The EDR Processes page compiles information on device processes executed within the organization. This centralized aggregation enables quick analysis and detailed investigation of specific processes, giving admin users with sufficient permissions visibility into potential security threats.
If a device loses network connectivity or the Coro Agent becomes inactive, Coro preserves the process data. After the device regains connectivity or the Coro Agent resumes operation, Coro makes this saved data accessible.
Coro retains customer process data for 90 days.
This article discusses the following topics:
To access the EDR Processes page:
Select the Processes tab:

Coro displays the Processes page, which lists all processes:
Select any process to view detailed process information.
The Processes page displays the following process information:
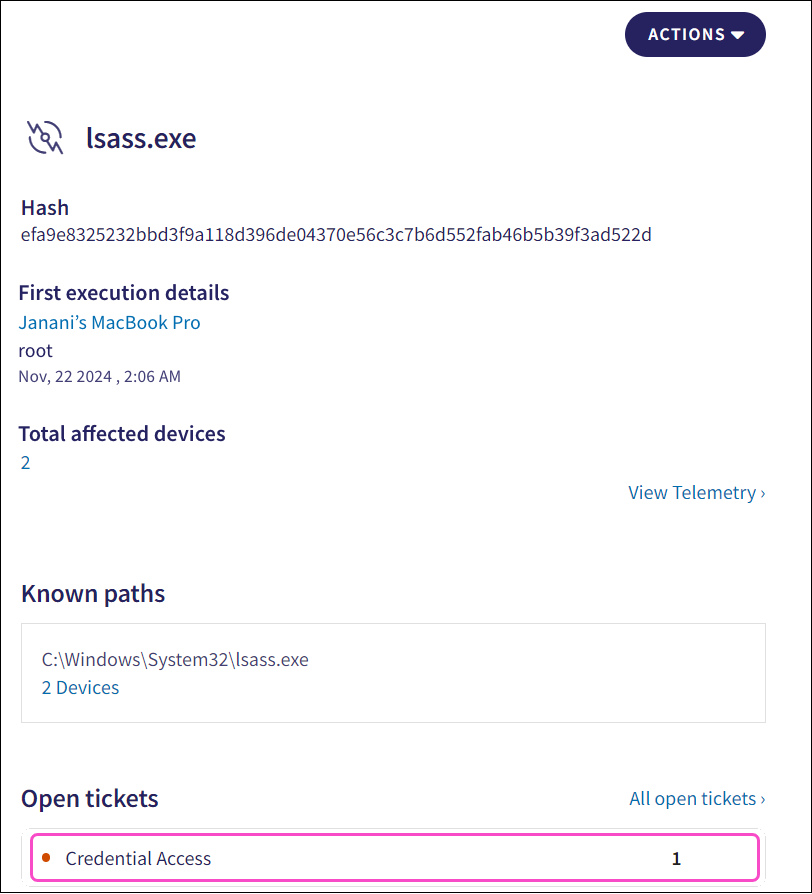
Hash: The unique process identifier hash value.
