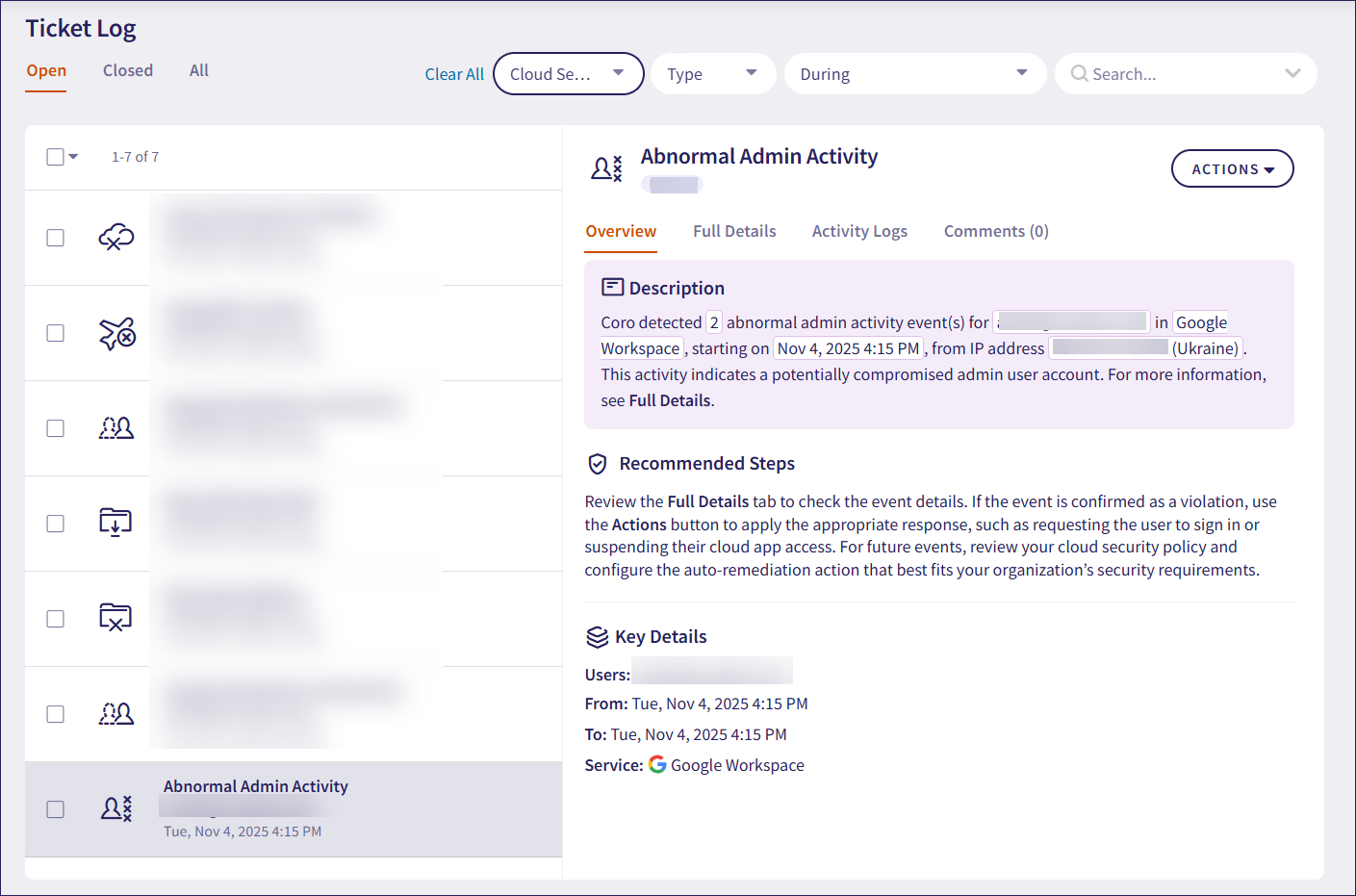
Abnormal Admin Activity
Abnormal Admin Activity tickets report instances of potential account breaches or unusual behavior patterns for your admin users.
Coro detects potential identity compromise for admin user accounts by analyzing data from all customers, specific customers, and specific users behind a ticket. Coro then creates normative behavior models from which anomalies can be detected. These models range from simple statistical anomaly models to more complex models that cross-correlate data from various sensors throughout the system, uncovering evidence of abnormal behavior.
