Policies
Coro's Cloud Security module enables admin users to configure user access permissions for connected cloud applications and threat detection policies for specified users or user groups.
To configure cloud security policies:
From the sidebar, select Control Panel:
Select Cloud Security:
Select the Policies tab:
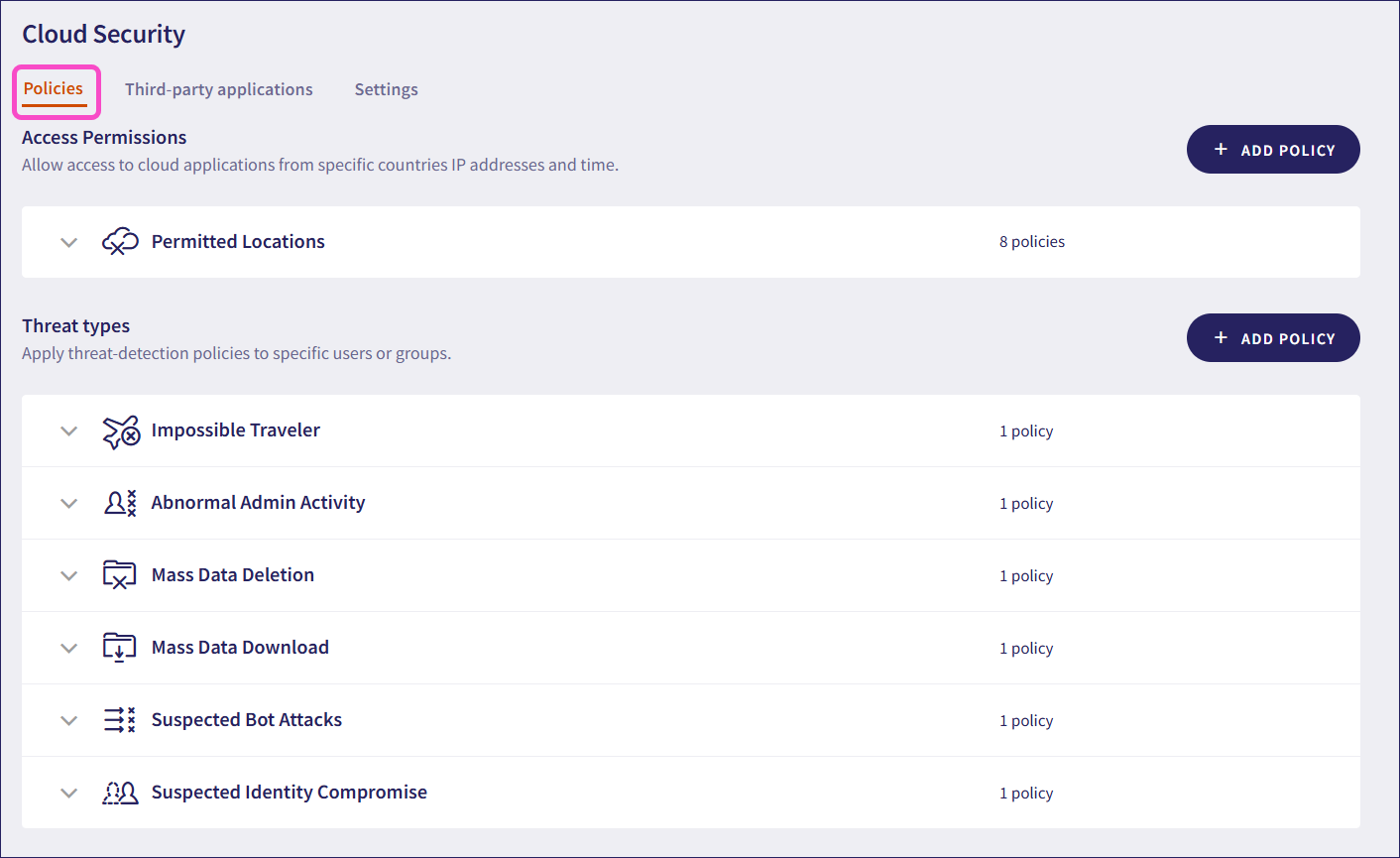
Use this tab to configure:
Access permissions
Coro supports the ability to set access permissions for connected cloud applications. Admin users with sufficient permissions can allow access to a cloud application based on whether a user meets a defined set of criteria.