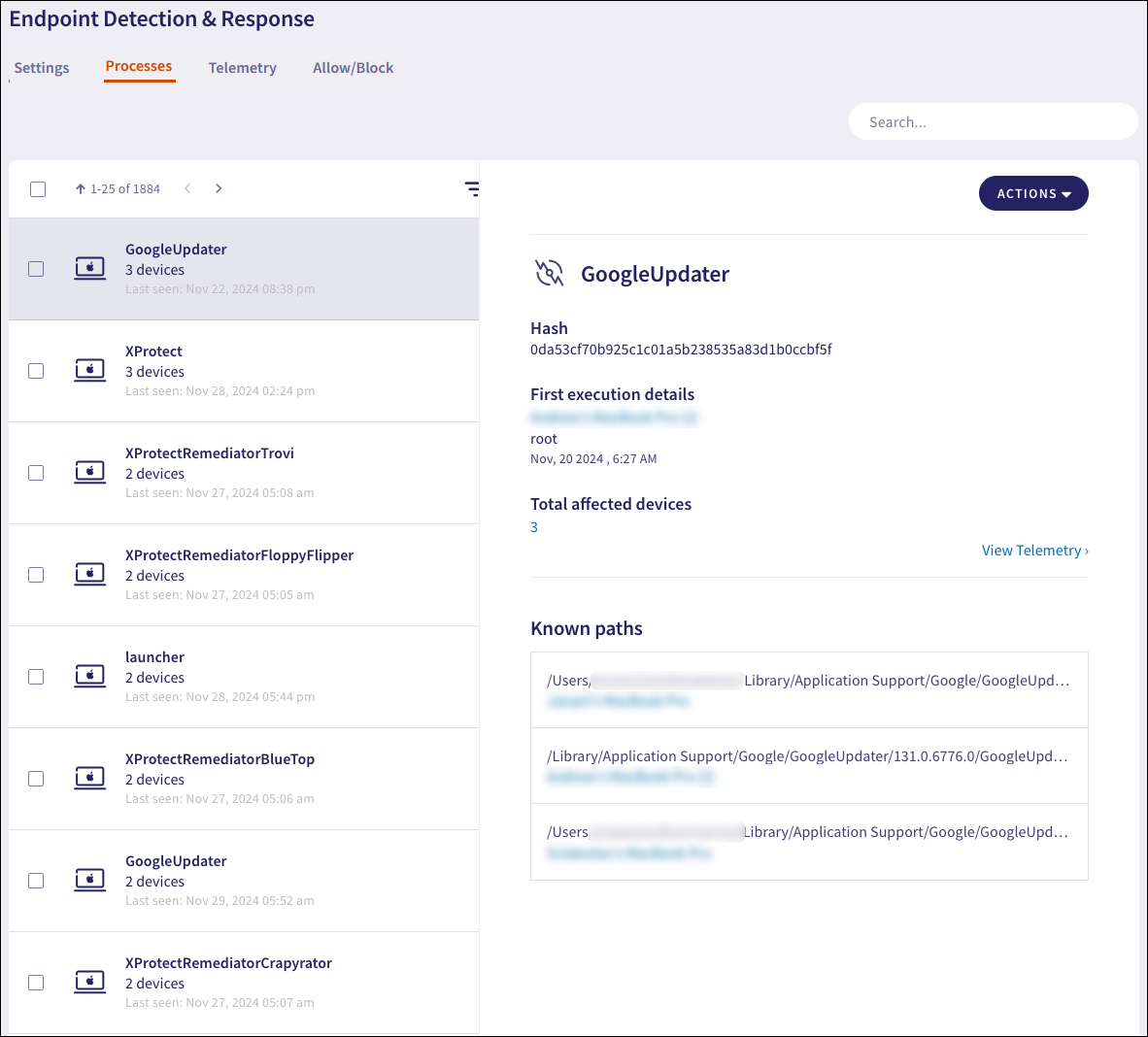
Select View Telemetry to display the Telemetry page, filtered by the process hash value:
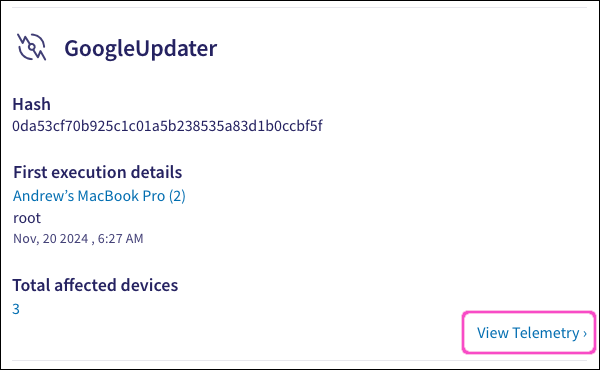
First execution details: Details about the process’s first execution:
Device name: The device that first executed the process.