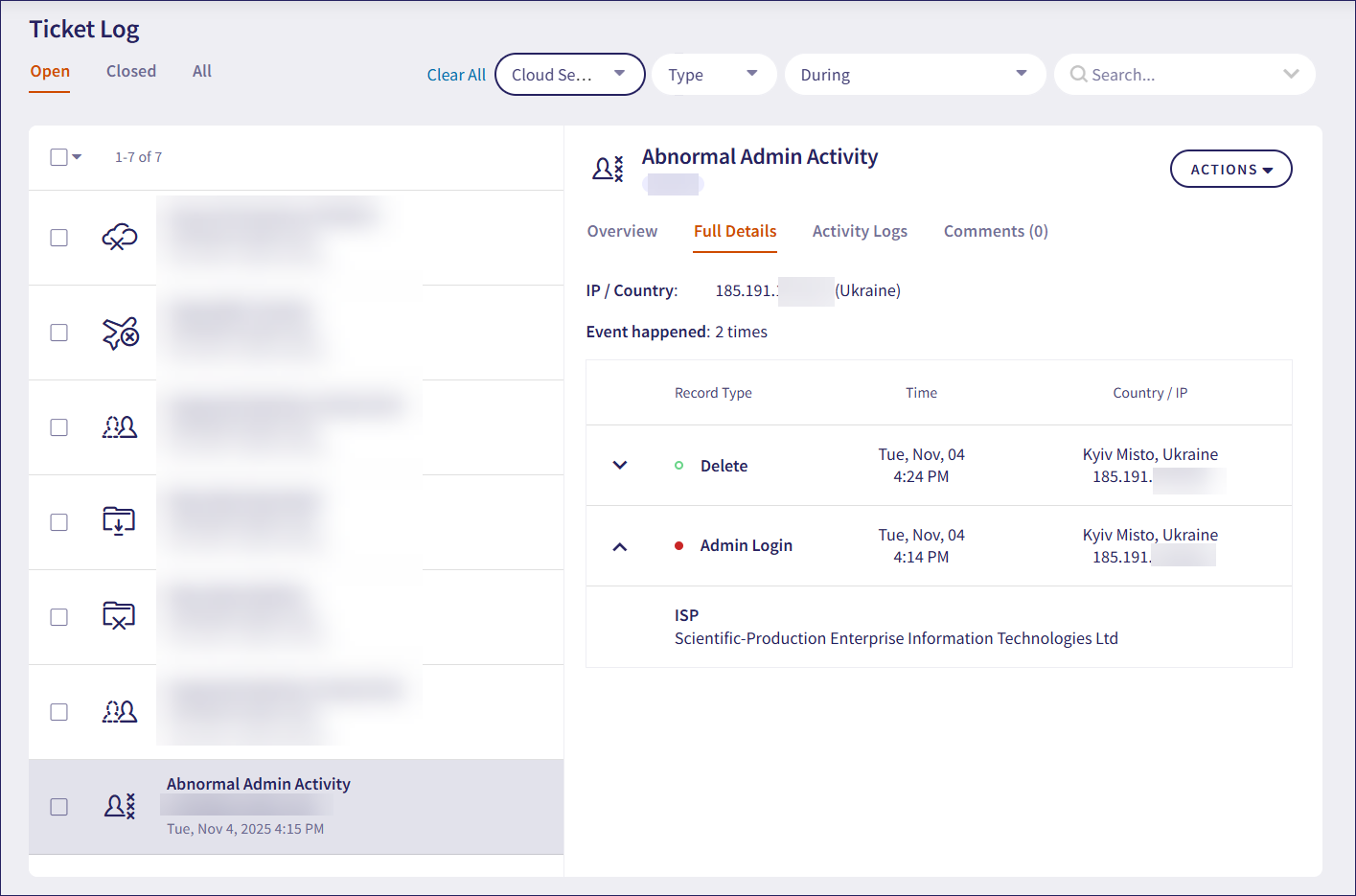
The Full Details section for Abnormal Admin Activity tickets is similar to that of Suspected Identity Compromise tickets. Coro displays a log of admin activity, listing the time and location for each event. Suspected activities are indicated in red, while typical activities are in green.
Coro uses IP lookup providers to derive metadata about connecting IP addresses to help admin users identify patterns in suspicious activity. Select the dropdown next to an activity to view any identified details, such as service provider, proxy, organization name, or threat type (where one is identified).
In the following example, Admin Login activities are marked as suspicious because they each occurred from a different IP address within a short time span. Use the dropdown next to each activity to view metadata related to the IP address, such as the service provider (ISP):
Abnormal Admin Activity tickets are classified as open for review and are automatically closed after a review period of four weeks.