Coro creates an Access permissions violation ticket if a user successfully logs into a protected service from an origin in violation of the configured access policy.
For Coro to monitor and report security issues, at least one cloud application must be connected.
To see a list of supported cloud applications, see Introducing cloud security.
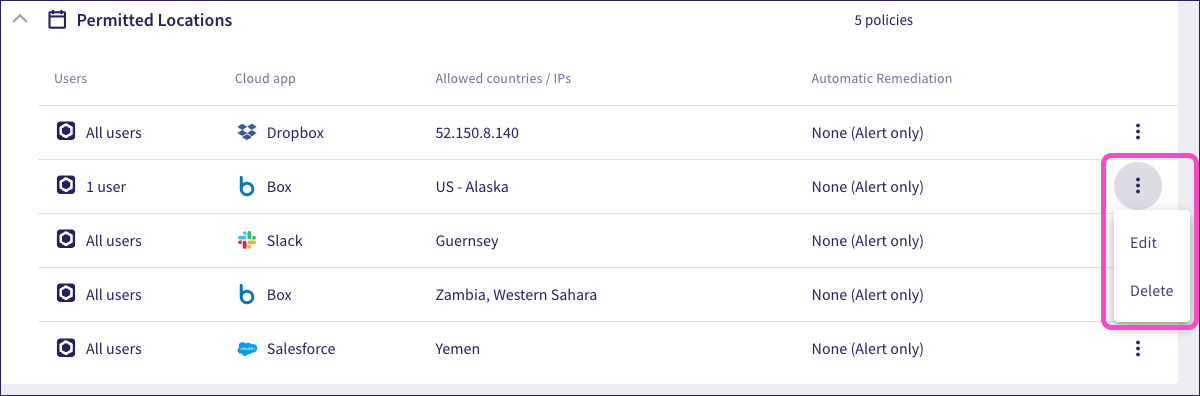
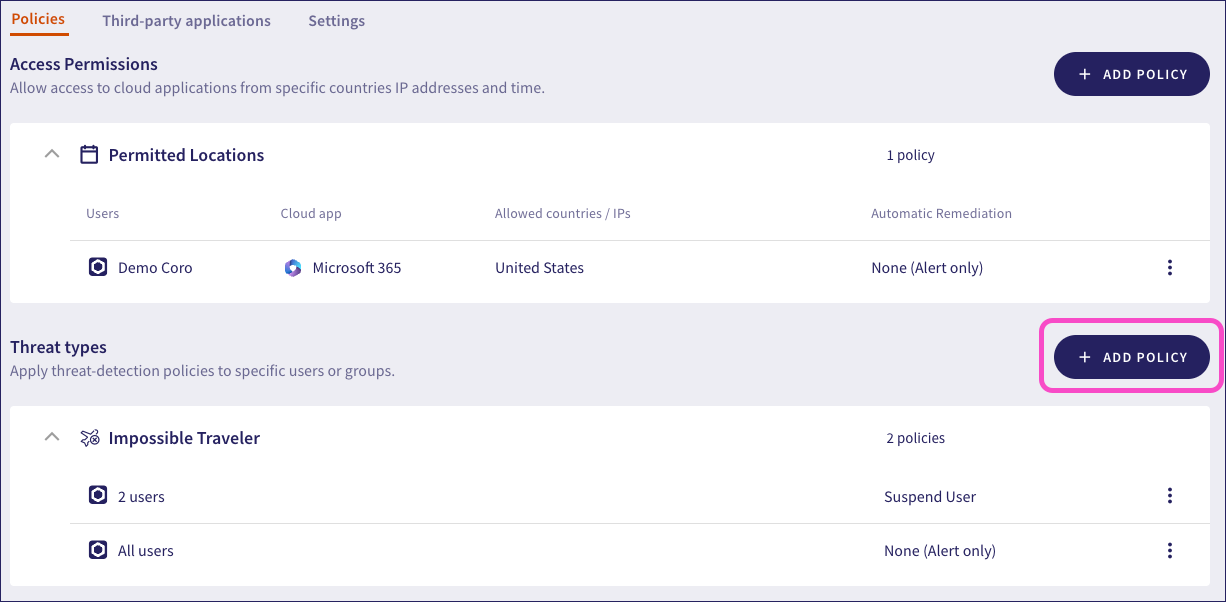
To view the currently configured access permissions, select the Permitted Locations dropdown:
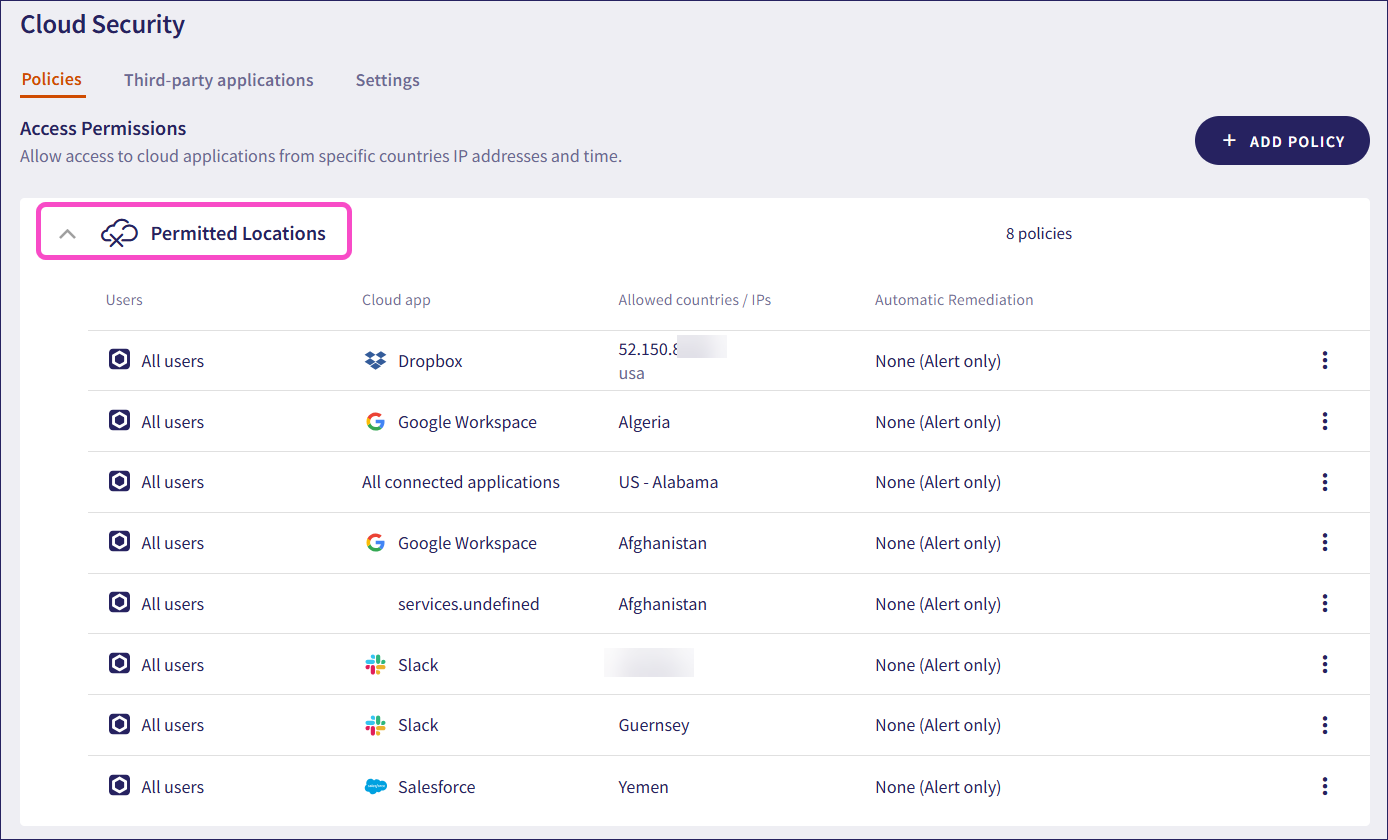
Coro displays each access permission policy, showing:
- Users: The users or user groups that this policy affects.