User: The user account that first executed the process.
Timestamp: The date and time when the process was first executed.
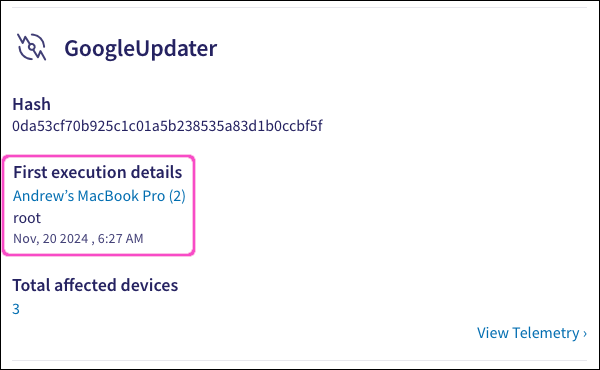
Total affected devices: The total number of monitored endpoint devices on which this process is running.
Select the devices counter to view the Devices page, filtered by the process hash value:
Known paths: All directory paths from which the process was executed. Each directory path includes the hostnames (devices) affected.
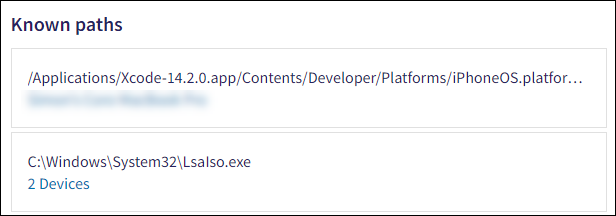
If a single device is affected, its name appears as a link to the Devices page below the directory path. If multiple devices are affected, Coro displays a counter showing the number of affected devices. This counter directs you to the Devices page, filtered by the process hash and directory path.
Process aliases (if applicable): If a process has more than one name, all aliases are displayed.

If a single device is affected, its name appears as a link to the Devices page below the directory path. If multiple devices are affected, Coro displays a counter showing the number of affected devices. This counter directs you to the Devices page, filtered by the process hash and directory path.
Coro does not display the Process Aliases section if a process has no additional aliases.
Open tickets: A list of all open EDR tickets associated with this process, including a count for each ticket type.
Select All Open Tickets to view the Ticket log, filtered by the process hash value:

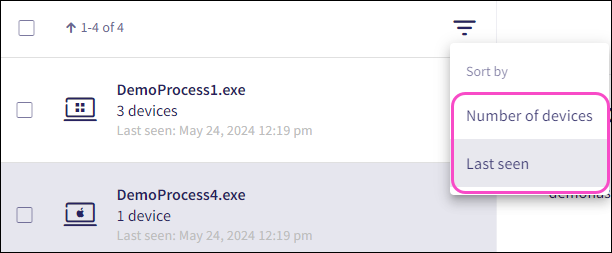
Sort the Processes page by the following fields:
Number of devices: The number of devices associated with a particular process hash.
Last seen: The timestamp at which the process was last seen.
