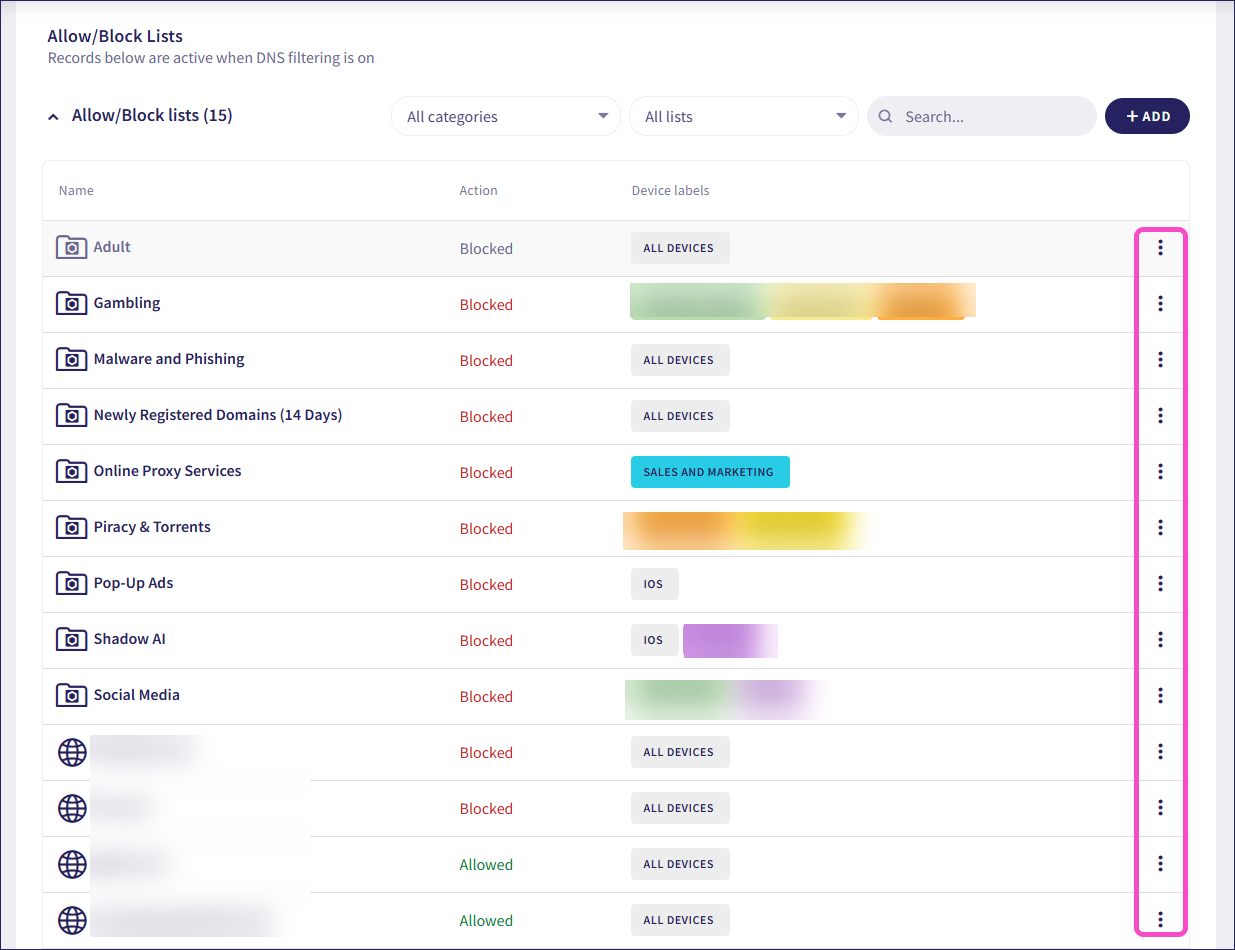
Admin users can enable or disable DNS filtering, which includes basic malware filtering when enabled. DNS filtering allows admin users to restrict or allow access to specific domains, as well as groups or categories of domains. For example, an admin user may block access to suspected malware sites, or enforce company policy by blocking access to gambling sites or social networks. By default, DNS filtering is disabled.
Admin users can make changes to the DNS filtering section whether filtering is enabled or disabled. If you make changes while DNS filtering is disabled, Coro applies those changes after you enable filtering.
