As part of a virtual office, Coro enables customers to configure virtual private networks (VPNs) together with site-to-site tunnels.
The VPN tunnels provide a secure, encrypted secure connection for transmitting data privately over the internet. VPN uses internet protocol security (IPsec), which authenticates and encrypts packets of data to provide secure encrypted communication between two devices.
This guide describes how to configure Coro to integrate with Sophos's firewall, and how to configure Sophos to allow traffic for your VPN from both inside and outside the network.
Before you start, make sure you have the following:
- Access as an admin user to the Coro console for your workspace.
- An active subscription (or trial) for the Coro Network module.
- Access to the Sophos admin portal.
Configure Coro with details of your site-to-site tunnel and firewall:
From the sidebar, select Control Panel.
Select Network:
Select Site-to-site tunnels:
Select + ADD to add a site-to-site tunnel configuration:
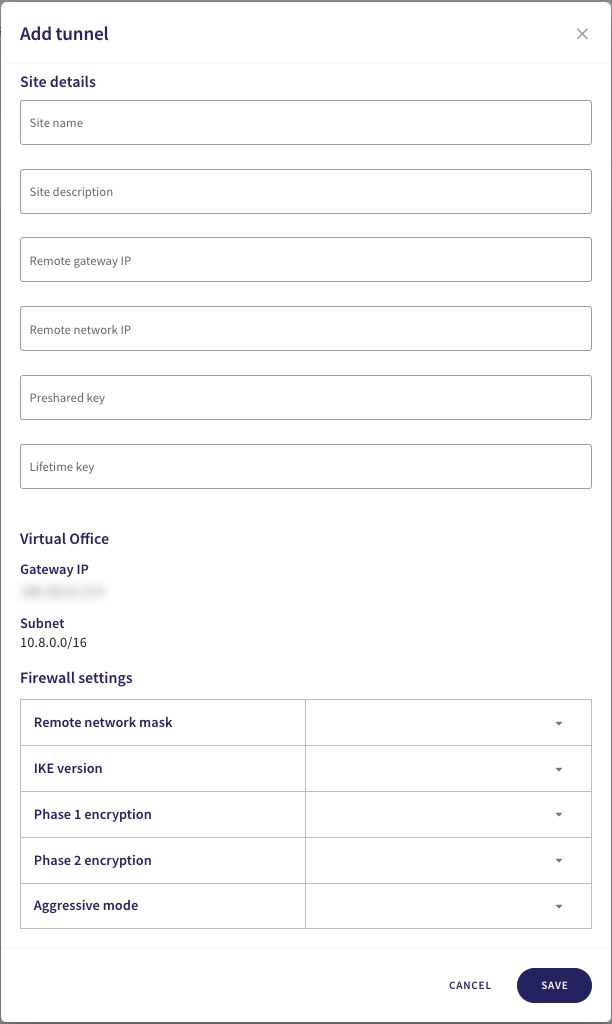
Avoid using special characters in your site details.
- Site name: Enter a suitable name for your site-to-site tunnel.
- Site description: Enter a suitable short description for the tunnel.
- Remote gateway IP: Enter the firewall/router WAN IP address for the remote site.
- Remote network IP: Enter the private IP address range used at the remote site.
- Preshared key: Enter a shared password (secret) that both sites use to authenticate and secure the tunnel. Use a minimum of 20 characters, and keep a note of the key for configuration on the Sophos device.
- Lifetime key: Enter 86400.
In the same dialog, configure the firewall settings:
- Remote network mask: Select your local network subnet mask. For example, 16 or 24.
- IKE version: Select IKEv2.
- Phase 1 encryption: Select AES256-SHA1-D14.
- Phase 2 encryption: Select AES256-SHA1-D14.
- Aggressive mode: Select No.
To save your configuration, select SAVE.
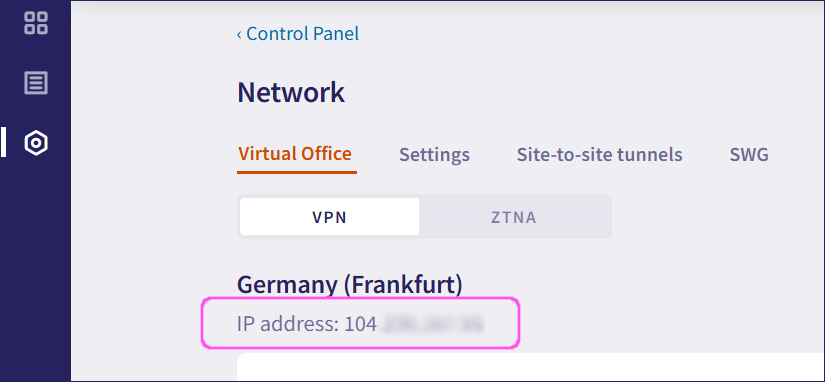
Make a note of your virtual office IP address for configuring your Sophos firewall. Locate the IP address displayed at the top of the Virtual Office tab:
Verify that your Sophos firewall allows inbound and outbound traffic for the following Coro Network subnets:
- 10.8.0.0/16
- 10.9.0.0/16
- 10.10.0.0/16
Alternatively, configure firewall policies to permit only the specific ports and protocols used by the VPN tunnel.
Configure your Sophos firewall to allow traffic from inside and outside the network:
Sign in to your Sophos admin portal.
Create an IPsec VPN connection:
- Go to Site-to-site VPN > IPsec and select Wizard:
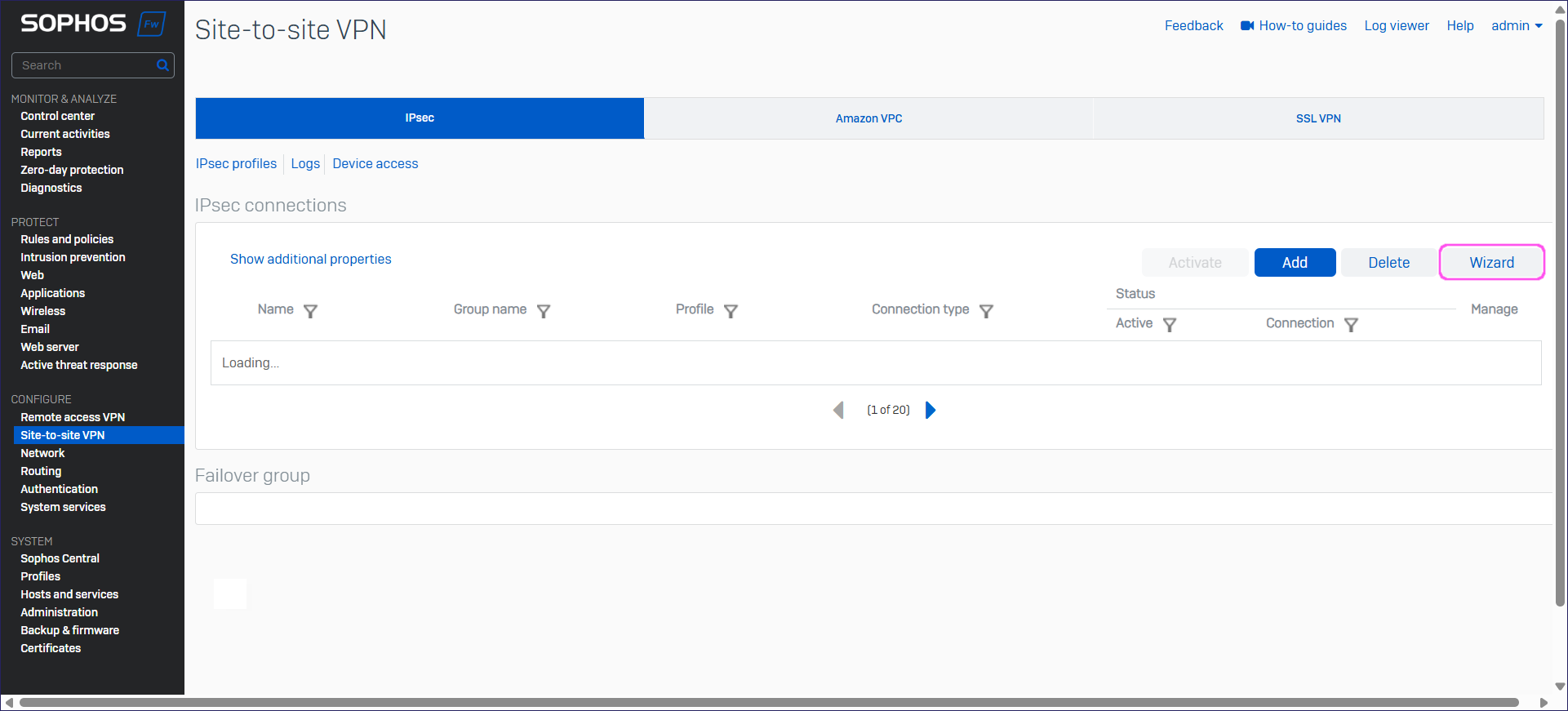
Sophos opens the VPN connection wizard.
In Overview, enter the following:
Name: a name for the connection.
Description: a description for the connection.
Select Start to start the wizard:
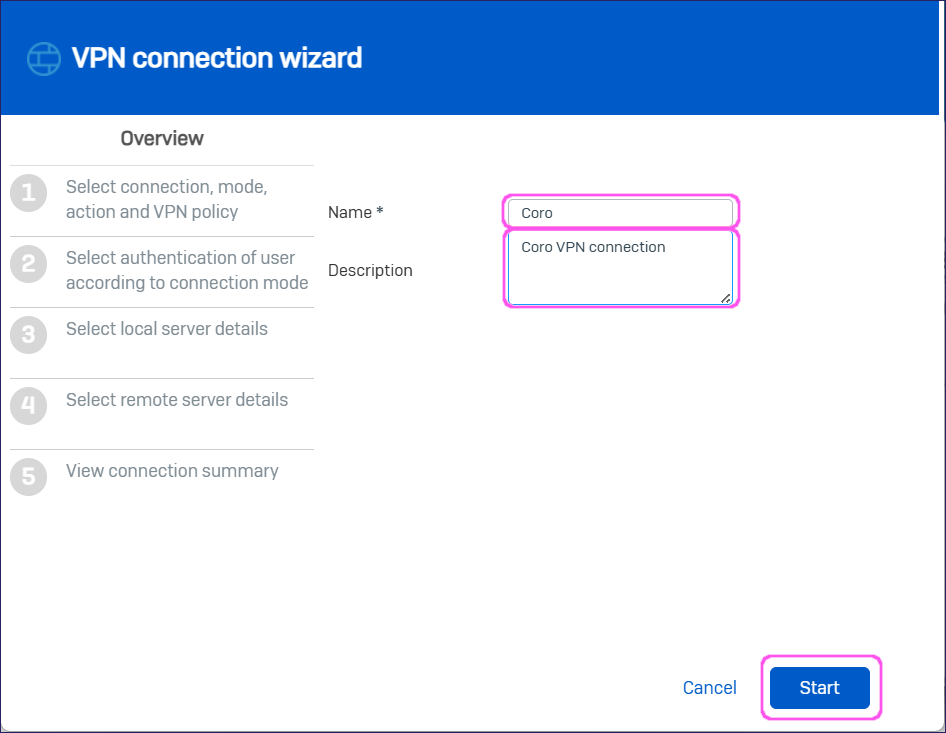
In Select a connection type, select Site To Site, then specify the following:
Select a base location: Select Head Office.
Action: Select Initiate:
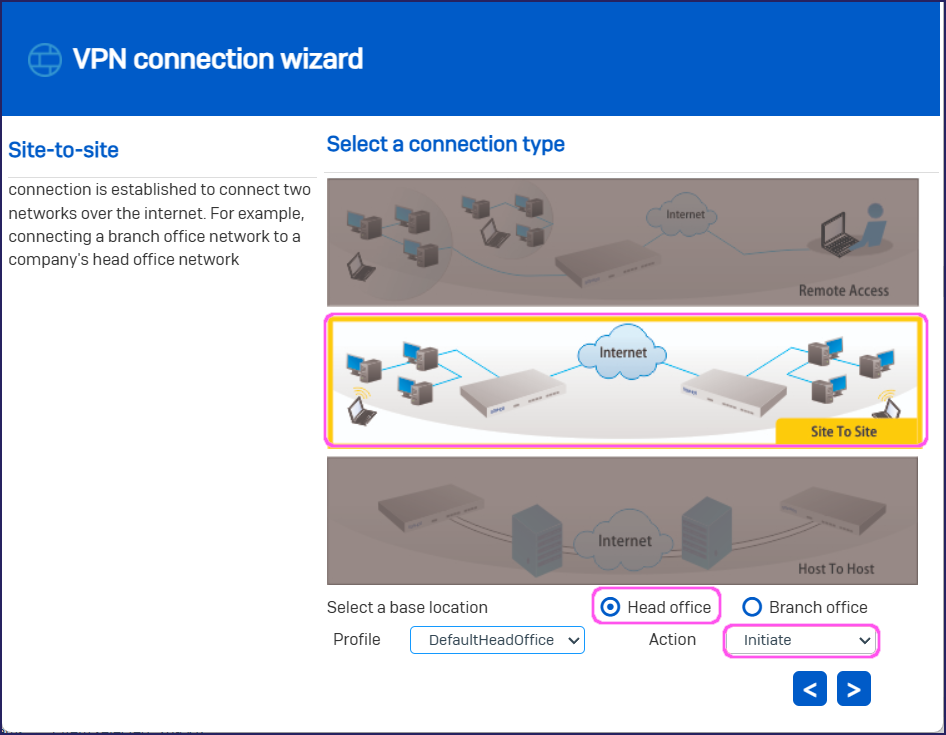
Select
 .
.In Authentication details, specify the following:
Authentication type: Select Preshared key.
Preshared key: Enter the preshared key you set in the Coro site-to site configuration, and then confirm the preshared key:
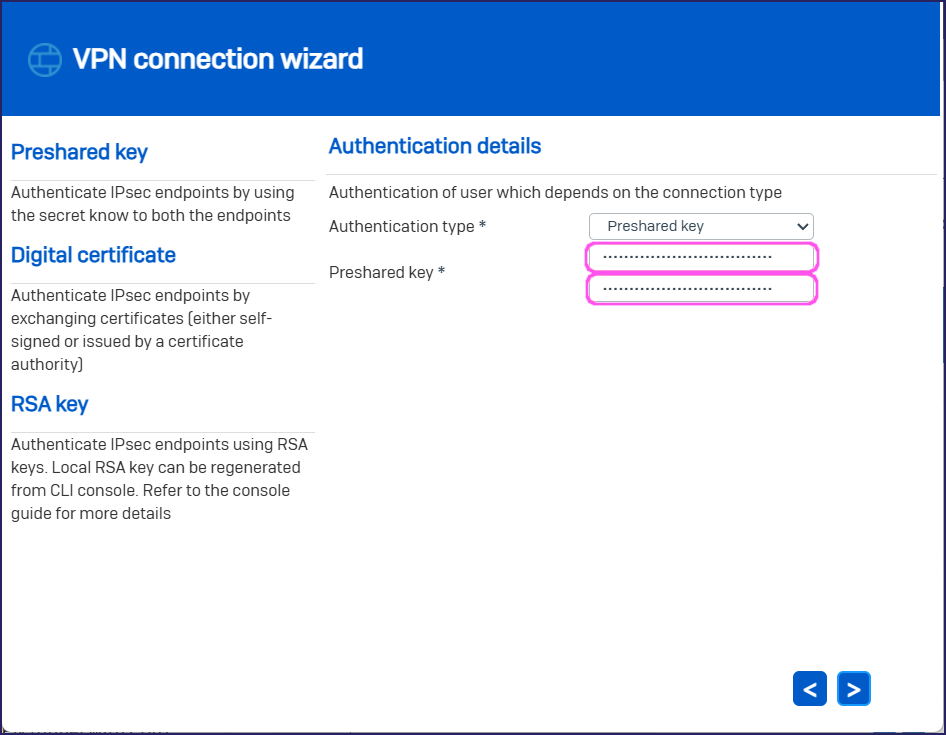
Select
 .
.In Local network details, specify the following:
Local WAN port: From the dropdown, select the local network port that you want to use for the VPN tunnel.
Local subnet: Select or add your local subnet for the VPN tunnel:
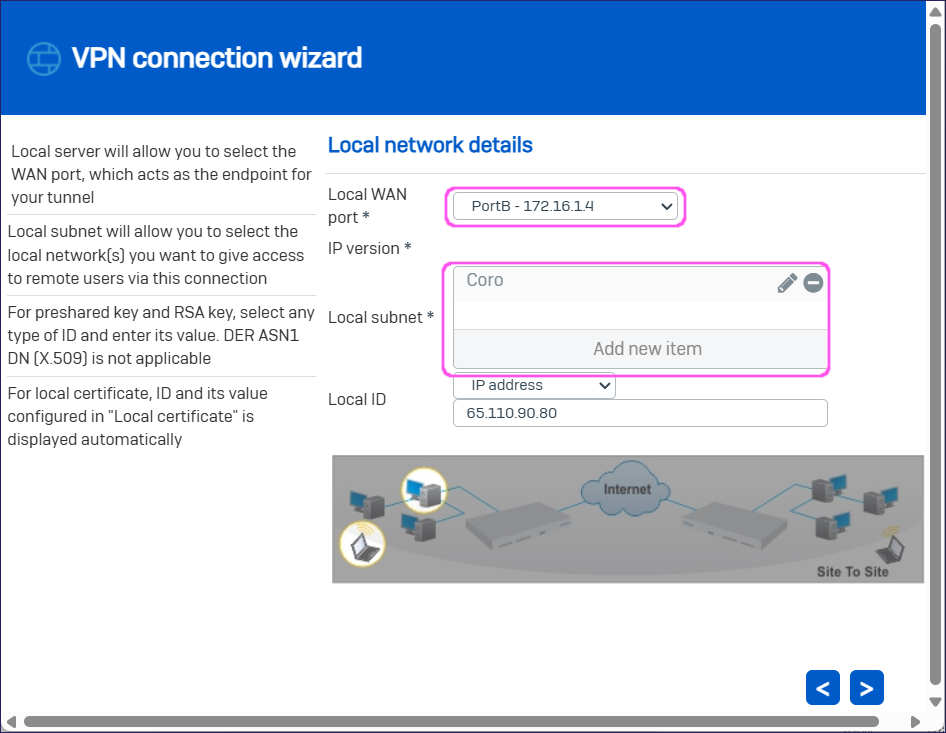
Then select Apply selected items.
Select
 .
.In Remote network details, specify the following:
Remote VPN server: Enter your Coro virtual office IP address.
IP version: Select IPv4.
Remote subnet: Enter 10.8.0.0/16, 10.9.0.0/16, 10.10.0.0/16.
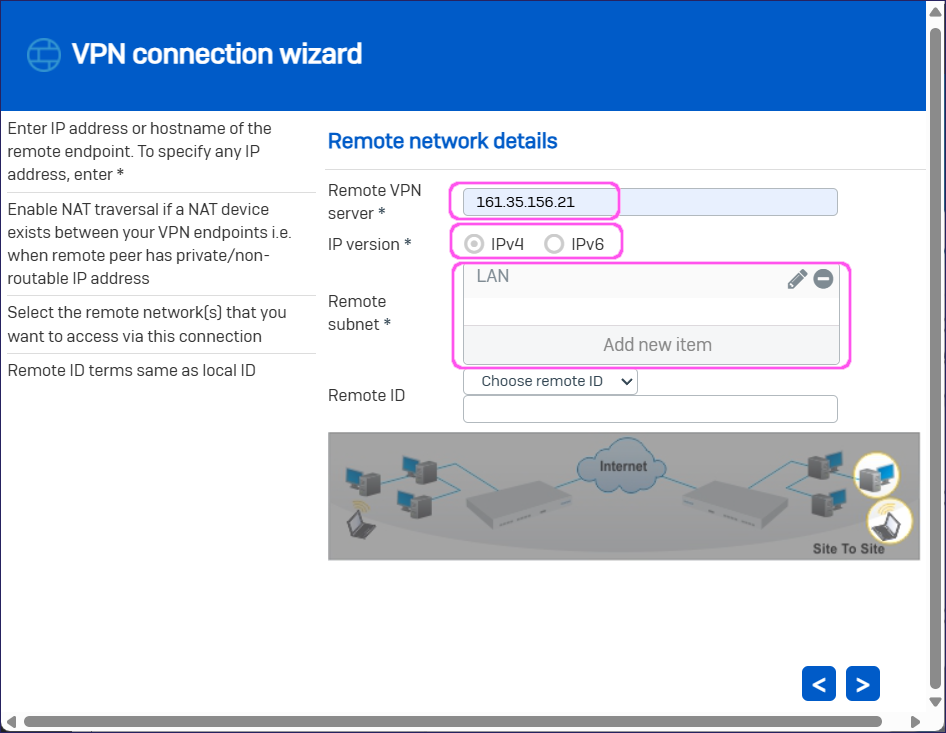
Select
 .
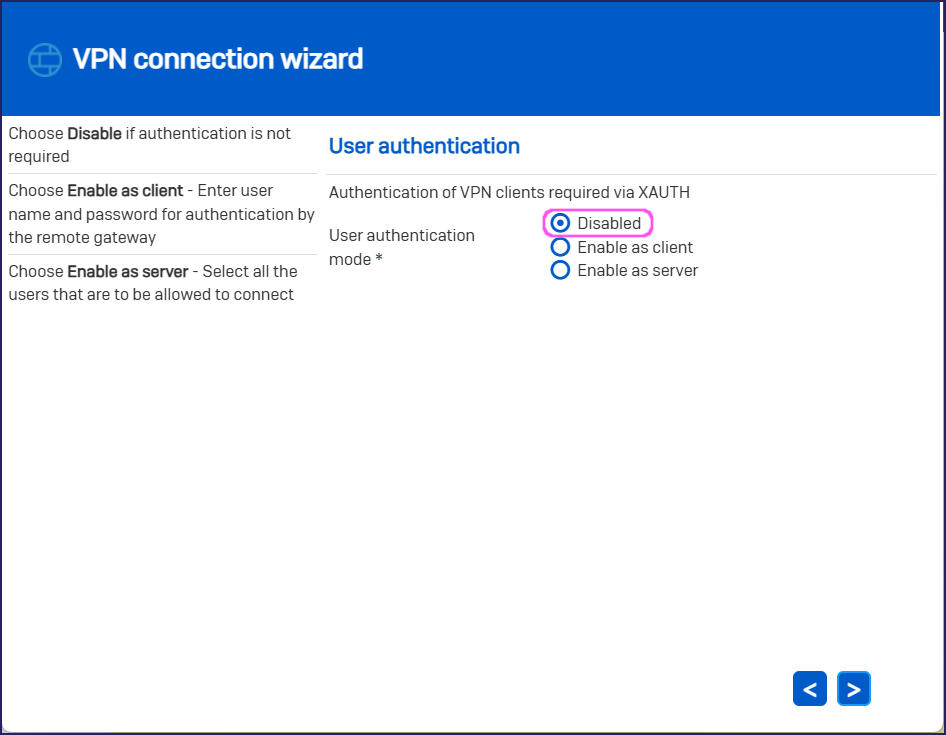
.In User authentication, specify the following:
- User authentication mode, select Disabled.
Select
 :
:
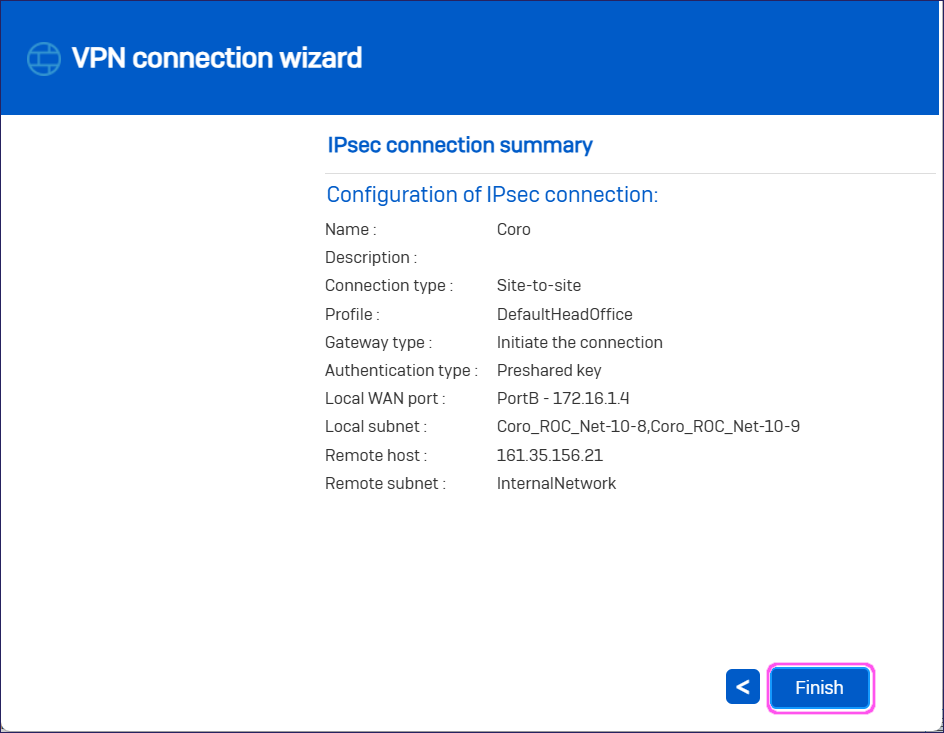
In IPsec connection summary, review the configuration and then select Finish:
Go to Site-to-Site VPN > IPsec, and locate the IPsec connection:
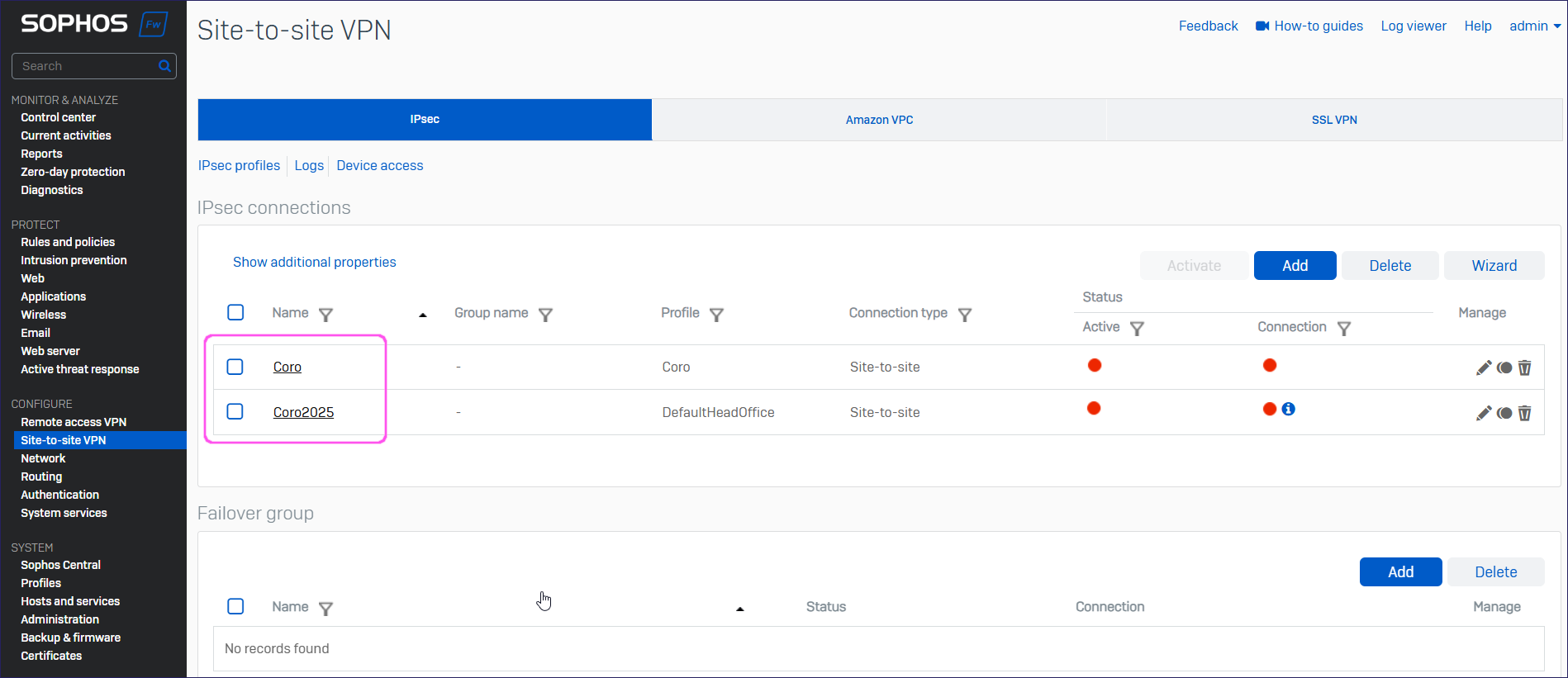
To activate the IPsec connection, select the relevant Status indicator:
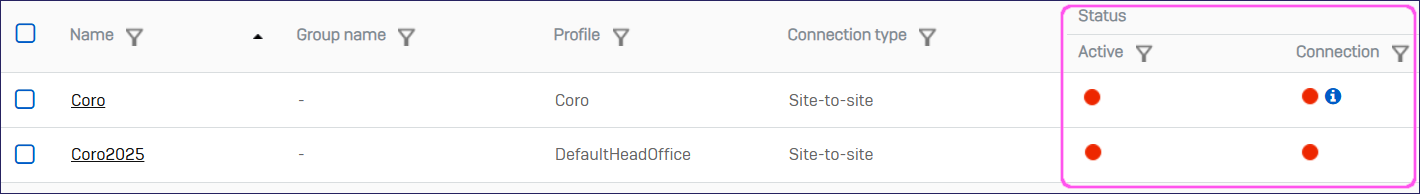
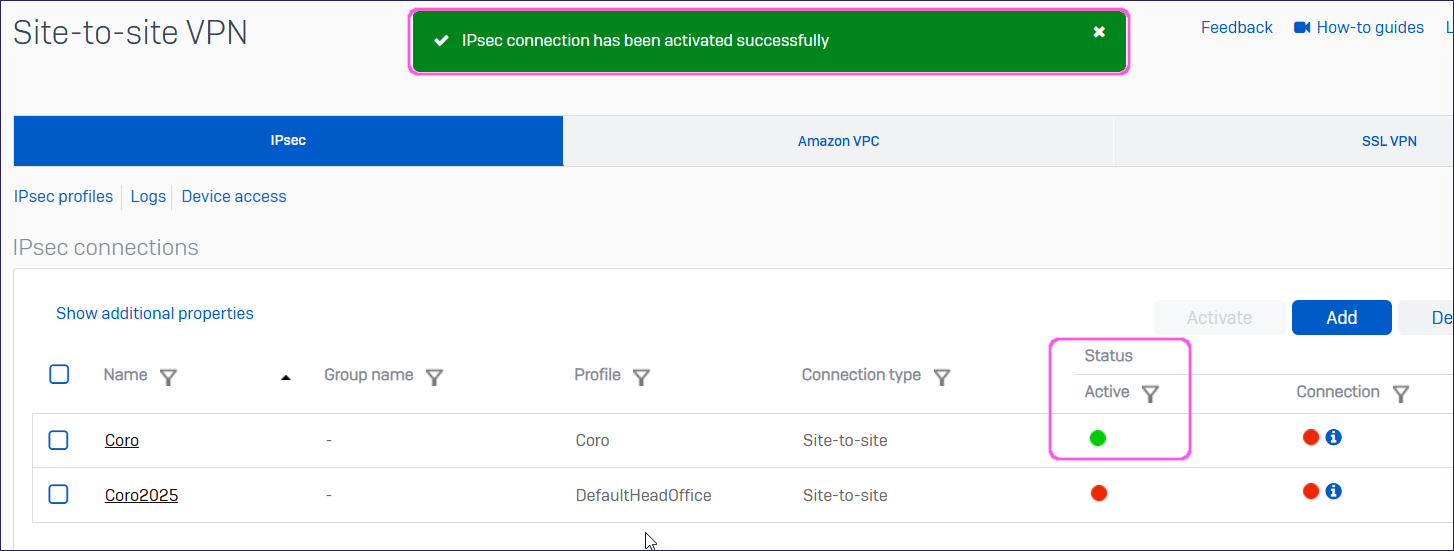
In the confirmation dialog, select OK:

Sophos displays confirmation that the IPsec connection is activated.
You must configure a static route and firewall policy in your Sophos configuration to allow Coro access to the subnet. Since each customer's LAN configuration may be unique, Coro cannot provide instructions. This guide describes establishing the site-to-site tunnel only.
After you have completed configuration of Coro Network and your Sophos firewall, test the connection from the Coro console:
- Sign in to the Coro console.
- Go to Control Panel > Network > Site-to-site tunnels.
- Select the three-dot menu adjacent to your tunnel configuration, then select Test tunnel to trigger a synchronization test.
- On completion of a successful test, Coro updates the Test status field to show Success.