Each process listed on the Processes tab has a set of actions you can apply to a selected process:
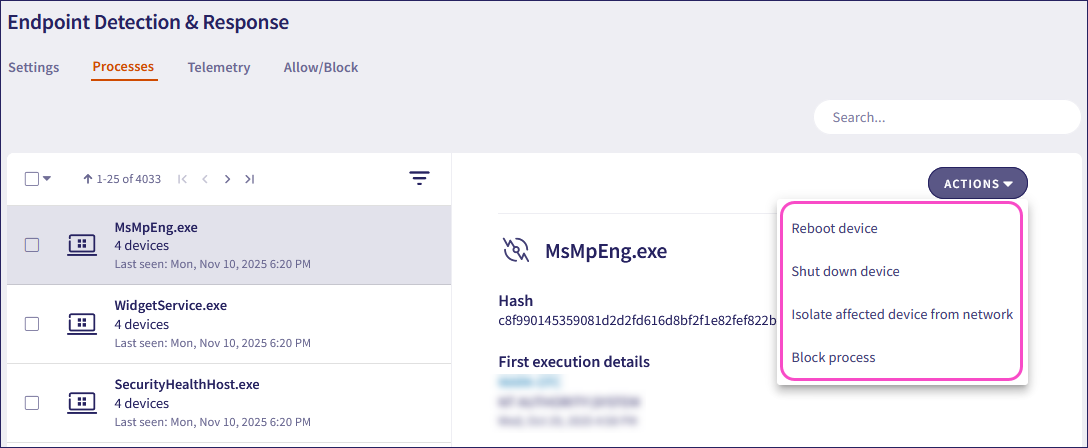
Perform the following process actions:
Reboot device(s): Reboots the affected device(s).
Shut down device(s): Shuts down the affected device(s).
Isolate affected device(s) from network: Used in the case of severe attacks. The action isolates the affected device(s) from the network. An isolated device cannot communicate with any resource on the network or the internet. Communication with the Coro servers remains functional while the device is isolated.
If MacOS Agent v2.1 or higher/Windows Agent v2.2 or higher is not installed, the Isolate affected devices from network action is not available. Isolated devices are only be able to communicate with Coro's servers.
Reconnect isolated devices to the network from the Devices page.
Isolate a process if at least one of the associated devices has either:
MacOS Agent v2.1 or higher installed.
Windows Agent v2.2 or higher installed.
Block process: Blocks a process and adds it to the Endpoint Security and EDR blocklist:
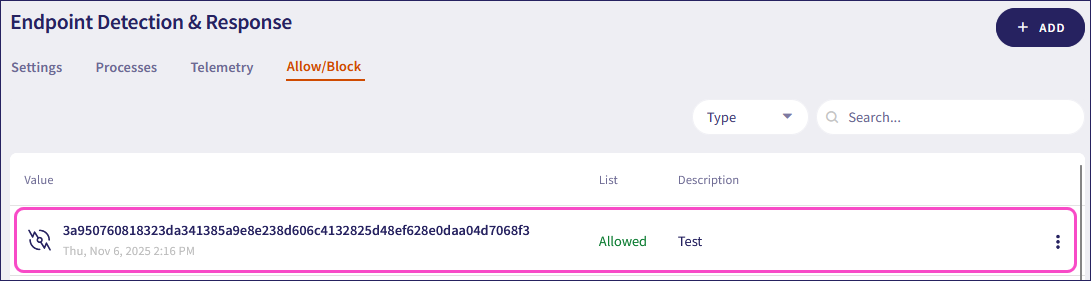
Coro labels the process as Blocked in the Processes list. When you select a blocked process, Coro displays the status in the format: Process blocked on MMMM DD, YYYY.