To apply DNS filtering, make sure the Network service in the Coro Agent or Endpoint Protection app is connected on each device. For more information, see The Network service in the Coro Agent or The Coro Endpoint Protection app.
To apply DNS filtering to protected devices, you must both enable DNS filtering and assign device labels to allowlists or blocklists. Filtering only applies to devices that are part of the specified device labels; it does not apply to all devices in the workspace.
To enable DNS filtering:
From the sidebar, select Control Panel:
Select SWG:
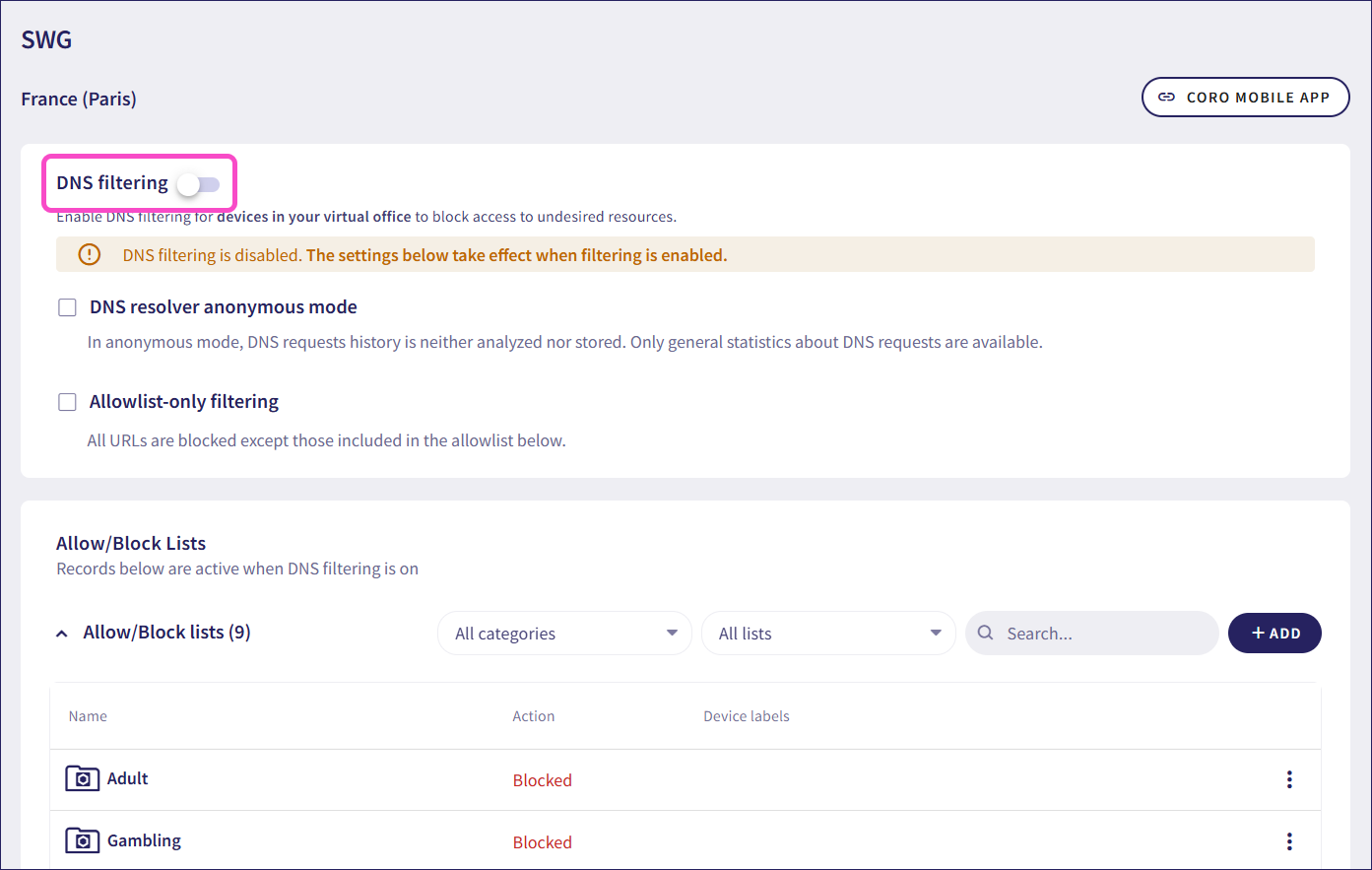
Coro displays the SWG page:
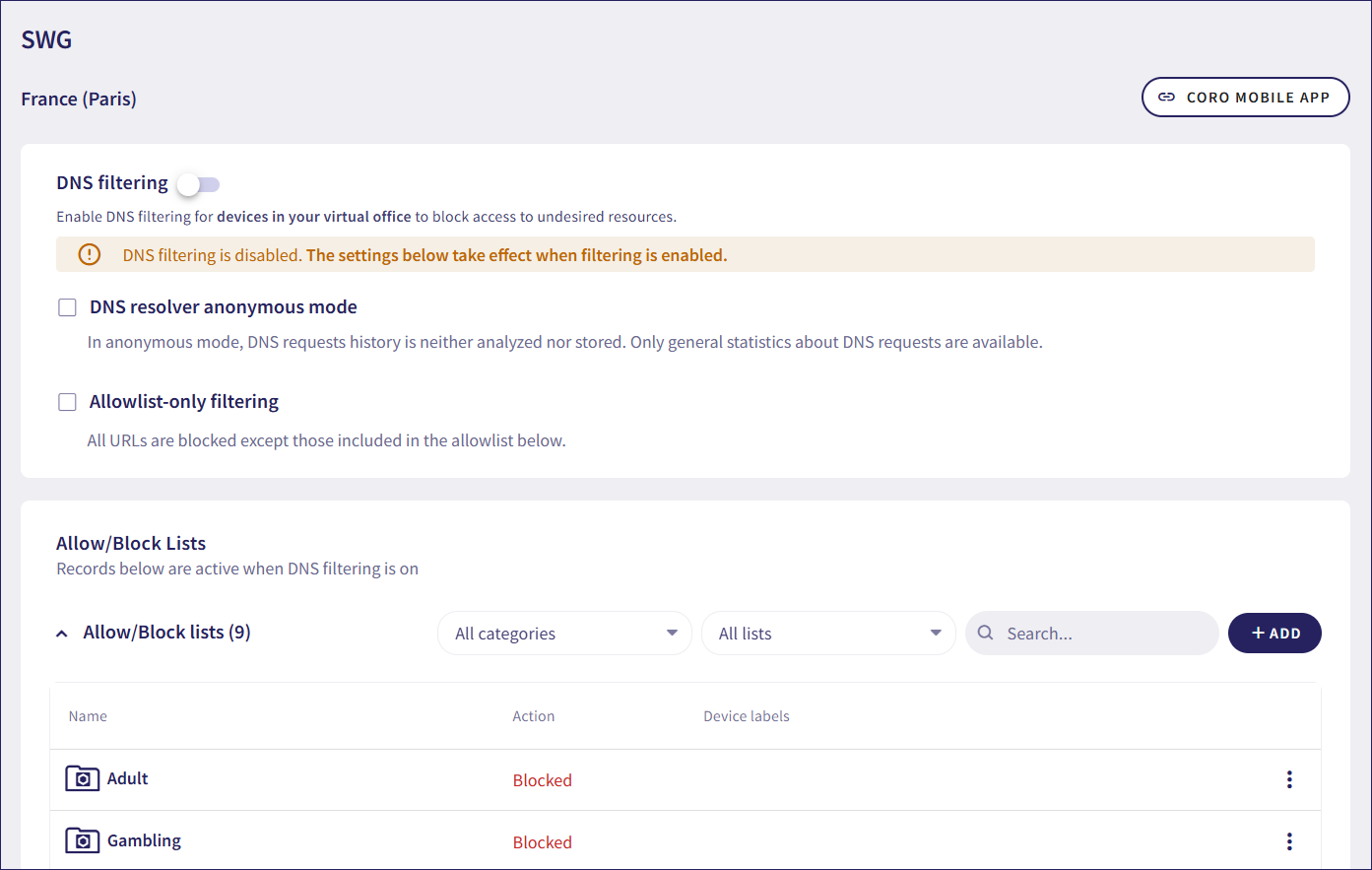
Add device labels to allowlists or blocklists with device labels to which DNS filtering should apply. For more information, see Allowlists and blocklists.