- Cloud app: The cloud application that this policy affects.
- Allowed countries/IPs: The locations (countries and/or US states) or IP addresses that this policy allows. IP addresses can have short descriptions below them.
- Automatic Remediation: The type of automatic remediation Coro applies if a user attempts to access the named cloud application from a location or IP address not listed.
Configuring new access permissions
To configure new access permissions for a connected cloud application:
In Access Permissions, select + ADD POLICY:
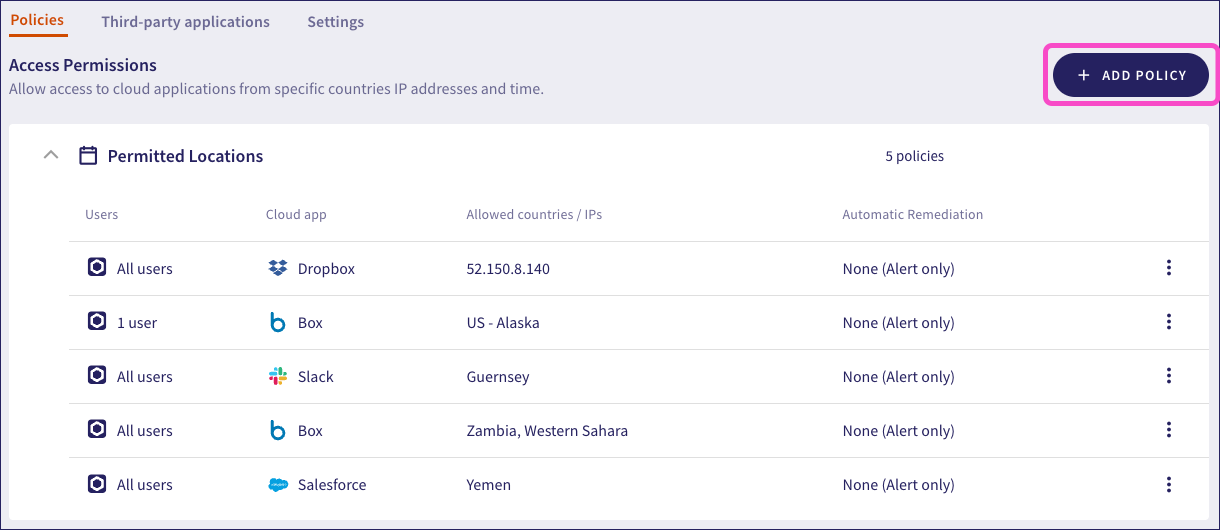
Coro displays the Create access policy dialog:
Select the cloud application for your policy:

In Allow access based on, select from the following options:
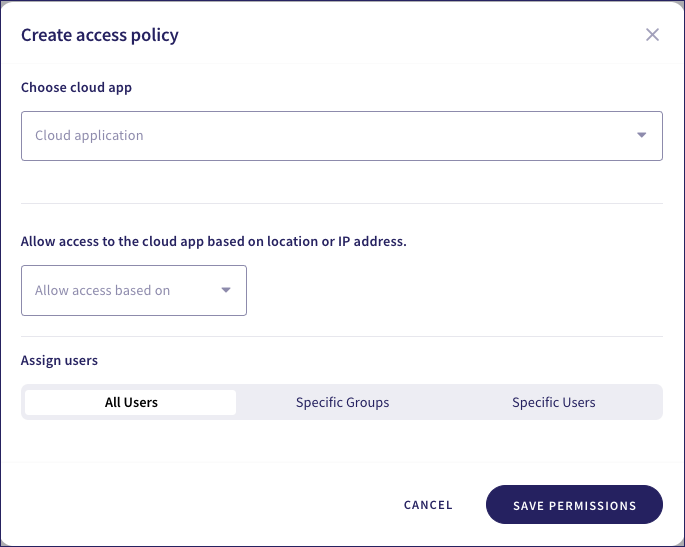
IP Address: Restricts access to a defined range of IP addresses. Enter the allowed IP addresses into the IP Addresses field and provide an optional short description:
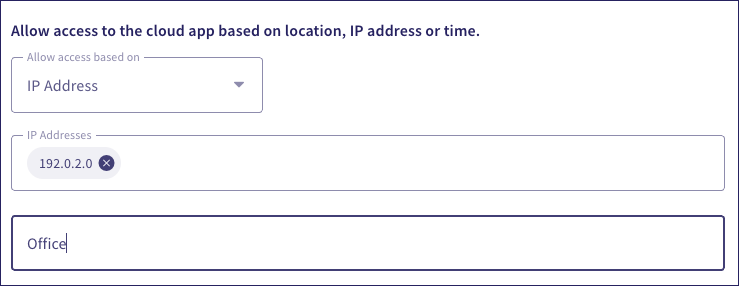
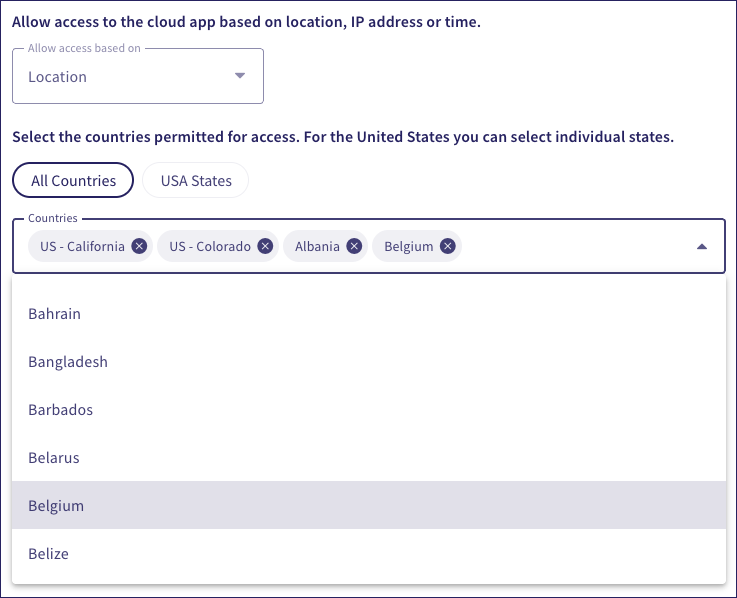
Location: Restricts access to named countries or US states. Select either All Countries or USA States:
US state permissions are independent of country permissions. You can select several countries and/or states. If United States is selected as a Country then permissions apply to all US states.