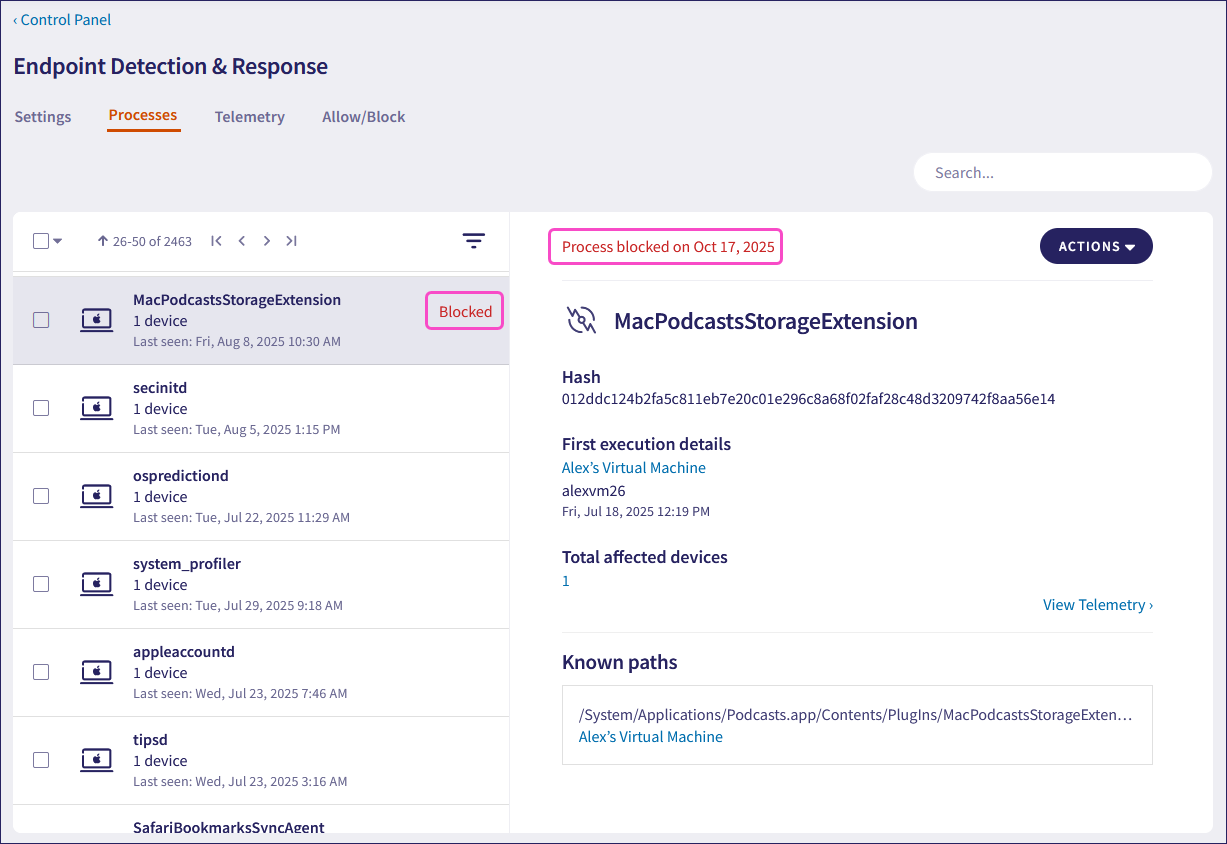
For further information on blocking processes, see EDR Allow/Block lists and Endpoint Security Allow/Block lists.
You can perform additional process actions from the Devices page.
Apply mass actions to multiple processes simultaneously. The following mass actions are available:
Block processes
Unblock Processes
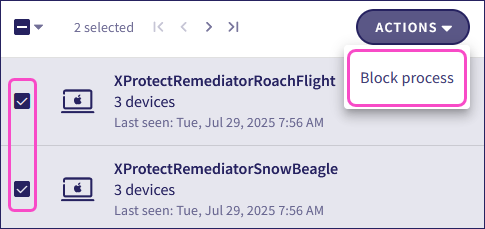
To apply a mass action to multiple processes:
Select the required processes from the process list.
Select ACTIONS > Block processes/Unblock Processes:
Coro displays a confirmation dialog:
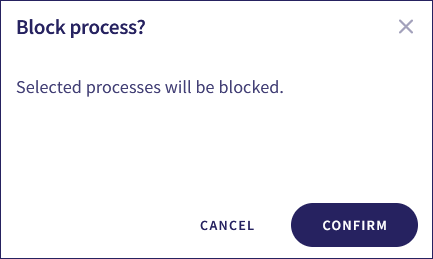
Select CONFIRM.