Enable DNS filtering:
Coro displays a confirmation dialog:
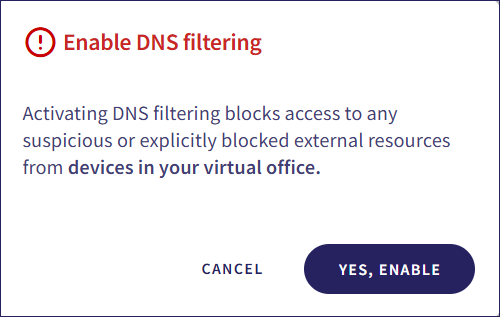
Select YES, ENABLE.
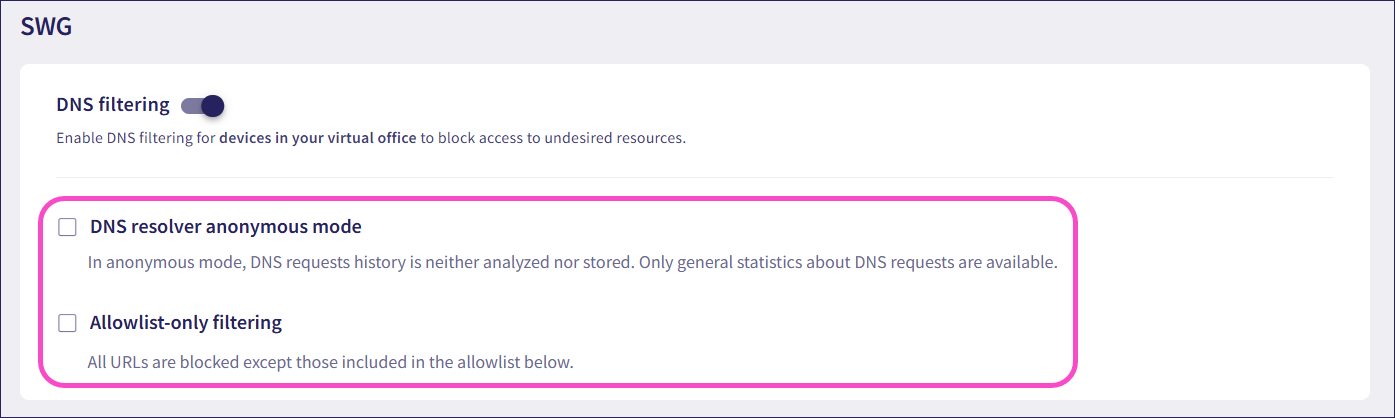
Admin users can enable:
- DNS resolver anonymous mode: Protects user privacy by not tracking individual data. This option ensures that Coro does not analyze or store the DNS request history.
- Allowlist-only filtering: Blocks all URLs except those added to the allowlist.
Coro displays allowlists and blocklists below the DNS filtering section. The Allow/Block Lists section includes a predefined set of inactive external blocklists (locked URL groups). Admin users can view, enable, and add device labels to these lists.
