The tickets discussed in this article apply to devices running Windows or macOS Agents.
When an admin user configures sensitive data settings for an endpoint device, Coro flags detection of sensitive data by creating an Endpoint Drive Containing Sensitive Data ticket.
Coro creates this ticket when it detects one or more of the monitored data types on an endpoint device drive. The raised ticket contains details of all occurrences of monitored sensitive data detected during the event, enabling admin users to review detection of all data types for a single event in one place.
These data types are:
- Credit Card Data
- Health Data
- Non-Public Data
- Personal Data
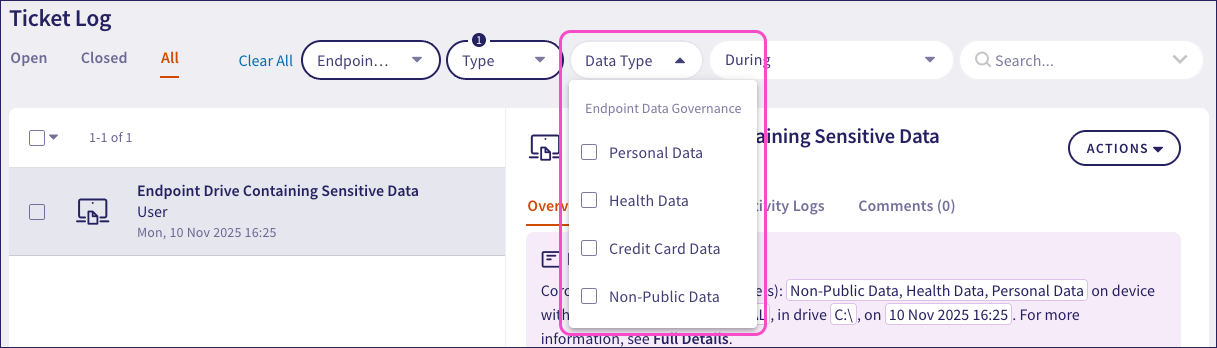
Use the Module and Type filters in the Ticket Log to find endpoint data governance tickets. To filter results by specific sensitive data types, Coro provides an additional Data Type filter:
Coro deprecated the following ticket types in version 3.7:
- Endpoint drive with Credit Card Data
- Endpoint drive with Health Data
- Endpoint drive with Non-Public Data
- Endpoint drive with Personal Data
Coro now consolidates all exposure violations for these data types for a single event into one Endpoint Drive Containing Sensitive Data ticket.
To enable admin users to view historic tickets raised for deprecated types, Coro shows both deprecated and current ticket types in the left pane of the Ticket Log when you use the Type filter.
To learn more about what information constitutes these sensitive data types, see Regulatory sensitive information types.
Data compliance officers might need to review privacy-sensitive tickets to meet regulatory standards, such as GDPR and HIPAA. Tickets remain open for review by an admin user until Coro closes them automatically after 10 days.
Privacy-sensitive data tickets include the following actions:
| Action | Outcomes |
|---|---|
| Close ticket | Close this ticket as considered remediated and take no further action. Note: When a device is removed from protection, all open tickets associated with the device are automatically closed. |
| Encrypt drive | Encrypts the hard drive of the device. A record is added to the Activity Log: "Drive encryption was requested on <device name> of user <user> (drive: '<drive >')" When drive encryption is complete, a further record is added to the Activity Log: "Drive was encrypted on <device name> by <user>" Encryption keys are stored on both the device (by BitLocker) and on Coro's secure servers. |
For further information on how Coro protects an organization's device data, see Introducing Endpoint Data Governance.
For further information on data governance ticket management, see Ticket management.
Coro generates either an open or closed Endpoint drive containing sensitive data ticket based on the type and combination of detected sensitive data, as outlined below:
Coro generates a closed Endpoint drive containing sensitive data ticket when it detects personal data and another sensitive data type, such as financial keywords (financial metadata, content, forms, or credit card data).
Coro generates an open Endpoint drive containing sensitive data ticket when it detects credit card data.
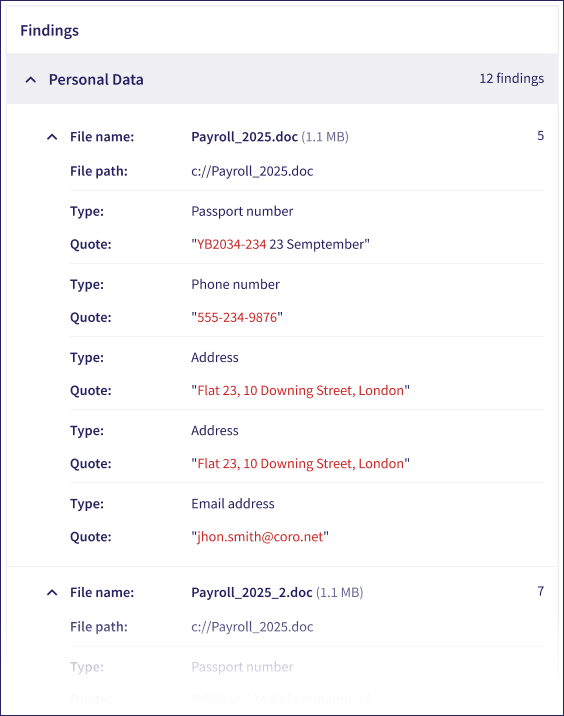
Each ticket contains a Findings table in the Full Details tab showing scan results grouped by sensitive data type:
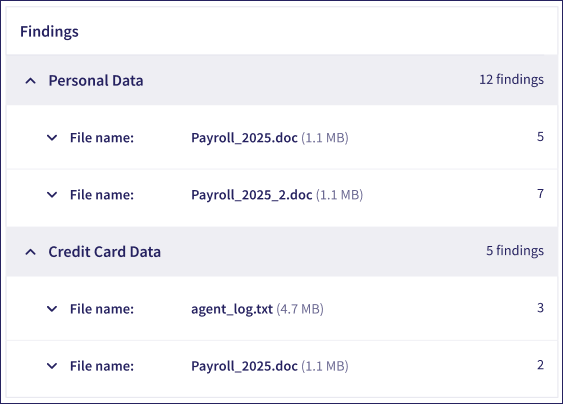
File name: The filename and file extension of the file that caused a policy violation
# of findings: The number of policy violation detected in the file
Expand the File name item to display additional information:
File path: The file path.
File size: The file size, in KB.
Coro lists each detected data item in the file as a Type and Quote pair:
Type: The type of sensitive data, for example, credit card number.
Quote: The text string in quotes containing the sensitive data, for example, "of PCI that can lead to identifying an individual . 6945 CVV 123 Test".