The selected mass action is performed, and a confirmation message appears:
Use the Search field to search and filter telemetry information in the following ways:
Perform a prefixed search using the following terms:
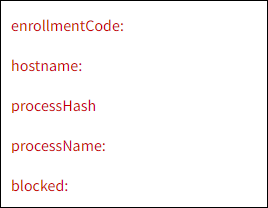
EnrollmentCode: The Coro device ID.
Hostname: The name of the device(s) linked to a process.
ProcessHash: The unique process identifier.
ProcessName: The name of the process.
Blocked: Enter true to search for all blocked processes.
Prefixed searches use exact matches for the selected prefixed term value entered.
Perform a free text search without using prefixed terms.
EDR tickets include details about the process that triggered a detection rule.
To view additional information about EDR tickets, see Ticket types for EDR.
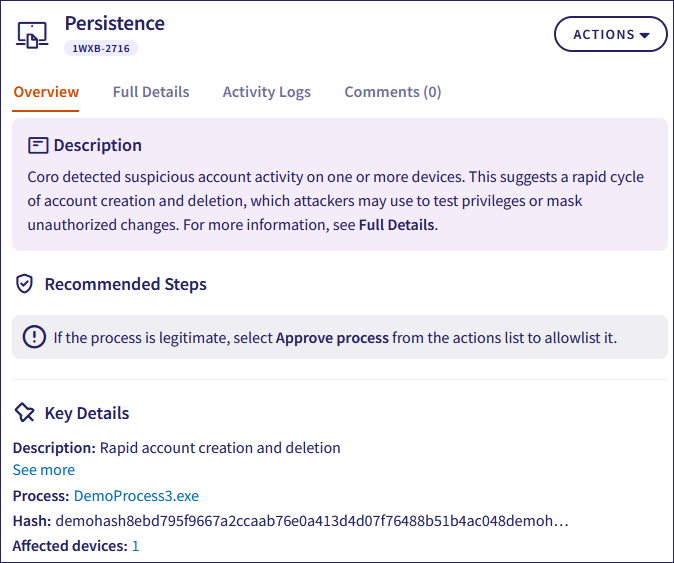
Select the Overview tab to view the following process-related information in the Key Details section:
Description: The detection rule that triggered the EDR ticket. Select See more to view the rule description.
Process: The executable file that triggered the EDR ticket. Select the process to open the Processes page filtered by hash.
Hash: The unique process identifier.
Affected devices: Select the device count to open the filtered Devices page showing affected devices for the EDR ticket.
Select the Full Details tab to view the following additional process-related information:
Mitre: This section lists MITRE ATT&CK techniques and tactics associated with the security incident. Each entry includes the tactic category and a detailed description of the technique. Select a technique ID to view the entry in the MITRE ATT&CK database.
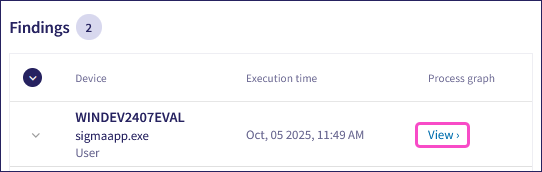
Findings: This section displays additional details about the process that triggered the EDR ticket:
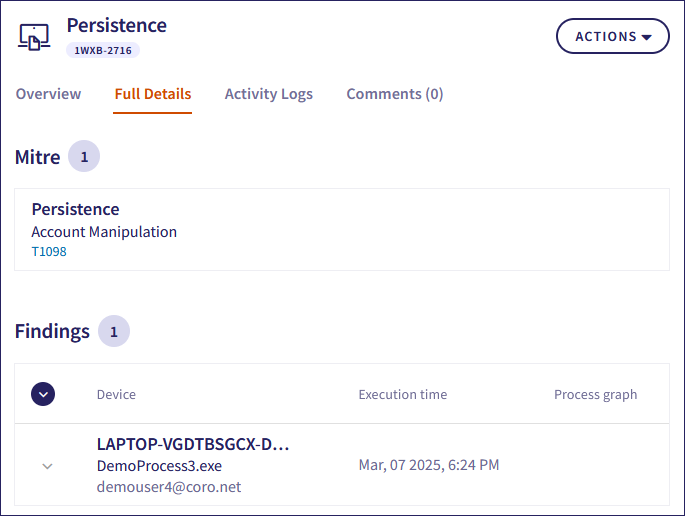
Coro lists execution times for the process and any related parent or child processes.
