Ticket types for Endpoint Security
The Linux Agent currently supports only Malware on endpoint tickets. Other ticket types discussed in this article apply to devices running Windows or macOS Agents.
Coro generates tickets for protected devices when it identifies the following security vulnerabilities:
- Apple mobile file integrity disabled
- Development mode enabled
- Device password missing
- Firewall disabled
- Forbidden Wi-Fi Connection
- Gatekeeper disabled
- Infected process
- Malware on endpoint
- Non-genuine Windows Copy
- System integrity protection disabled
- UAC notification missing
- Unencrypted endpoint drive
- VSS backup protection
- WiFi Phishing
Apple mobile file integrity disabled
Coro detected that Apple Mobile File Integrity (AMFI) is disabled on the device. AMFI helps maintain the integrity and security of executable code and system files on Apple devices. When AMFI is disabled, applications can be compromised with malicious code.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Apple Mobile File Integrity Disabled policy.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Enable Apple Mobile File Integrity | Enable Apple Mobile File Integrity on this device and close ticket. |
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
Development mode enabled
Coro detected that Development mode is enabled on the device. Development mode is a device configuration that is intended for use by developers and advanced users. Enabling Development mode can expose the device to potential security vulnerabilities.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Development mode policy.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Disable developer mode | Remotely disables Development mode on the device. |
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
Device password missing
Coro detected the password is missing on the device.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Device Password Missing policy.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
When Coro creates a ticket, it sends an email with ticket details and remediation options to all admin users configured to receive notifications. For more information about receiving notifications, see notifications.
When you select an action, Coro opens the Coro console where you can review and confirm it. Actions include:
- ADD POSTURE POLICY: Add the Remote password and session locking policy for Windows or macOS, depending on the device in the ticket. Close this and related open tickets for the device.
- DISREGARD AND CLOSE: Close this and related open tickets for the device without further action.
Firewall disabled
Coro detected that the firewall on the device is disabled. A firewall is a software or hardware-based security mechanism that monitors and controls network traffic on a device, based on predefined security rules.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Firewall disabled policy.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Enable firewall | Coro closes the ticket and enables the firewall on the device. |
When Coro creates a ticket, it sends an email with ticket details and remediation options to all admin users configured to receive notifications. For more information about receiving notifications, see notifications.
When an action is selected, you are taken to the Coro console to review and confirm the action. The actions include:
- ADD POSTURE POLICY: Add the Firewall disabled policy for Windows or macOS, depending on the device in the ticket. Close this and related open tickets for the device.
- ENABLE FIREWALL: Enable the firewall on the device. Close this and related open tickets for the device.
- DISREGARD AND CLOSE: Close this and related open tickets for the device without further action.
Forbidden Wi-Fi Connection
Coro detected a blocked public Wi-Fi network. A device is forbidden from connecting to a blocked public Wi-Fi network.
Coro creates and remediates a ticket according to the selected Wi-Fi connectivity policy. For further information, see Wi-Fi connectivity policies.
Forbidden Wi-Fi Connection tickets have no available actions.
Gatekeeper disabled
Coro detected that Gatekeeper is disabled on the device. Gatekeeper is a security technology that helps verify only trusted software runs on the device.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Gatekeeper Disabled policy.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Enable Gatekeeper | Enable Gatekeeper on this device and close ticket. |
Infected process
Coro detected a process group on the device that exhibited malicious or suspicious characteristics. Coro terminates the process group immediately and creates an open ticket for admin review. After 10 days Coro automatically closes the ticket. Admin users can review the ticket and choose to approve the process group or initiate a remote malware scan on the device.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Approve process group | Approve the process group on all devices in the same workspace. Coro marks identical process groups as safe and does not terminate them. |
| Remote scan for malware | Initiate a remote malware and ransomware scan on the device. |
| Stop remote scan for malware | Stop an active remote malware and ransomware scan on the device. |
Coro approves a process group based on the collective processes it contains, not on the order of the processes within the group.