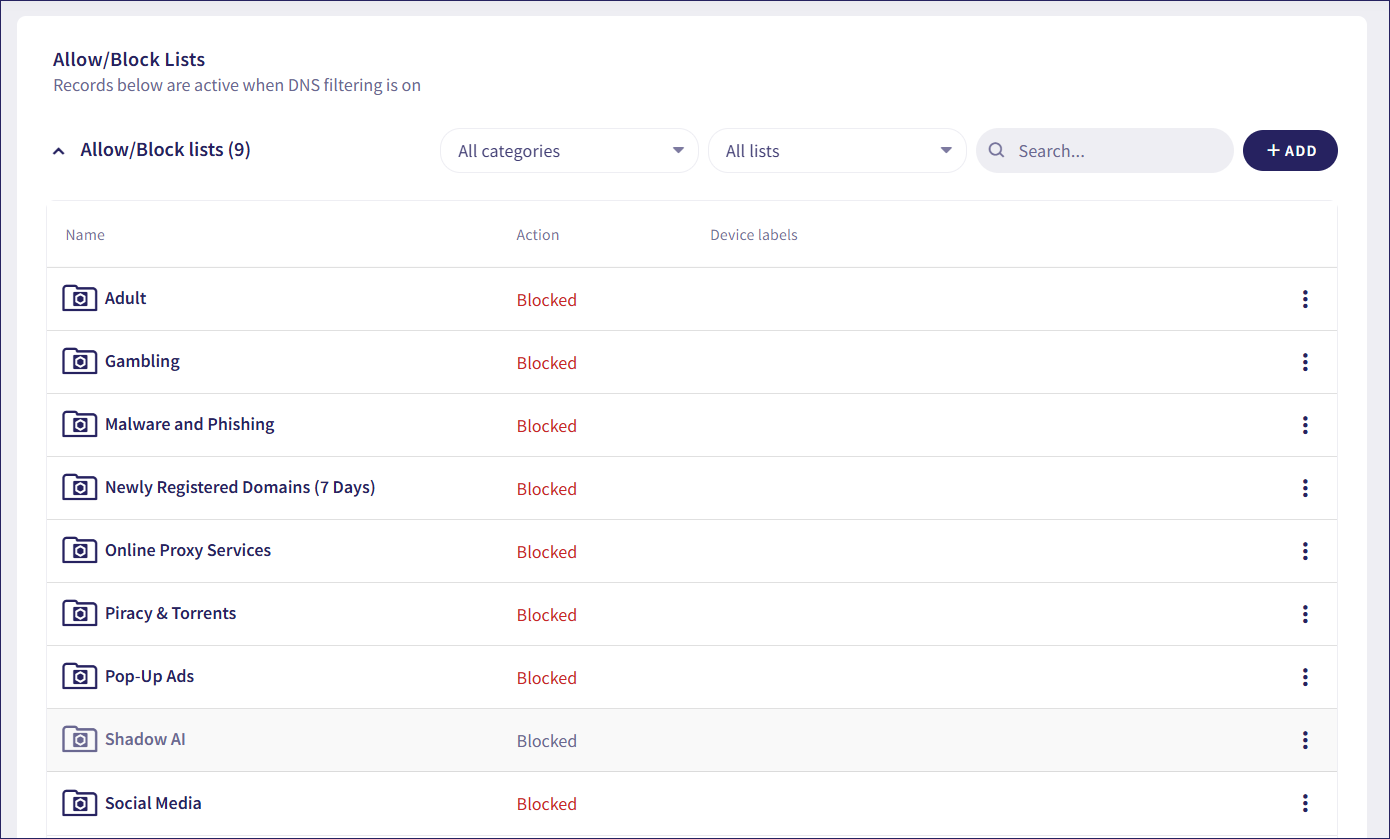
Allowlists and blocklists are only enforced when DNS filtering is enabled. However, admin users can manage these lists whether filtering is currently enabled or disabled. Changes made while filtering is disabled take effect after it is enabled.
To add device labels to locked URL groups:
From the three-dot menu of the relevant URL group, select Edit URL group:
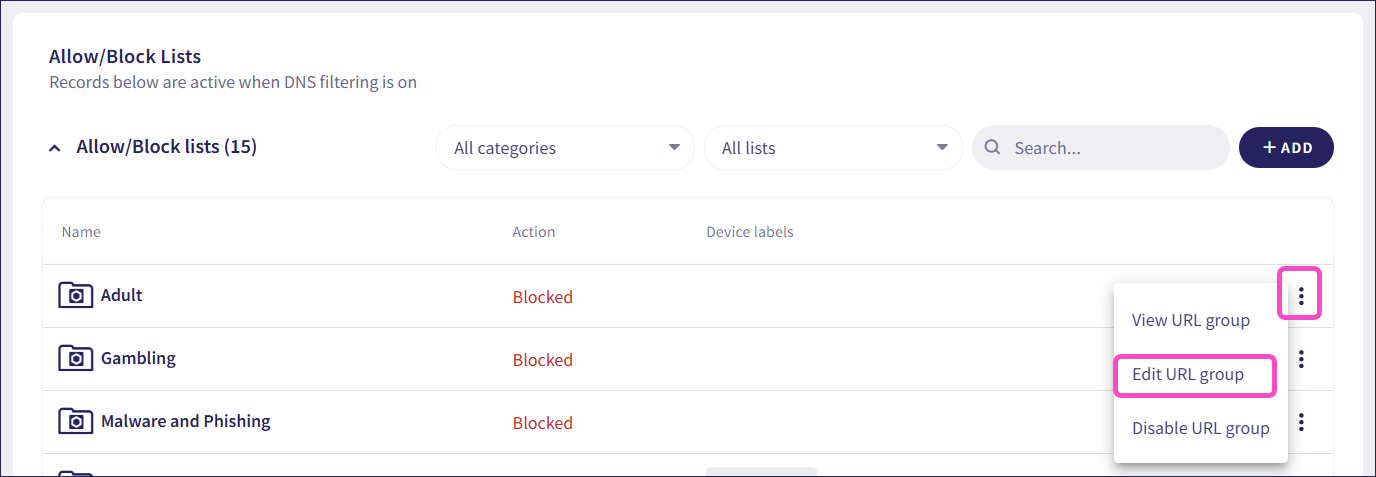
Coro displays the Edit URL group dialog:

Select device labels to which the allowlist or blocklist should apply.