If available, select View to open the process graph visualizer showing parent-child relationships for the process. For more information, see Process graph.
The process graph link appears only if Coro can access data to generate the visualization. If the data is unavailable, the View link is hidden.
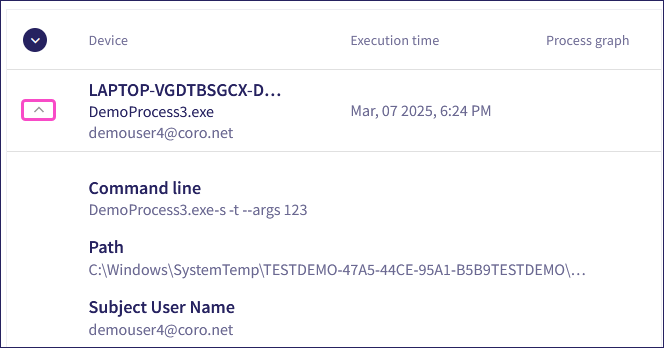
Select the dropdown adjacent to each finding to view the following additional details:
Affected User: (Credential Access, Persistence, and Privilege Escalation tickets) The user account that was the target of the action.
Command line: The full command used to start the process.
If the command line is base64 encoded, Coro automatically decodes and displays the text value.
Path: The directory path of the malicious process image file.
Subject User Name: (Credential Access, Persistence, and Privilege Escalation tickets) The account that performed the action.
Target Group: (Credential Access, Persistence, and Privilege Escalation tickets) The group that was modified.
The process graph visualizes the process tree for the selected EDR ticket, highlighting both malicious and legitimate processes detected by Coro. Navigate connected process nodes to explore parent and child relationships and view related details. This enables quicker assessment of whether the investigated process is malicious.
Coro supports process graphs for Windows and macOS devices.
The process graph is available only if Coro can access data for the selected process.
To view the process graph for an associated EDR ticket:
Select the EDR ticket.
Go to the Findings section, locate the process record, and select View under the Process graph header:
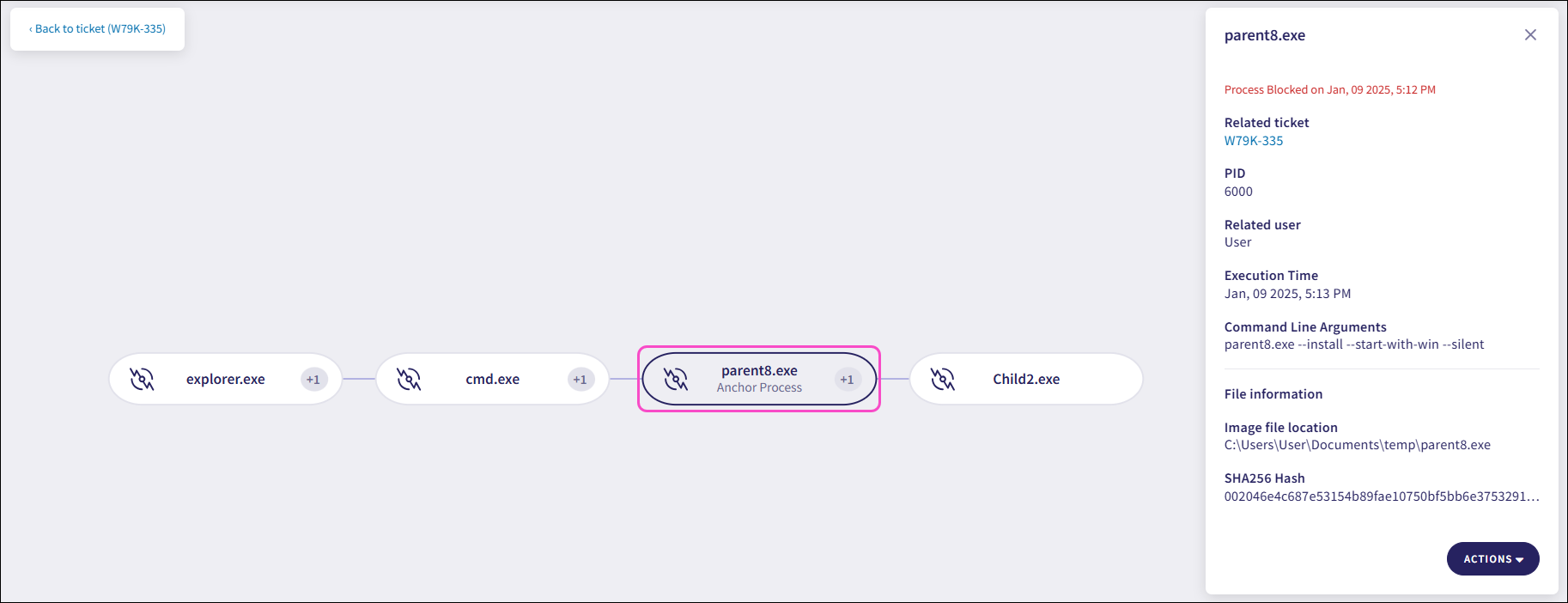
Coro displays the process graph with the Anchor Process node selected:
 Important