Malware on endpoint
Coro detected potential malware on the device. Coro automatically moves files detected as malicious to a quarantine folder and creates an open ticket for admin review. After 10 days Coro automatically closes the ticket. Admin users can review the ticket and either approve or discard the quarantined files. They can also configure Coro to ignore the original folder that contains the flagged file.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Exclude folder from malware scan | Exclude folder specified in the ticket from future malware and ransomware scans. Admin users can close the current ticket and all related tickets. |
| Remote scan for malware | Initiate a remote malware and ransomware scan on the device. |
| Stop remote scan for malware | Stop an active remote malware and ransomware scan on the device. |
| Discard this file | Treat the file as malicious and remove it from the device. Coro marks identical files as malicious and automatically deletes them in the future. Admin users can close the current ticket and all related tickets. |
| Approve this file | Approve the file on all devices in the same workspace. Coro removes it from quarantine (if applicable) and marks future identical files as safe. Admin users can close the current ticket and all related tickets. |
Non-genuine Windows Copy
Coro detected a non-genuine copy of Windows on the device.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Non-genuine Windows Copy policy.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
System integrity protection disabled
Coro detected that System Integrity Protection (SIP) is disabled on the device. SIP is a security technology that helps protect the device from malicious software that could modify protected files and folders. It restricts the root user account and limits the actions that the root user can perform on protected parts of the operating system.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new System Integrity Protection Disabled policy.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
UAC notification missing
Coro detected missing UAC (User Access Control) notifications on the device.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new UAC Notification Missing policy.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Enforce UAC notification | Enable UAC on the device. Admin users can close the current ticket and all related tickets. |
When Coro creates a ticket, it sends an email with ticket details and remediation options to all admin users configured to receive notifications. For more information about receiving notifications, see notifications.
When an action is selected, you are taken to the Coro console to review and confirm the action. The actions include:
- ADD POSTURE POLICY: Add the UAC notifications disabled policy for Windows or macOS, depending on the device in the ticket. Close this and related open tickets for the device.
- ENABLE UAC NOTIFICATIONS: Enable UAC on the device. Close this and related open tickets for the device.
- DISREGARD AND CLOSE: Close this and related open tickets for the device without further action.
Unencrypted endpoint drive
Coro detected an unencrypted drive on the device.
Coro creates and remediates a ticket according to the selected policy action. For further information, see Creating a new Unencrypted Endpoint Drive policy.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Encrypt drive | Encrypts the hard drive of the device. Encryption keys are stored on both the device (by BitLocker) and on the Coro servers. |
| Allow no encryption | The hard drive of the device is allowlisted, and is treated as not containing any sensitive data that requires disc encryption. Admin users can close the current ticket and all related tickets. |
When Coro creates a ticket, it sends an email with ticket details and remediation options to all admin users configured to receive notifications. For more information about receiving notifications, see notifications.
When an action is selected, you are taken to the Coro console to review and confirm the action. The actions include:
- ENCRYPT DRIVE: Encrypt the device hard drive. Close this and related open tickets for the device.
- ALLOW NO ENCRYPTION: Allowlist the device hard drive. Close this and related open tickets for the device.
- DISREGARD AND CLOSE: Close this and related open tickets for the device without further action.
VSS backup protection
When VSS (Volume Shadow Copy Service) backup protection is enabled, Coro enforces backup snapshots every four hours and blocks processes that exhibit risks to the backup (see Using VSS backup protection on your Windows endpoints). Coro displays the process that attempted to manipulate the VSS backup files under the Suspected malicious process field in the ticket's Full Details section:
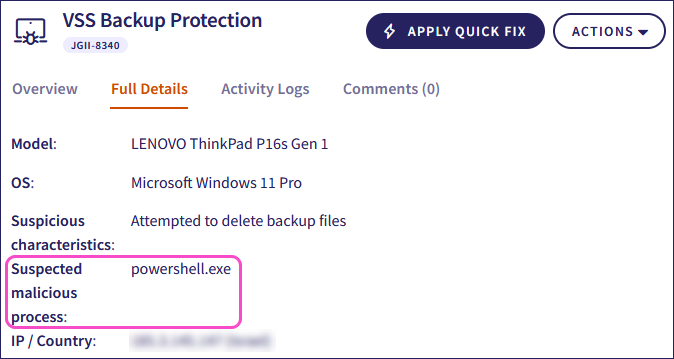
Coro automatically closes VSS Backup Protection tickets after 10 days.
When you remove a device from protection, Coro automatically closes all open tickets associated with the device.
Coro does not identify the process responsible for attempting to manipulate the VSS backup files on Windows Server 2016.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |
| Remote scan for malware | Initiate a remote malware and ransomware scan on the device. |
| Stop remote scan for malware | Stop an active remote malware and ransomware scan on the device. |
WiFi Phishing
Coro detected a connection from the device to a wireless network that might be unsafe or involved in phishing or man-in-the-middle attacks. Coro does not perform auto-remediation and creates a ticket for admin user review that remains open for two weeks.
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. |
| Re-open | Reopen this ticket for admin user intervention and manual remediation. |