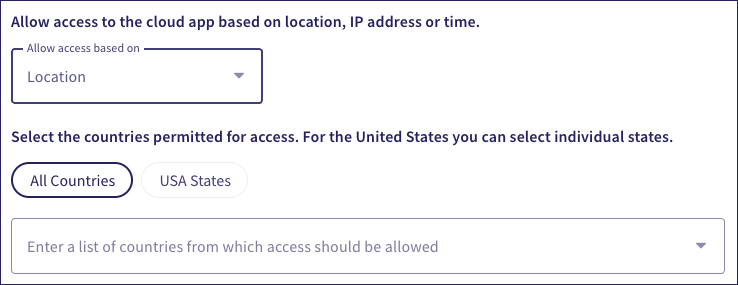
Coro displays a list of countries or US states based on your selection. Select the US states and/or countries to allow access from:
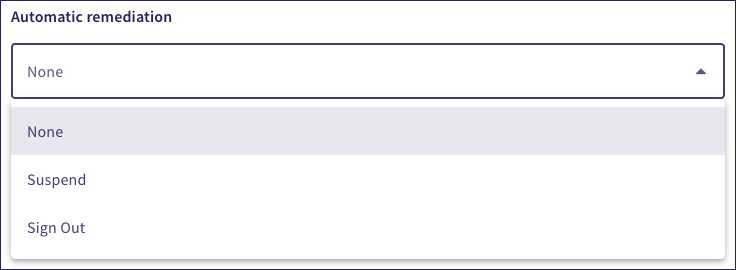
Set the automatic remediation Coro applies when a user does not meet the permission criteria, listed from least to most restrictive:
None: No remediation is applied.
Sign out: The user is signed out.
Suspend: The user account is automatically suspended.
When a user attempts to sign in, Coro evaluates all access permission policies that apply to that user. If multiple policies apply, Coro enforces the most restrictive automatic remediation.
In all cases, Coro creates a ticket to alert admin users to the event.
Select the users or groups to assign to this policy:
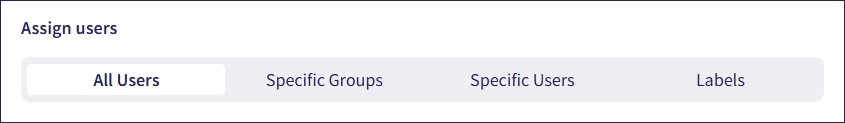
All Users: The new permission applies to all protected users.
Specific Groups: The new permission applies to a named group within the corresponding cloud application.
When a user belongs to several groups, they inherit the collective permissions of all those groups.
Specific Users: The new permission applies to users within the application, specified by their email addresses.
You can assign access permissions to existing admin users within the corresponding cloud application.
Select SAVE PERMISSIONS to save your changes.
When a user belongs to All Users and one or more specific groups, Coro evaluates all applicable access permission policies and applies the most restrictive automatic remediation (Suspend).
For example, if All Users is configured to suspend access outside the US and a user group allows access from Germany with remediation set to None, the user can sign in from the US and Germany but is suspended if they sign in from any other country.
Editing and deleting existing access permissions
Admin users with sufficient permissions can edit and delete existing access permissions.
To edit or delete existing access permissions for a connected cloud service, select the corresponding action from the three-dot menu:
Select Edit to change an existing access permission.
Select Delete to remove an existing access permission.
Threat types
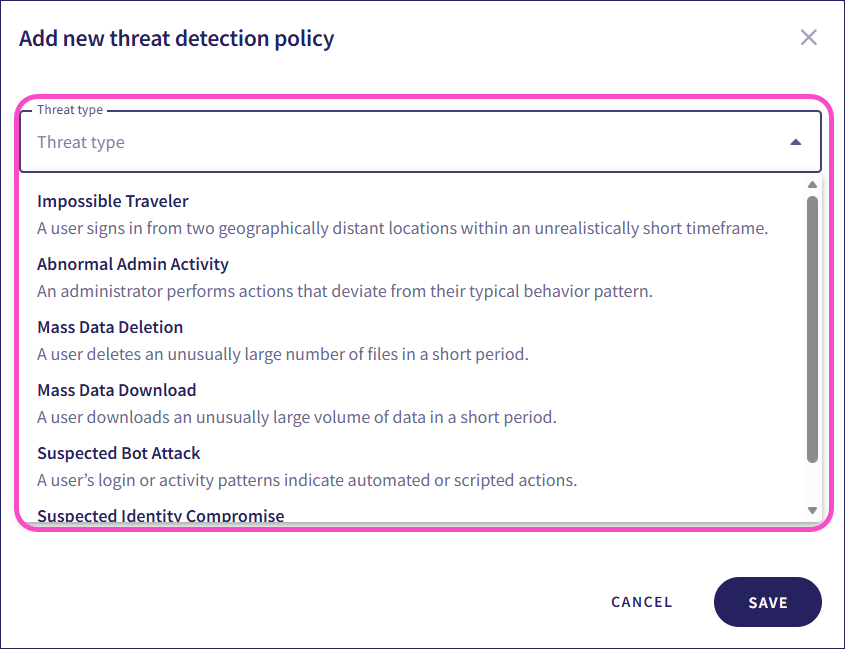
Coro supports creating detection policies for the following threat types:
- Impossible Traveler
- Abnormal Admin Activity
- Mass Data Deletion
- Mass Data Download
- Suspected Bot Attacks
- Suspected Identity Compromise
Coro creates threat detection policies by default for all protected users without automatic remediation when a new workspace is created. Admin users with sufficient permissions can edit or delete these policies as required.