ImportantCoro designates the anchor process node as the process selected from the Findings section of the EDR ticket.
The anchor process is the central node in the process graph. It links parent processes (showing all processes leading to the anchor process) to child processes (those initiated by it or its descendants). This provides a starting point for your investigation, enabling you to trace the lineage and impact of related processes.
Related process counters show the number of additional processes linked to the selected process node:
Each process graph node displays a set of properties.
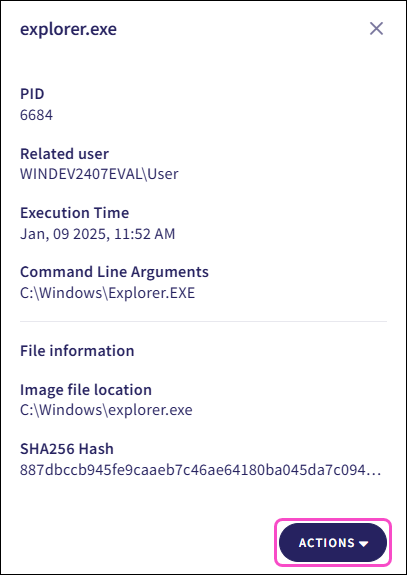
Select a process node to see the following process properties:
Related ticket: Select the link to go back to the related ticket.
PID: The unique process identifier assigned by the operating system (OS).
Related user: The user account that executed or interacted with the process.
Execution Time: The timestamp when the process executed.
Command Line Arguments: The full command used to start the process, including the path to the executable file and any passed arguments or parameters.
Image file location: The process image directory path of the executable file that started the process.
SHA256 Hash: The SHA-256 hash value of the selected process.
Each process node includes available actions. To access these actions, select Actions for the selected process node:
The table below describes the outcome of each process node action:
| Action | Outcome |
|---|---|
| Block process | Blocks process execution. Coro adds an entry to the EDR and Endpoint Security blocked list. For more information, see Endpoint Security Allow/Block lists, EDR allowlist and blocklist, and EDR Processes. |
| Allow process | Prevents EDR ticket generation by marking the non-system process as safe. Related process information is not collected in the EDR Telemetry and Process tabs. |