As part of a virtual office, Coro includes the ability for customers to configure VPNs together with site-to-site tunnels.
This guide describes how to configure Coro to integrate with a UniFi Security Gateway (USG) firewall, and how to configure UniFi USG to allow traffic for your VPN from both inside and outside the network.
Before you start, make sure you have the following:
- Access as an admin user with sufficient permissions to the Coro console for your workspace.
- An active subscription (or trial) for the Coro Network module.
- Access to the USG configuration interface.
Verify that your USG firewall allows inbound and outbound traffic for the following Coro Network subnets:
- 10.8.0.0/16
- 10.9.0.0/16
- 10.10.0.0/16
Alternatively, configure firewall policies to permit only the specific ports and protocols used by the VPN tunnel.
Configure your USG firewall to allow traffic from inside and outside the network:
Sign in to your USG configuration interface.
Go to Networks > Add New Network:
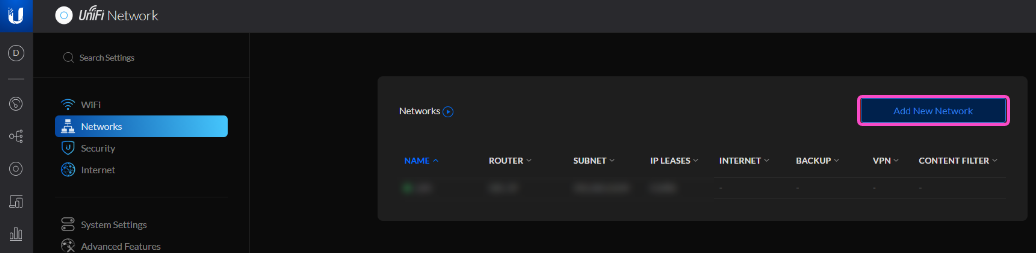
Configure your VPN Settings:
Name: Enter a suitable name for your site-to-site tunnel.
VPN Type: Select Site-to-Site.
VPN Protocol: Select Manual IPsec.
Enable Enable this Site-to-Site VPN.
Remote Subnets: Enter 10.8.0.0/16, 10.9.0.0/16, 10.10.0.0/16.
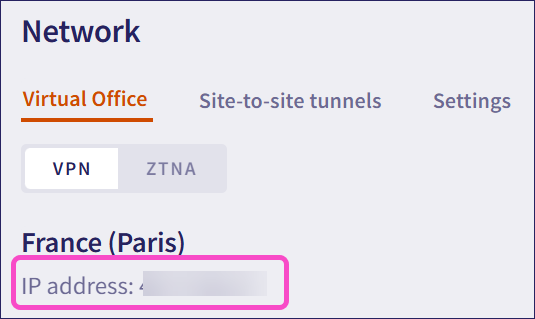
Peer IP: Enter the Coro public IP address. The Coro public IP address is retrieved from the Network module in the Coro console.
To retrieve the Coro public IP address:
From the sidebar, select Control Panel.
Select Network:
Coro displays the Coro public IP address on the Virtual Office tab:
- Local WAN IP: Enter the public IP address of your USG.
- Pre-Shared Key: Enter the pre-shared key you created in the Management Portal.
Leave all other VPN Settings at their default value.
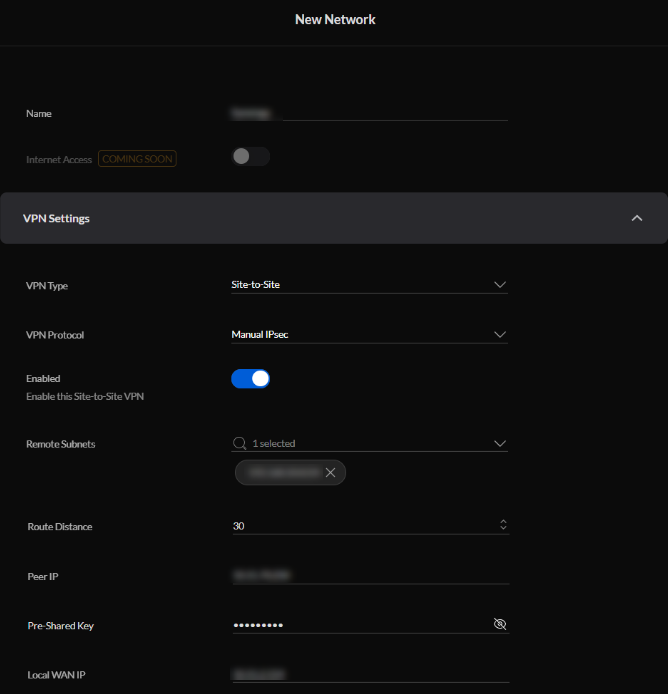
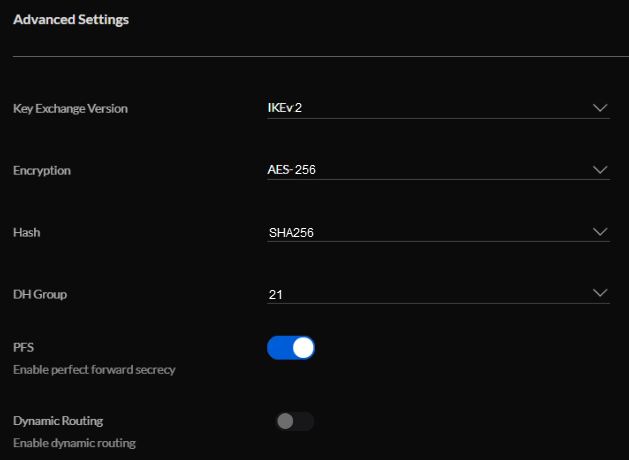
Configure the following Advanced Settings:
Key Exchange Version: Select "IKEv2" if supported by your firewall version, or else select "IKEv1".
