Adding a new SIEM connector
Coro integrates with Security Information and Event Management (SIEM) platforms and provides real-time access to ticket data, enabling integration with existing workflows.
Coro currently supports the following integrations:
Fluency
Fluency (https://fluencysecurity.com) is a streaming analytics SIEM platform that delivers risk-prioritized insights from across your environment. Integrate Fluency with Coro to collect ticket data related to an event.
Configuring a Fluency connector via the Coro console
To configure a Fluency connector:
- Sign in to the Coro console .
-
From the sidebar, select
 to access the
Control Panel
.
to access the
Control Panel
.
-
Under
Workspace
, select
Connectors
:
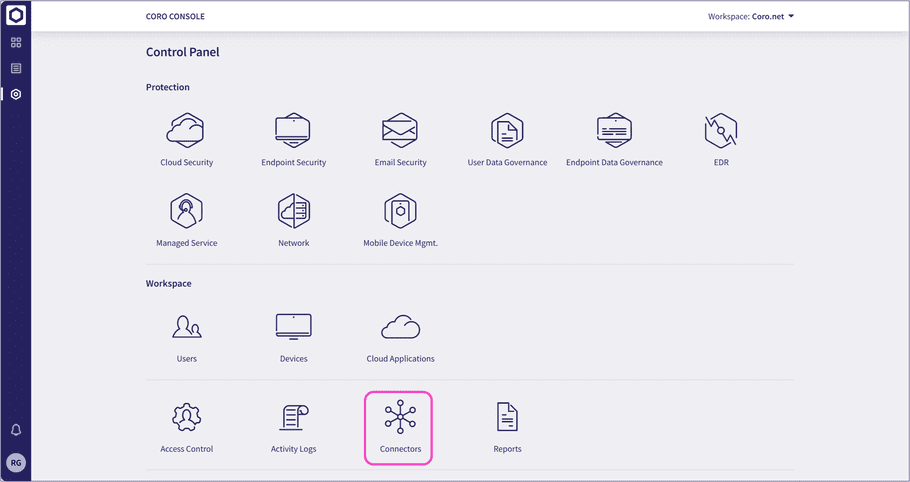
Coro displays the Connectors page:
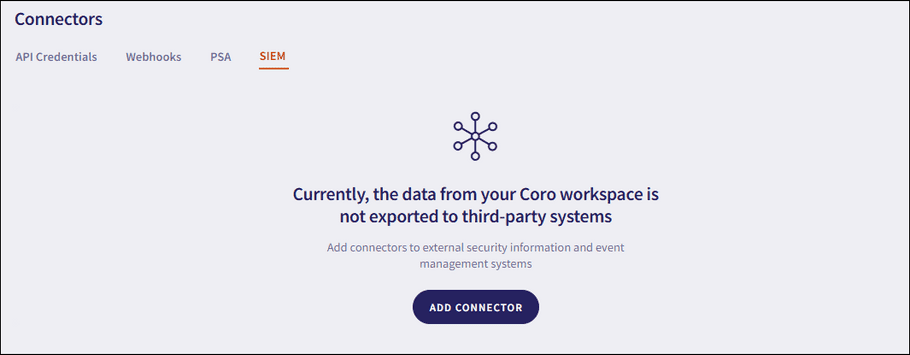
- Select SIEM .
-
Select
ADD CONNECTOR
.
Coro displays the Add connector dialog:
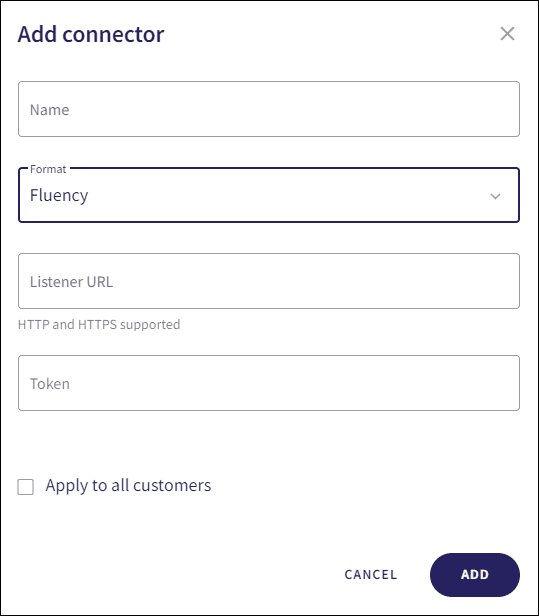
- Enter a connector Name .
- From the Format dropdown, select Fluency .
- Enter the Listener URL and Token (both retrieved from your SIEM provider).
-
(Optional) Enable
Apply to all customers
to create the new connector for all child workspaces connected to the parent (channel) workspace. Events from each child workspace are then sent to the configured SIEM provider:
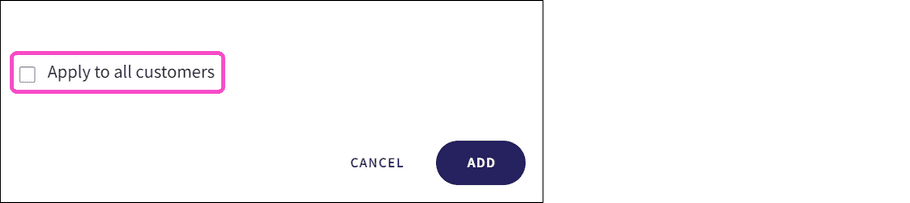
note
This option applies only to Managed Service Provider (MSP) parent (channel) workspaces.
For further information, see Managing Workspaces.
-
Select
ADD
:

Coro triggers a test event to verify the configuration. If the settings are incorrect, Coro displays an error dialog. Select GOT IT to return to the Connectors page. The configuration is not saved:
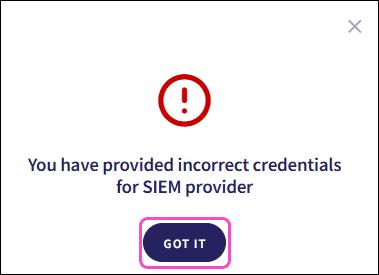
After successful configuration, Coro displays the new connection with a Connected status:

Coro adds the connector to the workspace.
note
For MSP parent (channel) workspaces, Coro adds the connector to the parent (channel) workspace and, if Apply to all customers is enabled, to all connected child workspaces.
Configuration is complete.
If the SIEM endpoint device is unavailable after the configuration, Coro retries the connection after two hours. If the device remains unavailable, Coro displays a message in the Messages section of the Actionboard:
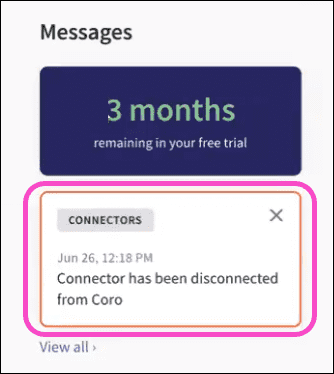
If the SIEM service is not connected, Coro displays Disconnected:

Use the Sync action to manually retry a failed connection.
Coro sends all events to the configured SIEM in real time. It returns all data and metadata associated with each event. Coro does not collect events when the SIEM service is disconnected. This typically happens when the downstream SIEM server is unavailable.
note
The event data returned might differ depending on the SIEM provider used for the connector.
The following example shows the data returned for a Domain Impersonation ticket:
{
"id": "OLvX-1479",
"workspaceId": "coronmicrosofteom_OLvX_b",
"ticketType": "emailPhishing",
"ticketDetails": {
"affectedUser": "user1.test@myyahoo.com",
"service": "office365Enforcement",
"locations": [],
"emailMetadata": {
"subject": "test",
"senderEmail": "user1.test@myyahoo.com",
"senderIp": "192.0.2.0",
"recipients": [
"testuser1@coro.onmicrosoft.com"
],
"processedMessages": [
{
"messageId": "AAkALgAAAAAAHYQD6EapmEc2byAcQAC-Elv8AklmbFzgKuZeaN9sWir-hpwwAB8FbapwAA"
}
]
},
"filesMetadata": [],
"firstEventTime": 1713774078429,
"lastEventTime": 1713774078429,
"creationTime": 1713774078447,
"processed": true,
"processedTime": 1713774078429,
"ticketTrigger": "domainImpersonation"
}
}note
For information on connector actions, see SIEM connector actions.
Generic webhook integration
Coro supports generic webhook integrations to collect ticket data related to an event and send it from the Coro console to a specified URL endpoint, such as the REST API of an internal IT system.
To configure a generic webhook connector:
- Enter a connector Name .
- From the Format dropdown, select Generic .
- Enter the external webhook into Listener URL (retrieved from your organization’s internal IT system).
-
(Optional) Enable
Apply to all customers
to create the new connector for all child workspaces connected to the parent (channel) workspace. Events from each child workspace are then sent to the specified webhook endpoint:

note
This option applies only to Managed Service Provider (MSP) parent (channel) workspaces.
For further information, see Managing Workspaces.
-
(Optional) To configure request headers, such as for authentication or custom metadata, select
+ Header
:

note
Headers allow your webhook to send additional information, such as an authorization token, along with the request.
To protect sensitive information, Coro encrypts all headers before storing them.
-
Select
Add
:
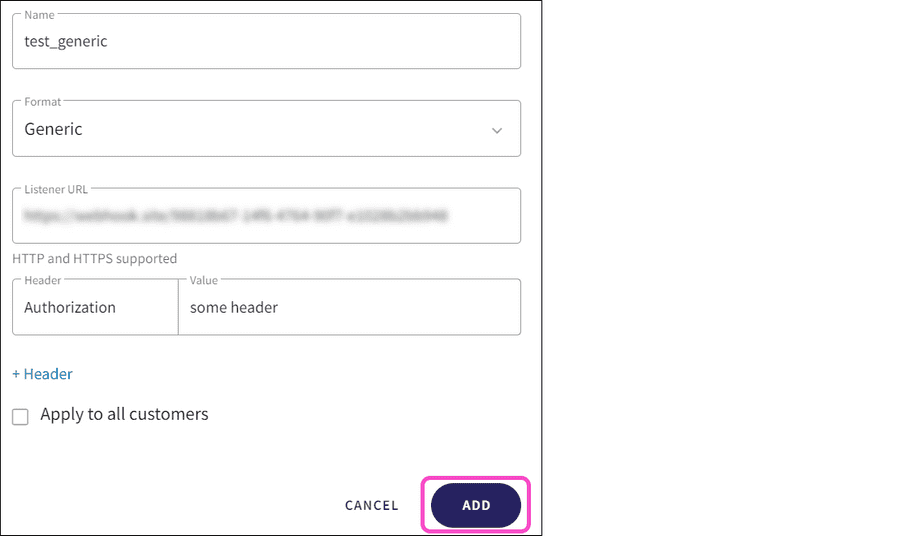
Coro triggers a test event to verify the configuration. If the settings are incorrect, Coro displays an error dialog. Select GOT IT to return to the Connectors page. The configuration is not saved:

After successful configuration, Coro displays the new connection with a Connected status:

Coro adds the connector to the workspace.
note
For MSP parent (channel) workspaces, Coro adds the connector to the parent (channel) workspace and, if Apply to all customers is enabled, to all connected child workspaces.
Configuration is complete.
Coro sends all events to the configured webhook endpoint in real time. It returns all data and metadata associated with each event.
To learn about SIEM connector actions, see SIEM connector actions.
Microsoft Sentinel
Microsoft Sentinel (https://www.microsoft.com/en-us/security/business/siem-and-xdr/microsoft-sentinel) provides real-time threat detection and response, integrating with Microsoft tools. Its cloud-native architecture offers scalability, while AI-driven automation supports incident analysis. Integrate Microsoft Sentinel with Coro to collect ticket data related to an event.
note
Coro sends SIEM data to Azure Monitor using the HTTP Data Collector API, which is then imported into Microsoft Sentinel.
note
To configure a Microsoft Sentinel connector, your Microsoft 365 account must have admin permissions.
Configuring a Microsoft Sentinel connector via the Coro console
To configure a Microsoft Sentinel connector:
- Sign in to the Coro console .
-
From the sidebar, select
 to access the
Control Panel
.
to access the
Control Panel
.
-
Under
Workspace
, select
Connectors
:

Coro displays the Connectors page:

-
Select
ADD CONNECTOR
.
Coro displays the Add connector dialog:
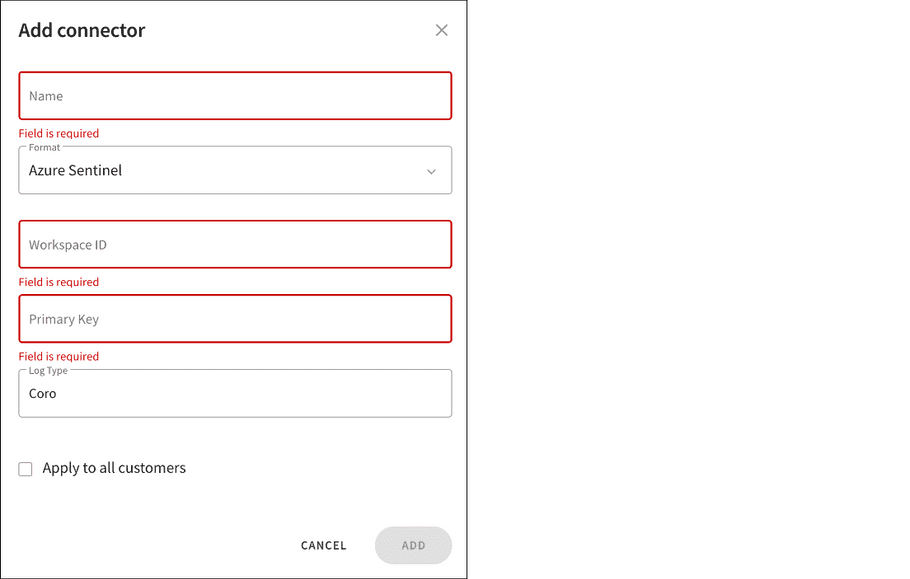
- Enter a connector Name .
- From the Format dropdown, select Azure Sentinel .
- Enter a valid Microsoft Workspace ID .
- Enter a valid Primary Key (API key).
- Specify Log Type to define where Microsoft Sentinel stores the logs. The default value is Coro , but you can modify it as needed.
-
(Optional) Enable
Apply to all customers
to create the new connector for all child workspaces connected to the parent (channel) workspace. Events from each child workspace are then sent to the configured SIEM provider:

note
This option applies only to Managed Service Provider (MSP) parent (channel) workspaces.
For further information, see Managing Workspaces.
-
Select
ADD
.

Coro triggers a test event to verify the configuration. If the settings are incorrect, Coro displays an error dialog. Select GOT IT to return to the Connectors page. The configuration is not saved:

After successful configuration, Coro displays the new connection with a Connected status:

Coro adds the connector to the workspace.
note
For MSP parent (channel) workspaces, Coro adds the connector to the parent (channel) workspace and, if Apply to all customers is enabled, to all connected child workspaces.
Configuration is complete.
If the SIEM endpoint device is unavailable after the configuration, Coro retries the connection after two hours. If the device remains unavailable, Coro displays a message in the Messages section of the Actionboard:

If the SIEM service is not connected, Coro displays Disconnected:

Use the Sync action to manually retry a failed connection.
Coro sends all events to the configured SIEM in real time. It returns all data and metadata associated with each event. Coro does not collect events when the SIEM service is disconnected. This typically happens when the downstream SIEM server is unavailable.
note
The event data returned might differ depending on the SIEM provider used for the connector.
The following example shows the data returned for a Domain Impersonation ticket:
{
"id": "OLvX-1479",
"workspaceId": "coronmicrosofteom_OLvX_b",
"ticketType": "emailPhishing",
"ticketDetails": {
"affectedUser": "user1.test@myyahoo.com",
"service": "office365Enforcement",
"locations": [],
"emailMetadata": {
"subject": "test",
"senderEmail": "user1.test@myyahoo.com",
"senderIp": "192.0.2.0",
"recipients": [
"testuser1@coro.onmicrosoft.com"
],
"processedMessages": [
{
"messageId": "AAkALgAAAAAAHYQD6EapmEc2byAcQAC-Elv8AklmbFzgKuZeaN9sWir-hpwwAB8FbapwAA"
}
]
},
"filesMetadata": [],
"firstEventTime": 1713774078429,
"lastEventTime": 1713774078429,
"creationTime": 1713774078447,
"processed": true,
"processedTime": 1713774078429,
"ticketTrigger": "domainImpersonation"
}
}note
For information on connector actions, see SIEM connector actions.
Splunk
Splunk (https://www.splunk.com/en_us/products/enterprise-security.html) is a platform for collecting, analyzing, and visualizing machine-generated data. Organizations use it for log management, SIEM, and operational monitoring. Integrate Splunk with Coro to collect ticket data related to an event.
note
Coro sends SIEM data to Splunk via HTTP event collector (HEC) REST API endpoints.
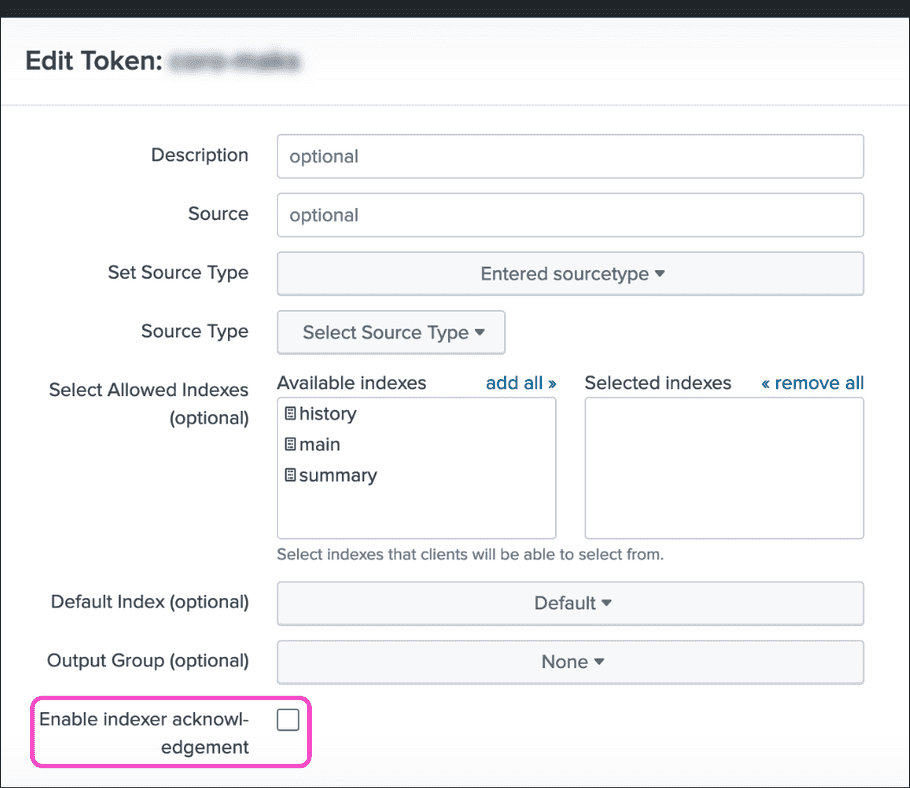
Important
Disable Enable indexer acknowledgment when configuring an HEC on the Splunk Cloud Platform:
Configuring a Splunk connector via the Coro console
To configure a Splunk connector:
- Sign in to the Coro console .
-
From the sidebar, select
 to access the
Control Panel
.
to access the
Control Panel
.
-
Under
Workspace
, select
Connectors
:

Coro displays the Connectors page:

-
Select
ADD CONNECTOR
.
Coro displays the Add connector dialog:
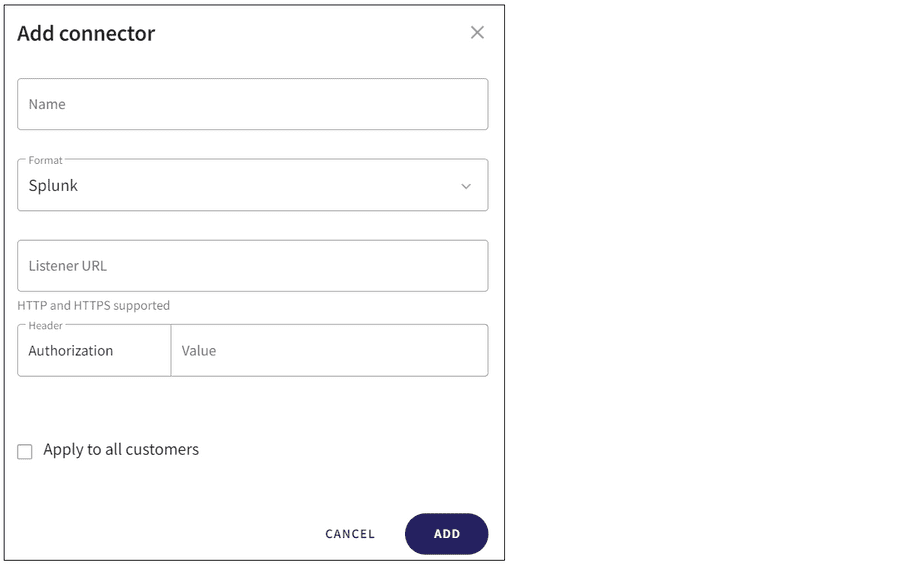
- Enter a connector Name .
- From the Format dropdown, select Splunk .
-
Enter the
Listener URL
(retrieved from your SIEM provider).
Important
-
The
Listener URL
must be in the format:
http(s)://Public IP Address of Splunk/services/collector
.
Example value:
https://192.0.2.0:8088/services/collector -
The
Listener URL
must match the SSL configuration (
Enable SSL
option) in your Splunk cloud platform HEC settings:
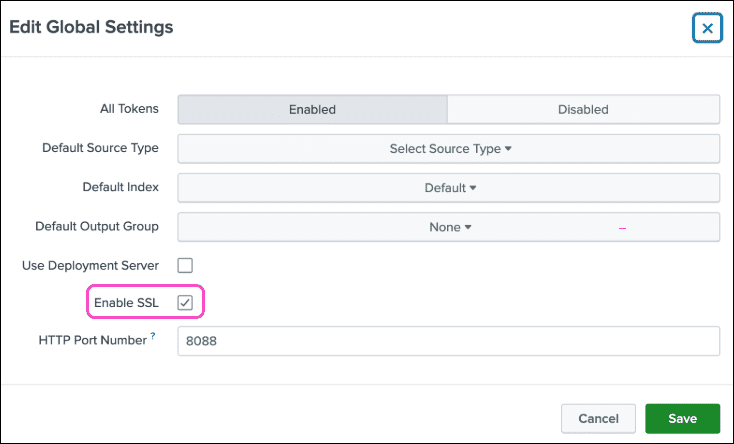
- If Enable SSL is enabled, use https://
- If Enable SSL is disabled, use http://
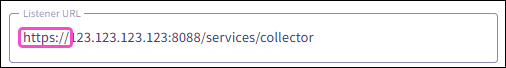
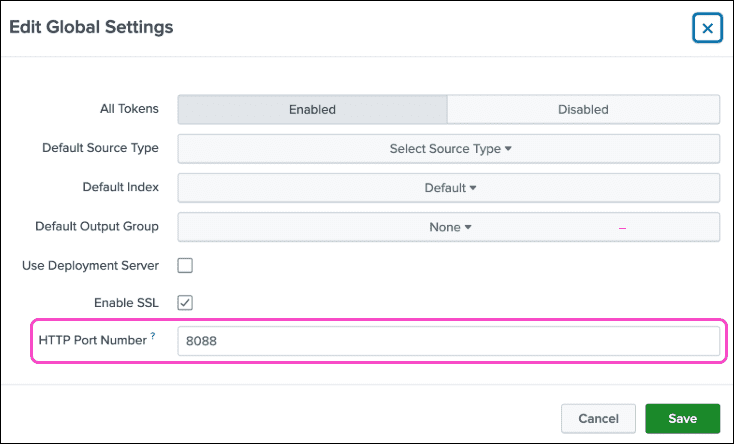
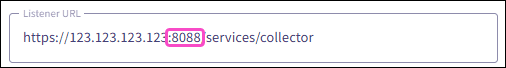
-
The port number part of the
Listener URL
must match the
HTTP Port Number
value in your Splunk cloud platform HEC settings:
-
The
Listener URL
must be in the format:
http(s)://Public IP Address of Splunk/services/collector
.
-
Enter the
Authorization
header (retrieved from your SIEM provider).
Important
The Authorization header must be in the format: Splunkf <Authorization_token>.
Example value:
Splunkf 9b30ab7-85bf-4dd5-8fd9-b42bb3a74163.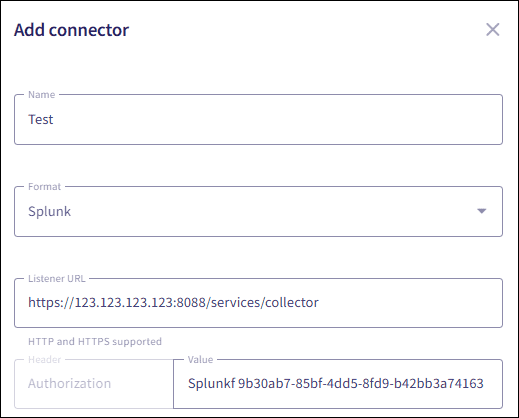
-
(Optional) Enable
Apply to all customers
to create the new connector for all child workspaces connected to the parent (channel) workspace. Events from each child workspace are then sent to the configured SIEM provider:

note
This option applies only to Managed Service Provider (MSP) parent (channel) workspaces.
For further information, see Managing Workspaces.
-
Select
ADD
.

Coro triggers a test event to verify the configuration. If the settings are incorrect, Coro displays an error dialog. Select GOT IT to return to the Connectors page. The configuration is not saved:

After successful configuration, Coro displays the new connection with a Connected status:

Coro adds the connector to the workspace.
note
For MSP parent (channel) workspaces, Coro adds the connector to the parent (channel) workspace and, if Apply to all customers is enabled, to all connected child workspaces.
Configuration is complete.
If the SIEM endpoint device is unavailable after the configuration, Coro retries the connection after two hours. If the device remains unavailable, Coro displays a message in the Messages section of the Actionboard:

If the SIEM service is not connected, Coro displays Disconnected:

Use the Sync action to manually retry a failed connection.
Coro sends all events to the configured SIEM in real time. It returns all data and metadata associated with each event. Coro does not collect events when the SIEM service is disconnected. This typically happens when the downstream SIEM server is unavailable.
note
The event data returned might differ depending on the SIEM provider used for the connector.
The following example shows the data returned for a Domain Impersonation ticket:
{
"id": "OLvX-1479",
"workspaceId": "coronmicrosofteom_OLvX_b",
"ticketType": "emailPhishing",
"ticketDetails": {
"affectedUser": "user1.test@myyahoo.com",
"service": "office365Enforcement",
"locations": [],
"emailMetadata": {
"subject": "test",
"senderEmail": "user1.test@myyahoo.com",
"senderIp": "192.0.2.0",
"recipients": [
"testuser1@coro.onmicrosoft.com"
],
"processedMessages": [
{
"messageId": "AAkALgAAAAAAHYQD6EapmEc2byAcQAC-Elv8AklmbFzgKuZeaN9sWir-hpwwAB8FbapwAA"
}
]
},
"filesMetadata": [],
"firstEventTime": 1713774078429,
"lastEventTime": 1713774078429,
"creationTime": 1713774078447,
"processed": true,
"processedTime": 1713774078429,
"ticketTrigger": "domainImpersonation"
}
}