Select APPLY.
If disabled, from the three-dot menu, select Enable URL group:
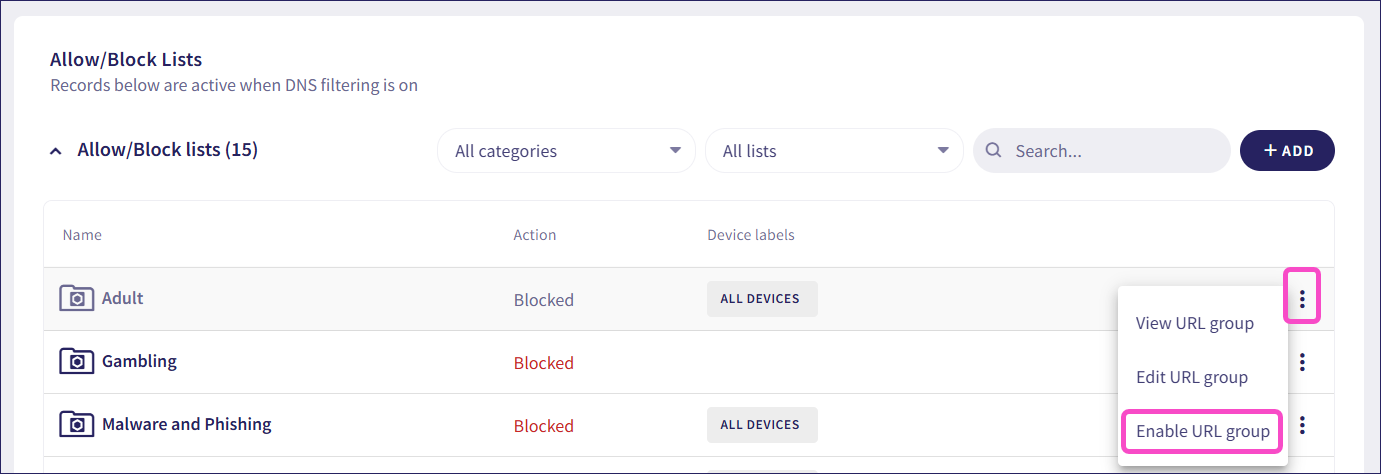
To add URLs, IP address ranges, subnets, or URL-based wildcards to an allowlist or blocklist:
Select + ADD > Add to allowlist/blocklist:
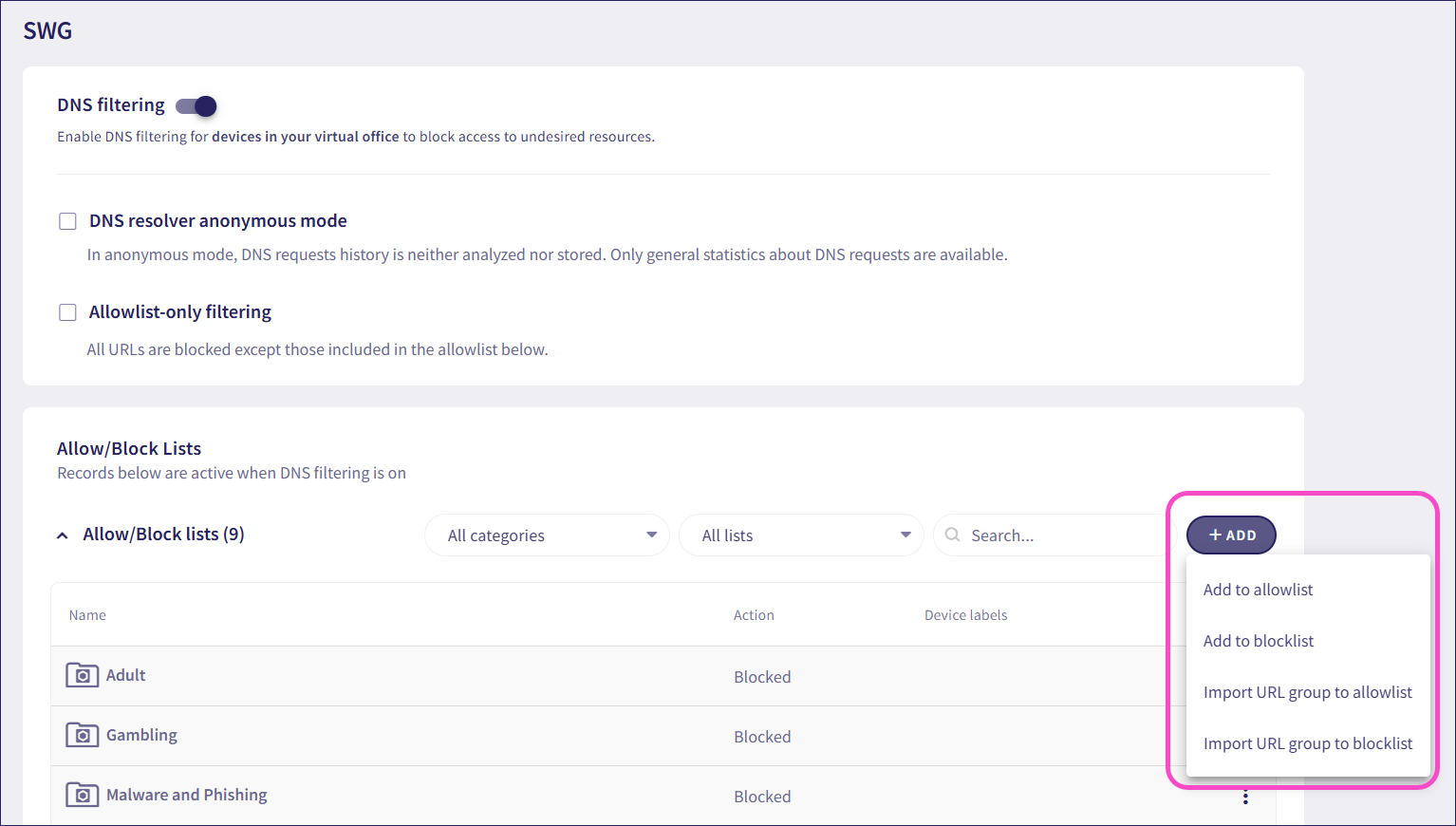
Coro displays the Add to allowlist/blocklist dialog:

Enter URLs, IP address ranges, subnets, or URL-based wildcards.
Select the device labels to which the list should apply.
Select ADD TO LIST.