Coro creates a ticket for the named threat if a user violates the policy.
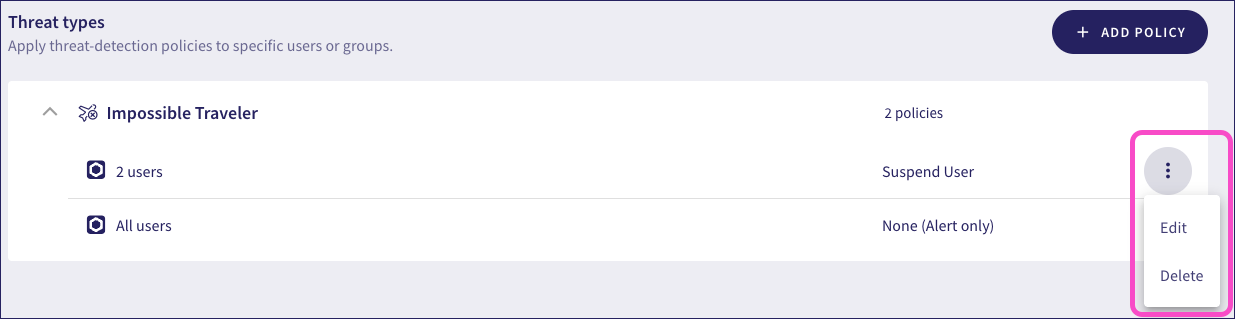
To view the currently configured threat detection policies, select the dropdown header for the policy type:
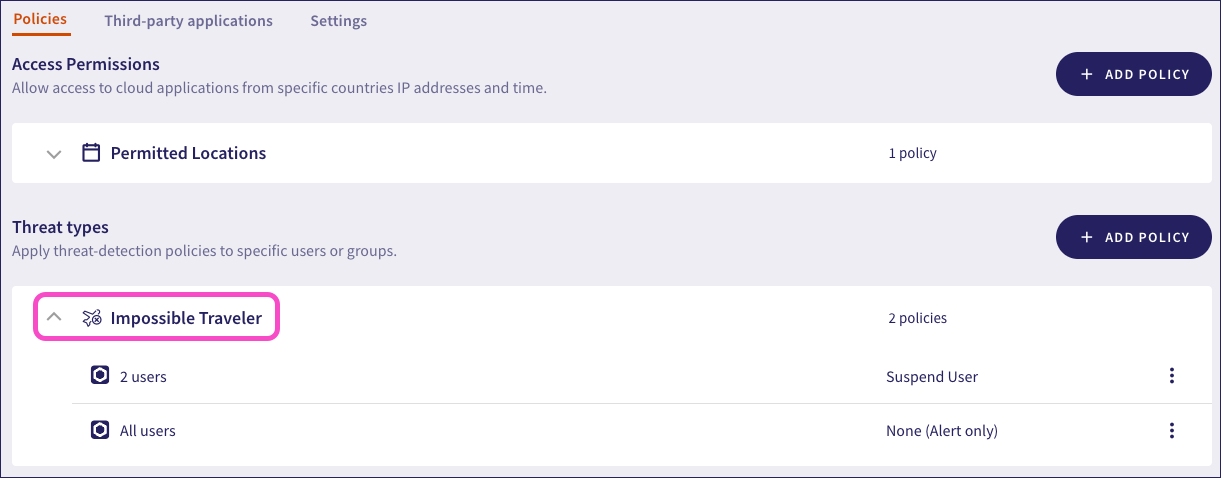
Coro displays each policy, showing:
- Users: The users or user groups that this policy affects.