Encryption: Select "AES-256".
Hash: Select "SHA256".
DH Group: Select "21".
Enable PFS.
Disable Dynamic Routing.
Configure Coro with details of your site-to-site tunnel and firewall:
From the sidebar, select Control Panel.
Select Network:

Select Site-to-site tunnels:
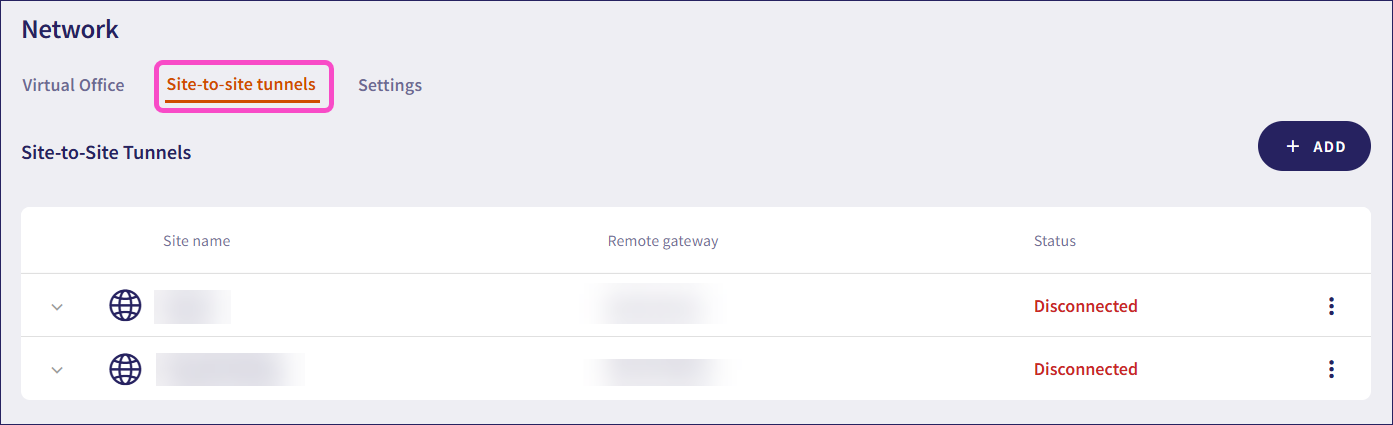
Select + ADD to add a new site-to-site tunnel configuration.
Configure your site details:
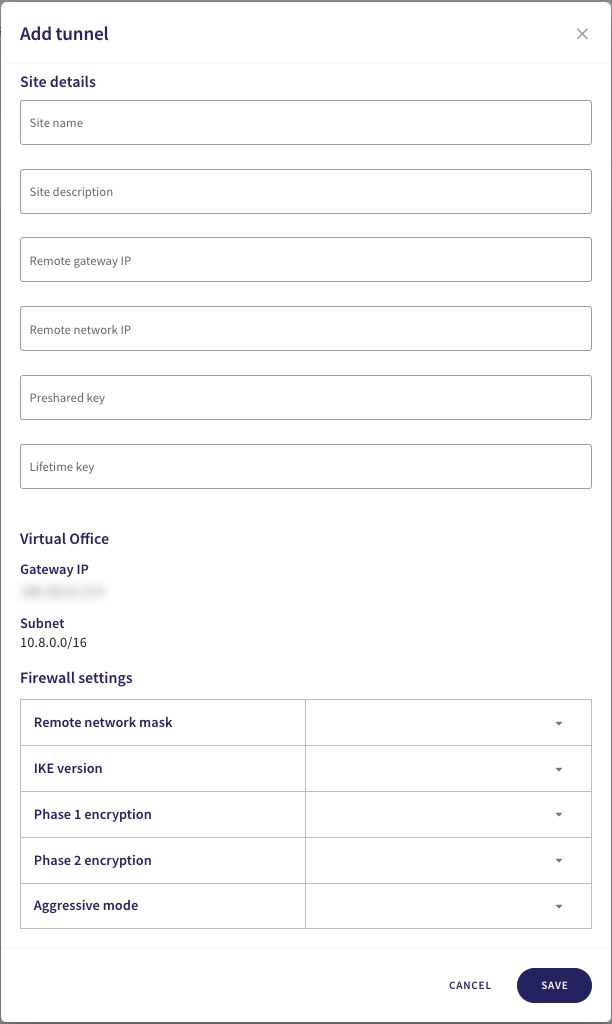
Avoid using special characters and spaces in your site details or preshared key.
- Site name: Enter a suitable name for your site-to-site tunnel.
- Site description: Enter a suitable short description for the tunnel.
- Remote gateway IP: Enter USG's public IP address obtained here.
- Remote network IP: Enter USG's internal network IP address.
- Preshared key: Enter the preshared key used here.
- Lifetime key: Enter "28800".
In the same dialog, configure the Firewall settings:
- Remote network mask: Enter USG's subnet obtained here.
- IKE version: Select "IKEv2".
- Phase 1 encryption: Select "AES256-SHA256-D2" or "AES256-SHA256-D14".
- Phase 2 encryption: Select "AES256-SHA256-D2" or "AES256-SHA256-D14".
- Aggressive mode: Select "No".
To save your configuration, select SAVE.