To add a list of URLs, IP address ranges, subnets, or URL-based wildcards to an allowlist or blocklist:
Select + ADD > Import URL group to allowlist/blocklist:

Coro displays the Import URL group to allowlist/blocklist dialog:
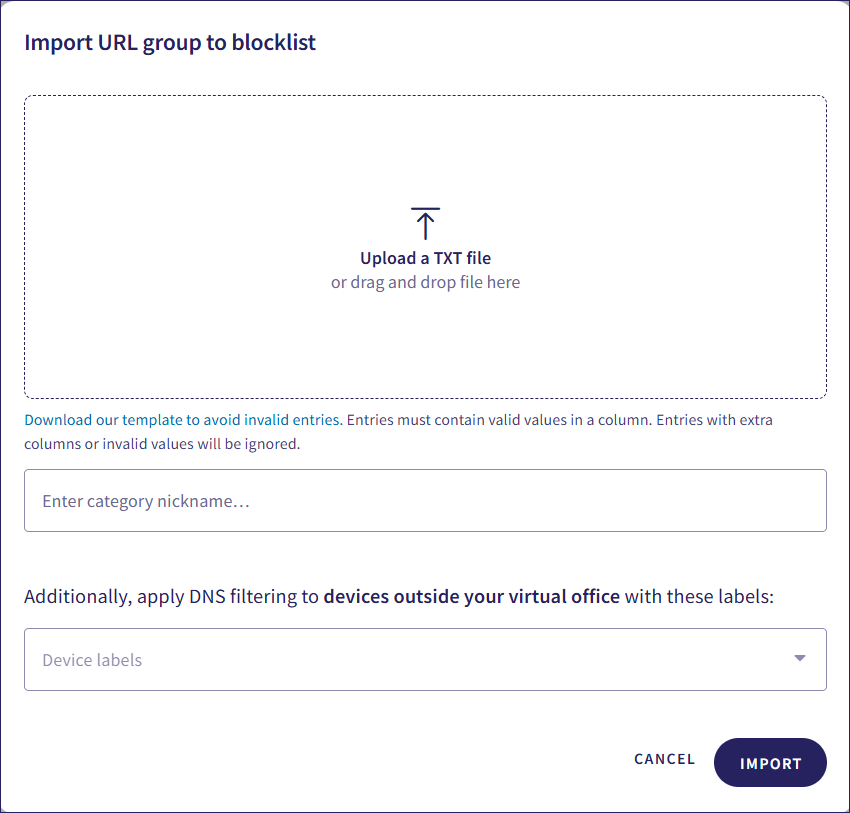
Upload a text file of the URLs, IP address ranges, subnets, or URL-based wildcards. To facilitate creating a valid text file, Coro provides a link to a template in the Import URL to allowlist/blocklist dialog. Each entry should be on a separate line:
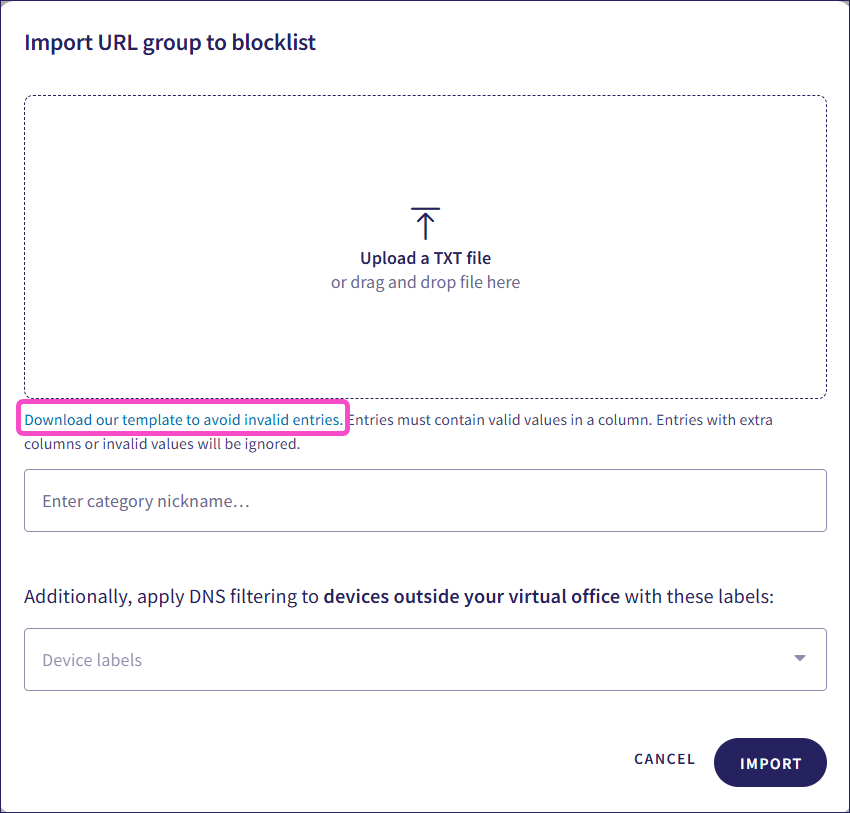
Enter a name for the URL group.
Select the device labels to which the list should apply.
Select IMPORT.
View, edit, remove, disable, or enable allowlists and blocklists from the three-dot menu next to each list. Disabled lists appear grayed out: