Introducing the Inbound Gateway
This article describes Coro's Inbound Gateway email security add-on and how it can help protect your users' incoming email.
For information on Coro's Outbound Gateway, see Configuring an outbound gateway for email scanning.
Overview
A subscription to Coro's Email Security module enables organizations to configure comprehensive and configurable anti-malware and anti-phishing protection for the email accounts of protected users in connected Gmail or Microsoft 365 cloud applications. Coro utilizes an API-based approach to check emails in a user's mailbox, deleting or quarantining malicious messages as appropriate. For more details, see Email Security.
Coro's Inbound Gateway add-on takes this same protection one step further by offering a full email proxy gateway that intercepts inbound emails before they enter the organization's network.
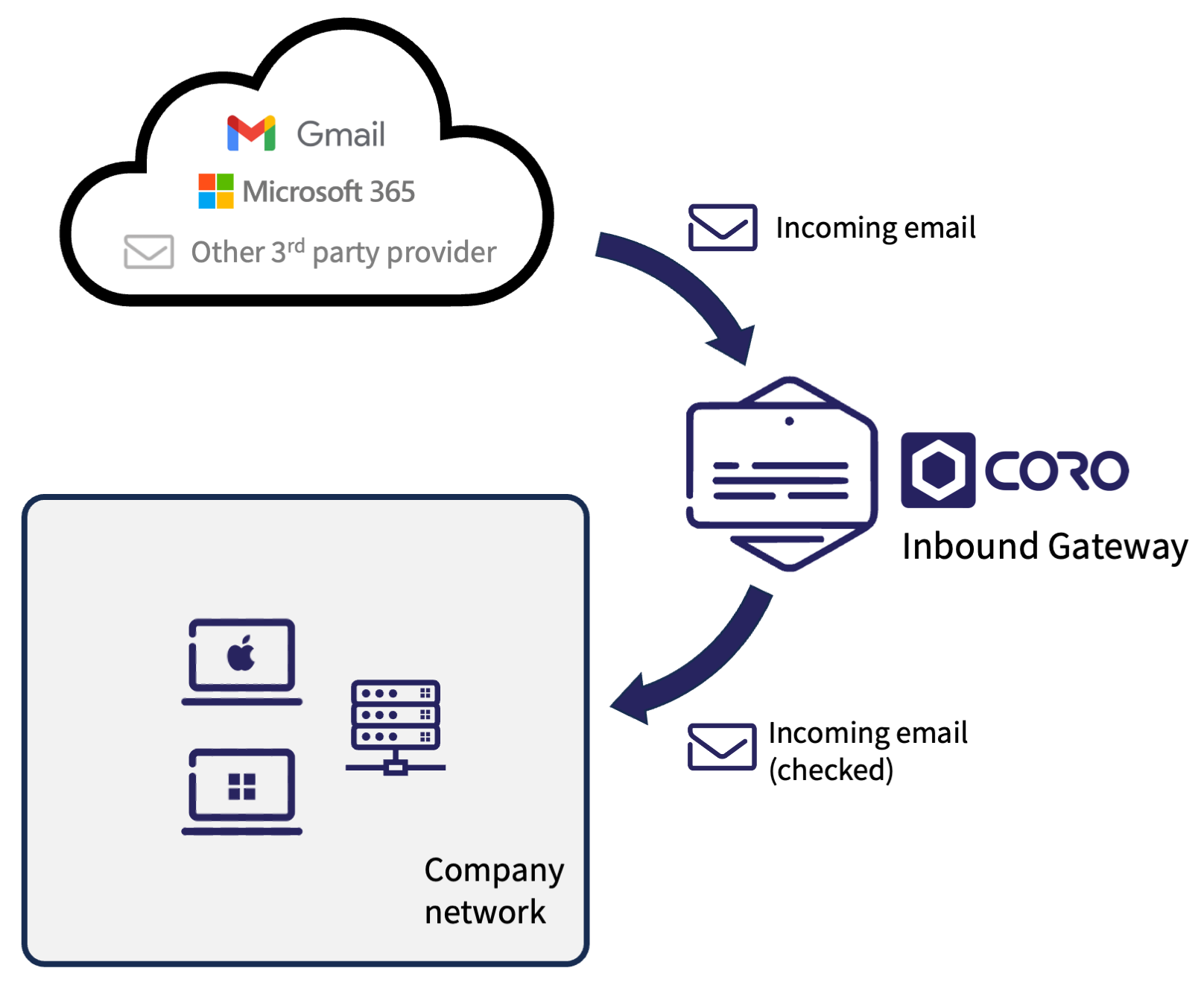
Emails passing through the Inbound Gateway are thoroughly inspected for threats, greatly reducing the number of malicious or untrusted emails that enter the organization and reach their intended recipients.
While Coro's API-based Email Security module is designed to protect users in connected cloud email services from Google or Microsoft, the Inbound Gateway acts on email messages from all third party providers. Messages are checked at delivery (MX/DNS level protection) and recipients can be individual accounts, groups, or shared email boxes.
API-based email security subscription: Detects threats by scanning email after delivery.
Inbound Gateway: Intercepts and processes incoming email before it is delivered.
Using the Inbound Gateway
The Inbound Gateway is an add-on to Coro's Email Security module. You can use the Inbound Gateway as a standalone email protection service without configuring API connections to your cloud applications, but combining both approaches provides increased protection against email threats. Both services are configured through the same common settings - enabling scanning for one threat type affects both API-based protection and the Inbound Gateway simultaneously.
By incorporating the Inbound Gateway into your existing API-based email protection, you increase the probability that a threat will be detected. You additionally introduce a failover mechanism in the unlikely event that one of the protection mechanisms is blocked or prevented from full operation.
To enable the Inbound Gateway to inspect and protect your users' incoming email, you must make sure they are added to protection. If you have no cloud applications connected, this must be done manually (by adding user email addresses individually or through a CSV file-based bulk import). Alternatively, connect a cloud application to your workspace to enable Coro to identify and add all registered email users in one operation.
The following restrictions apply to the Inbound Gateway:
Emails to group addresses: Due to the way the Inbound Gateway intercepts emails before they reach an organization, emails sent to a distribution group email address appear to the Inbound Gateway as a message to a single recipient. The Inbound Gateway does not know about the individual members of the group.
As with individual users, where you do not have cloud applications connected, make sure you manually add group addresses to Coro as Protected Users. This ensures Coro can protect group members by performing detection and remediation against the named group address.
Emails to *.onmicrosoft.com addresses: Due to limitations in DNS configuration for Microsoft's domains, Coro cannot route emails sent to recipients with *.onmicrosoft.com addresses or aliases through the Inbound Gateway. Microsoft routes such emails directly to user's inboxes, meaning that the Inbound Gateway cannot apply protection in those cases.
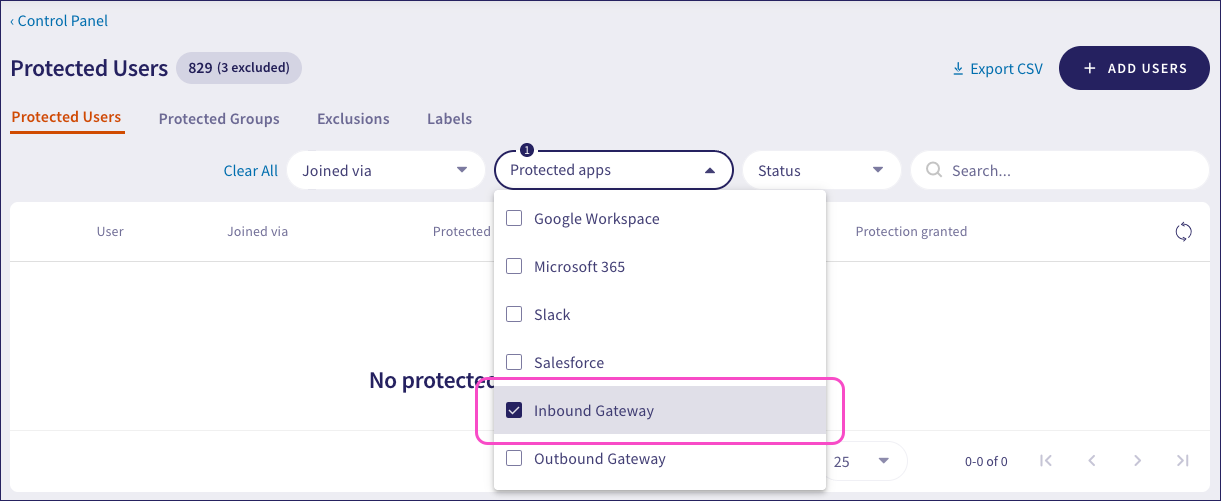
To view a list of users protected by the Inbound Gateway, use the Protected Users page. This page shows all users added to Coro for protection across all connected apps. To filter on only those users protected by the Inbound Gateway, select Inbound Gateway from the Protected apps dropdown:
Protection for unlicensed users or groups
Coro's API-based Email Security module identifies and protects only licensed user accounts in Microsoft 365 or Google Workspace. Where a distribution list, collaborative group, or shared inbox is unlicensed, or includes both licensed and unlicensed users, the Email Security module cannot protect the unlicensed users or groups.
The Inbound Gateway can protect unlicensed users and groups, but to achieve this you must add all unlicensed user or group email addresses for protection manually.
Configuring the Inbound Gateway to work with your existing email provider
The Inbound Gateway offers a streamlined workflow with seamless integration into your existing email service.
The process by which you configure the Inbound Gateway to receive email from your existing provider can be summarized as follows:
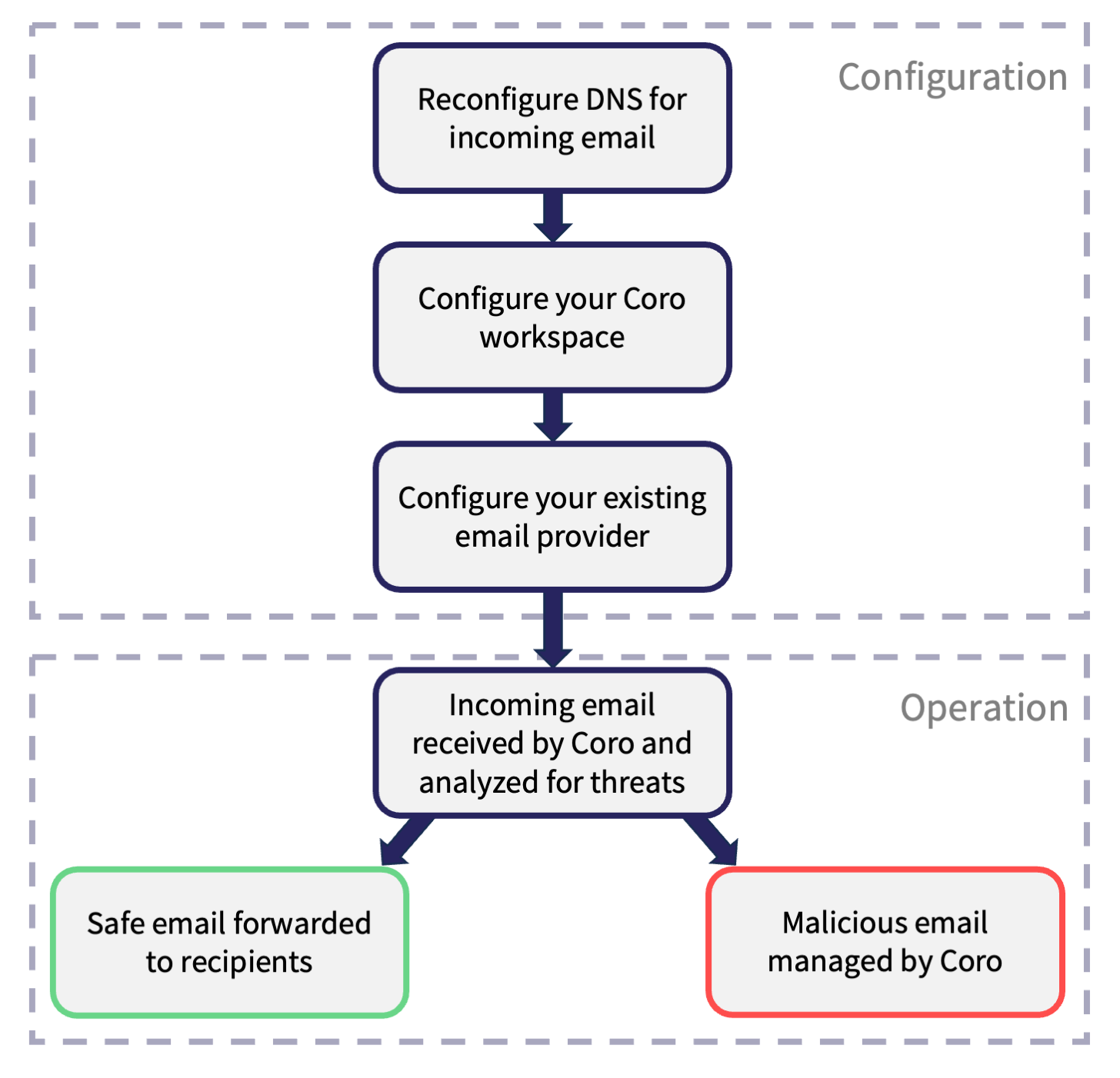
You reconfigure your DNS with Coro as the highest priority MX record, and then configure your Coro workspace with details of the email domain being protected. Finally, you configure your existing email service to set Coro as the gateway for inbound email.
In normal operation, incoming email is received by the Coro Inbound Gateway and analyzed for potential threats.
Safe emails are transparently forwarded to the recipient, and malicious emails are managed by Coro according to your selected level of protection (see How Coro handles malicious email). Coro raises tickets in the console for each potentially malicious email it encounters. This enables admin users to analyze threats and take appropriate action to safely remove malicious content, or identify false positives and release the email to its recipient.
To learn more about configuring the Coro Inbound Gateway, see Configuring the gateway.