- Automatic Remediation: The type of automatic remediation Coro applies if a user violates the policy.
Configuring new threat detection policies
To configure a new threat detection policy:
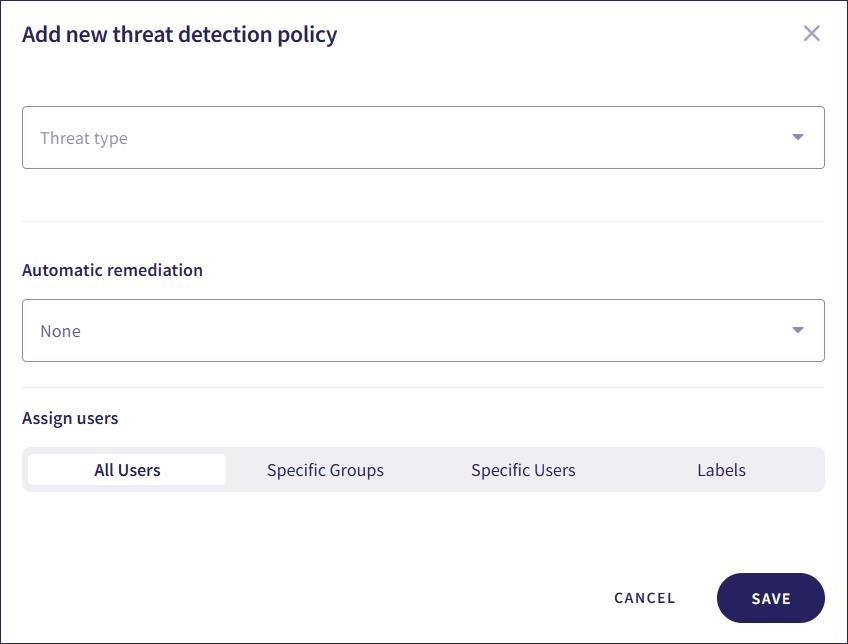
In Threat types, select + ADD POLICY:
Coro displays the Add new threat detection policy dialog:
Select a threat type for the policy:
Set the type of automatic remediation Coro should apply when a user violates the policy:

None: No remediation steps are required.
Suspend: The user account is automatically suspended.
Sign out: The user is signed out..
In all cases, Coro creates a ticket to alert admin users to the event.
Select the users or groups to assign to this policy:

All Users: The policy applies to all protected users.
Specific Groups: The policy applies to named user groups.
Specific Users: The policy applies to named users, specified by their email addresses.
Labels: The policy applies to users included in the user label. For more information on user labels, see User labels.
Select SAVE to save your changes.
Editing and deleting existing threat detection policies
Admin users with sufficient permissions can edit and delete existing threat detection policies.
To edit or delete existing policies, select the corresponding action from the three-dot menu:
Select Edit to change the settings in an existing policy.
Select Delete to remove an existing policy.
Connectivity warnings
If any previously connected cloud applications have connectivity issues, Coro displays a warning banner at the top of the page:

Select Review to see the list of issues, each with a brief description and a link to the console page where you can resolve it.
Detection is disabled for cloud applications in the following connectivity states:
Connected (Additional setup required): For example, Microsoft 365 is connected, but some required permissions may be missing, or audit log recording is disabled.
Incomplete: For example, Microsoft 365 setup was started, but a step in the connection dialog was skipped.
Disconnected: For example, Microsoft 365 permissions were removed after the application was connected.
Coro still allows you to configure policies for these applications, but they only take effect after any issues are resolved.