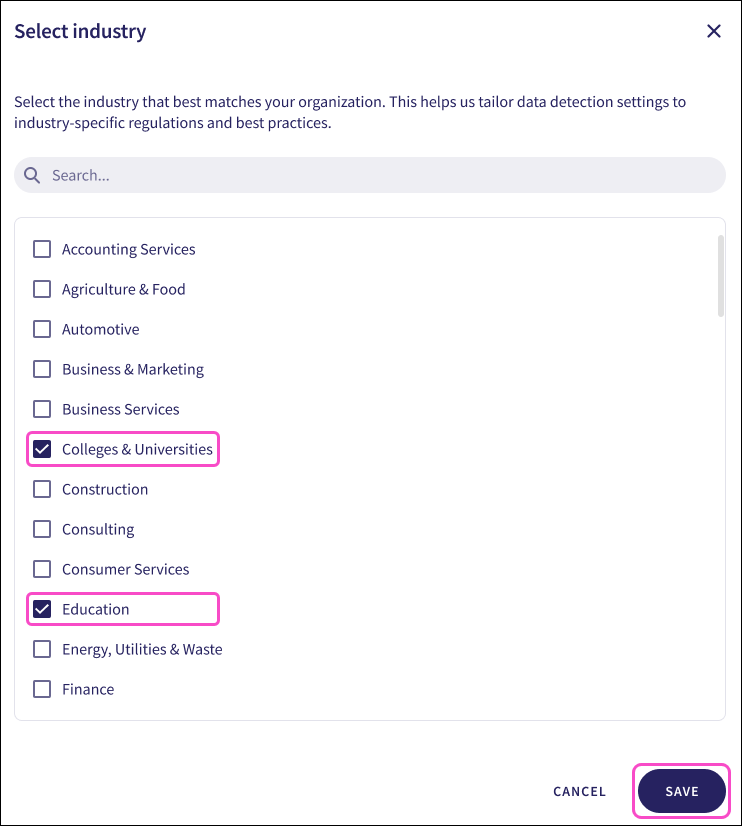
Coro opens the Select industry dialog:
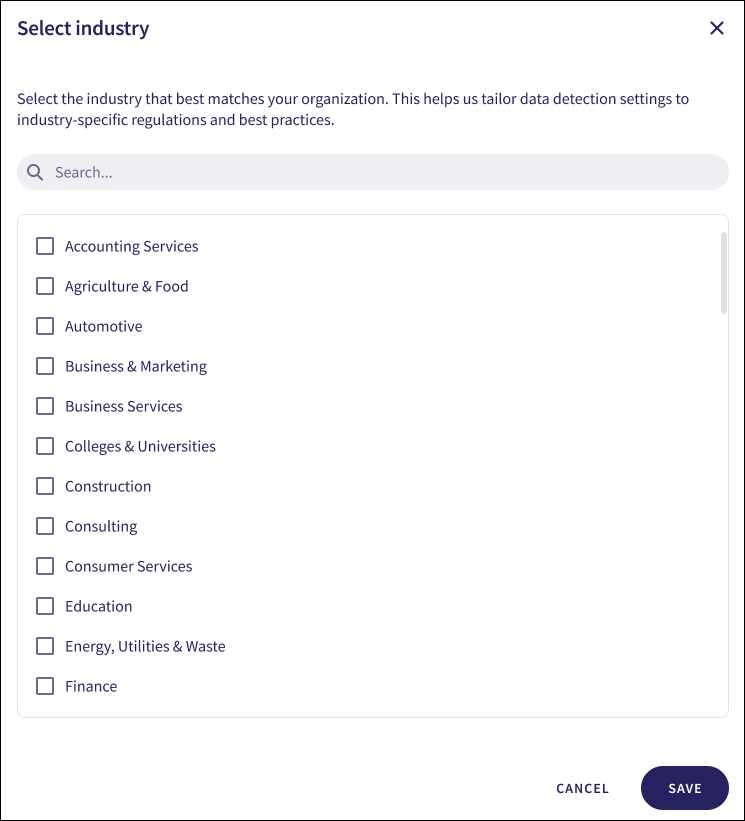
Enable the industries applicable to your organization.
Use Search... to filter the list.
Select SAVE to create your data privacy configuration:
Coro displays your configuration and recommended data types:
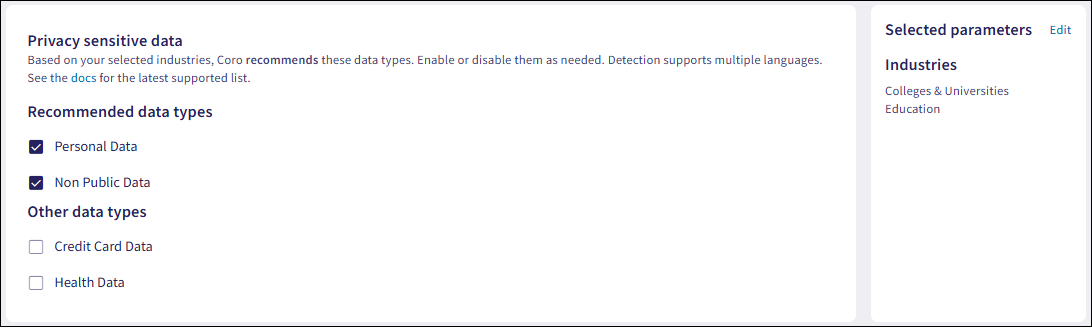
Select additional sensitive data types from the Other data types section to tailor detection for your organization.
Editing a data privacy configuration
Edit an existing data privacy configuration to modify industries and sensitive data types.
Editing industries
Edit industries defined in an existing configuration from the Selected parameters pane.
To edit industries:
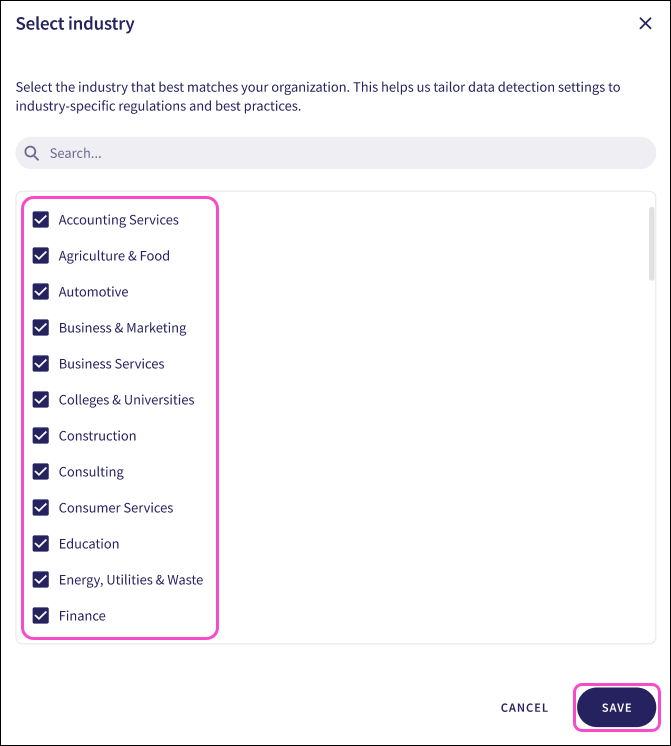
Select Edit:

Coro opens the Select industry dialog.
Enable or disable additional industries.
Use Search... to filter the list.
Select SAVE to update your data privacy configuration:
Coro displays your updated configuration:
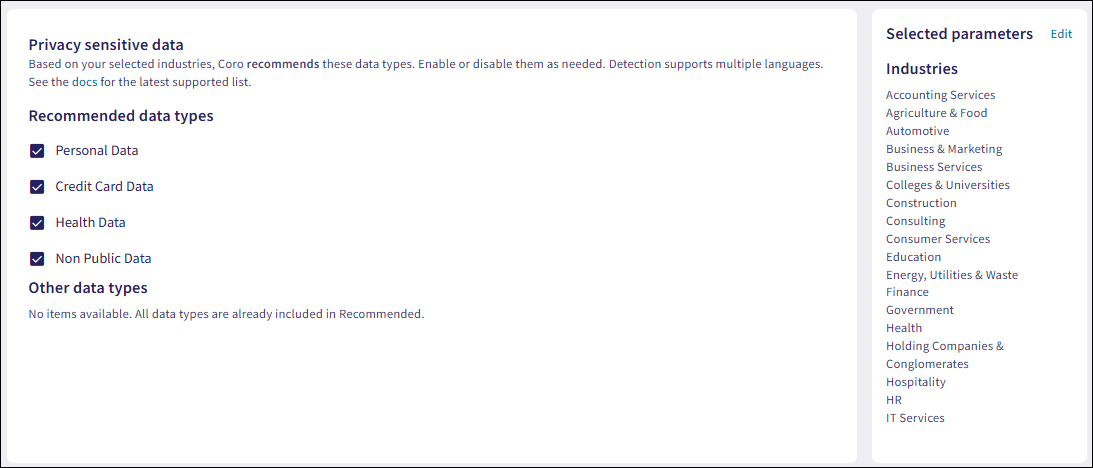
Editing sensitive data types
Edit sensitive data types defined in an existing configuration from the Privacy sensitive data pane.
Editing your sensitive data types overrides the recommended selections made by Coro.
To edit sensitive data types:
In Recommended data types, enable or disable sensitive data types preselected by Coro.
In Other data types, enable or disable additional sensitive data types not preselected by Coro.
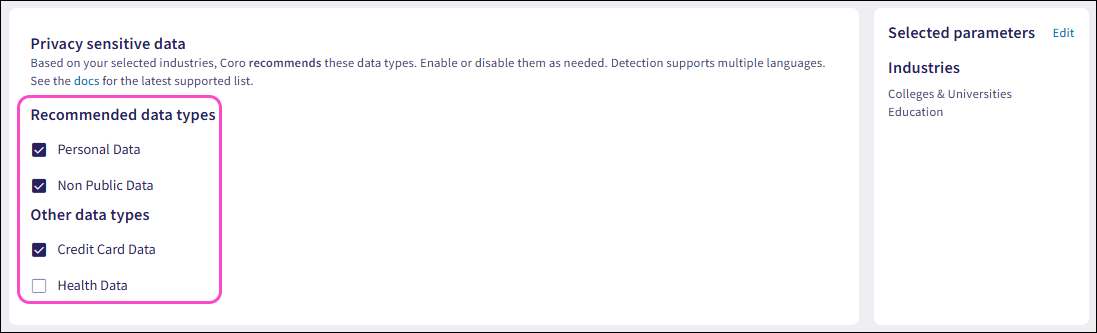
Coro automatically saves and applies your changes to sensitive data types.
Security and business sensitive data
The Security and business sensitive data section allows you to enable monitoring of additional sensitive data types that are important to your individual organization.
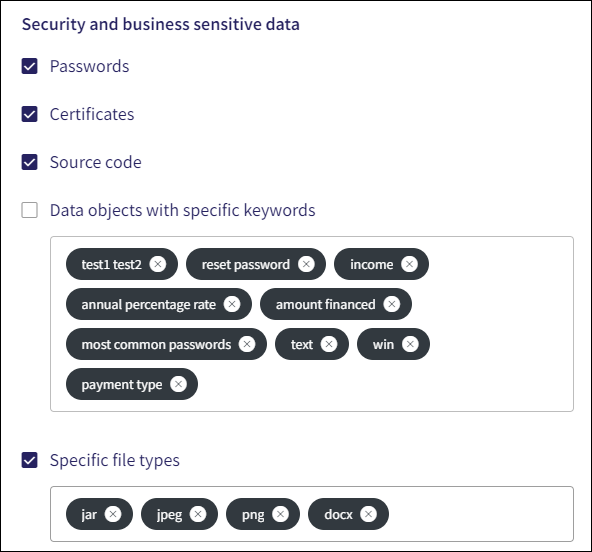
Coro monitors the following Security and business sensitive data:
Passwords: Monitors for potential password exposure.
Certificates: Monitors security certificate files, such as SSL certificates, which are used to establish secure connections between web servers and browsers.
Source code: Monitors source code files (such as *.md, *.yaml, *.sh, *.slx, *.mdl, *.m, and *.json).
Data objects with specific keywords: Identifies and matches defined keywords in email and shared file content, including subject, body, and attachment filenames. Keyword matching is case validated, and Coro removes duplicate keywords, keeping only the lowercase version. Email domains and sender/recipient names are not used for keyword matching.
Specific file types: Monitors files added as email attachments and in shared drive content that match one of the defined file extentions.
Sensitive data types assigned per industry
Coro User Data Governance and Endpoint Data Governance automatically assign sensitive data types to your data privacy configuration based on your industry:
This table does not cover all industries and might not address every scenario or requirement. Admin users must ensure that the data types they select in their Coro data governance configuration meet their organization’s needs.
| Industry | Data type |
|---|---|
| Accounting services | Personal data |
| Agriculture and food | Personal data AND credit card data |
| Automotive | Non public data |
| Business and marketing | Personal data |
| Business services | Personal data |
| Colleges and universities | Non public data AND personal data |
| Construction | Personal data |
| Consulting | Personal data |
| Consumer services | Personal data |
| Education | Personal data |
| Energy, utilities, and waste | Personal data AND credit card data |
| Finance | Non public data |
| Government | Personal data |
| Health | Health data AND personal data AND credit card data |
| Holding companies and conglomerates | Personal data |
| Hospitality | Personal data AND credit card data |
| HR | Personal data |
| Insurance | Non public data |
| IT services | Personal data AND credit card data |
| Law firms and legal services | Personal data |
| Manufacturing | Personal data |
| Media and internet | Personal data AND credit card data |
| Minerals and mining | Personal data |
| Organizations | Personal data |
| Pharma | Health data AND personal data AND credit card data |
| Real estate | Personal data |
| Retail | Personal data AND credit card data |
| Software | Personal data AND credit card data |
| Telecommunications | Personal data AND credit card data |
| Transportation | Personal data AND credit card data |