v3.0¶
Version 3.0, a major release including several major changes, includes:
Prerequisites¶
Before you can use the features and enhancements described below, you must update the relevant agent on your device. macOS/Windows agents 3.0 will be available on October 29, 2023.
New features¶
This section describes the new 3.0 modular security Coro platform that we are releasing with version 3.0.
Modular overview¶
The new 3.0 modular security Coro platform enables mixing and matching modules that snap easily into our platform and always work together, communicating via the same AI engine, regardless of how many of those components are implemented. This modular security Coro platform allows you to:
-
Pick and choose the security components (modules and associated add-ons) you need
-
Ensure compliance with the regulations you're obligated to
The following video provides an overview of the modular security Coro platform:
The following table summarizes the changes made to the location of specific settings in the Coro 3.0 modular security platform.
| 3.0 Module | 3.0 Setting name | 3.0 Location |
|---|---|---|
| Endpoint Security | Advanced Threat Control | Control Panel > Endpoint Security > NGAV |
| Secured Shadow Backups | Control Panel > Endpoint Security > NGAV | |
| Enhanced EDR Block Mode | Control Panel > Endpoint Security > NGAV | |
| Enable an initial malware and ransomware scan | Control Panel > Endpoint Security > NGAV | |
| Wi-Fi Phishing Add-on | Control Panel > Endpoint Security > Add-ons | |
| Labels | Control Panel > Endpoint Security > Labels | |
| Agent Deployment | Control Panel > Endpoint Security > Agent Deployment | |
| Device Posture | Control Panel > Endpoint Security > Device Posture | |
| Cloud Security | Access Permissions | Control Panel > Cloud Security > Access Permissions |
| Email Security | Settings | Control Panel > Email Security > Settings |
| Allow/Block | Control Panel > Email Security > Allow/Block | |
| Add-Ins | Control Panel > Email Security > Add-Ins | |
| Secure Messages Add-on (New) | Control Panel > Email Security > Secure Messages | |
| User Data Governance | Monitoring | Control Panel > User Data Governance > Monitoring |
| Permissions | Control Panel > User Data Governance > Permissions | |
| Exclusions | Control Panel > User Data Governance > Exclusions | |
| Endpoint Data Governance | Monitoring | Control Panel > Endpoint Data Governance > Monitoring |
| EDR (New) | Processes | Control Pane > EDR > Processes |
| Telemetry | Control Pane > EDR > Telemetry | |
| Allow/Block | Control Pane > EDR > Allow/Block | |
| Control Panel | Activity Logs | Toolbar > Activity Logs |
| Visibility Mode (New) | Control Panel > Devices > Settings > Visibility Mode | |
| Connect Cloud Applications | Control Panel > Cloud Applications |
Modules¶
A module is an independent cybersecurity feature, for example, security for email.
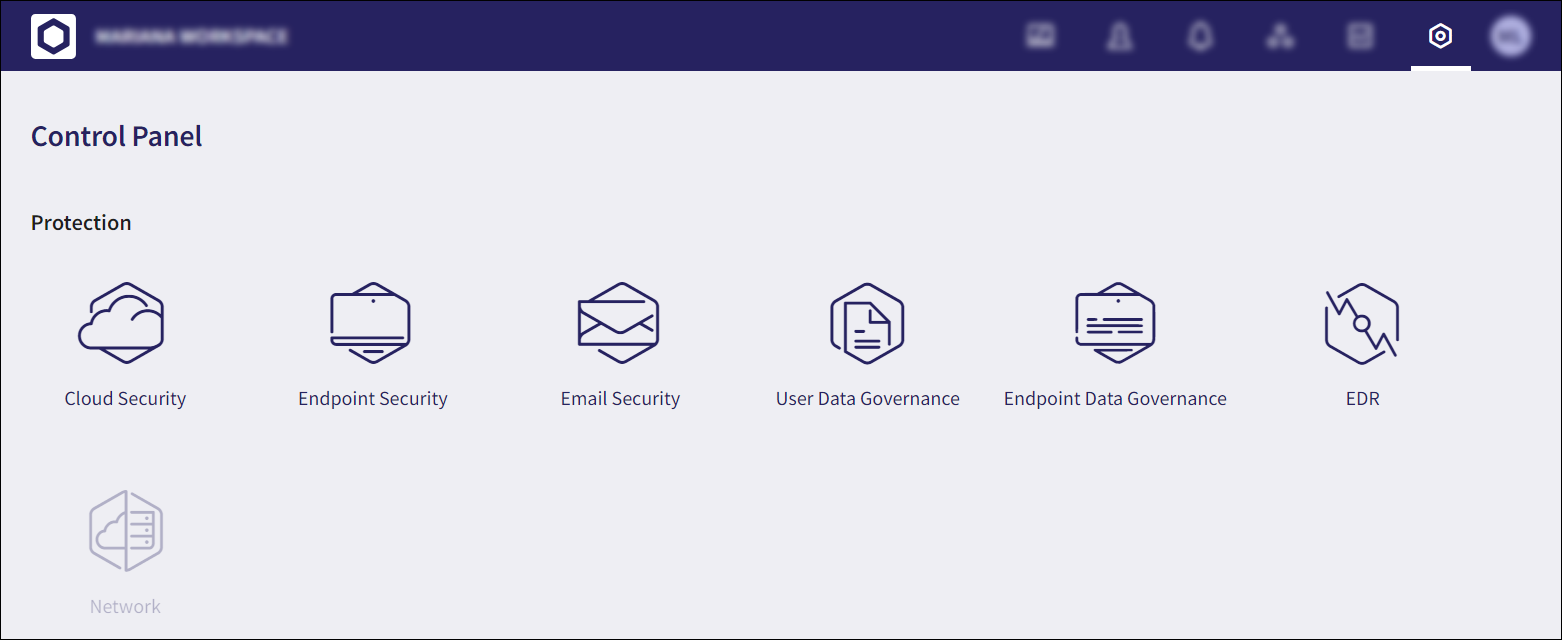
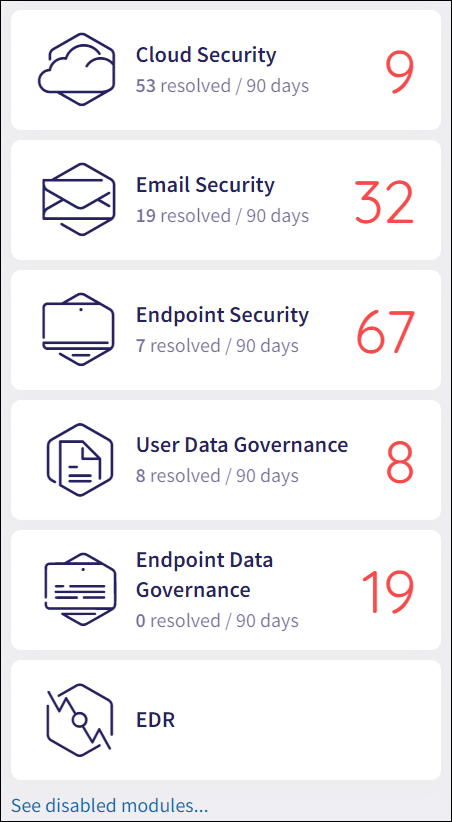
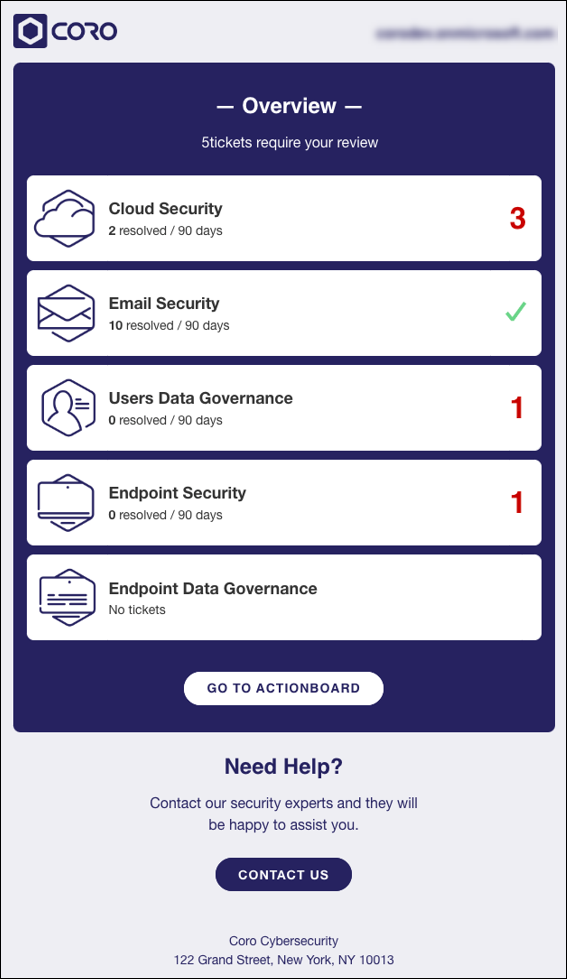
Version 3.0 includes six modules, one of which offers entirely new functionality. The Control Panel lists all modules under the Protection area, with unactivated modules greyed out. The following list details the module names, as well as their previous Control Panel section name (where applicable.)
-
Endpoint Detection and Response (EDR) - New module.
-
Endpoint Security - Previously Devices (Device Posture).
-
User Data Governance - Previously a sub-component of Data.
-
Endpoint Data Governance - Previously a sub-component of Data.
-
Email Security - Previously Email.
-
Cloud Security - Previously Cloud Apps.
Activated modules are all available from the Actionboard via their widgets:
Add-ons¶
Add-ons are optional components that can be included in a subscription. Add-ons are not required to access a module's full functionality, but they are dependent on the module for which they are an add-on.
Version 3.0 includes several add-ons that provide enhanced security to specific modules. The following add-ons are available:
-
Secure Messages: Part of Email Security
-
Wi-Fi Phishing: Part of Endpoint Security
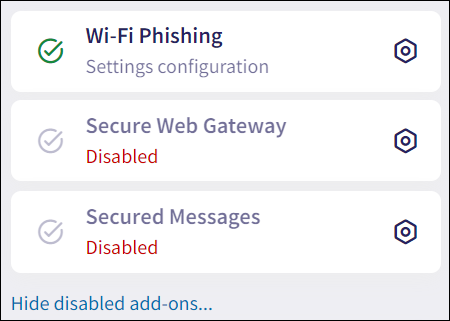
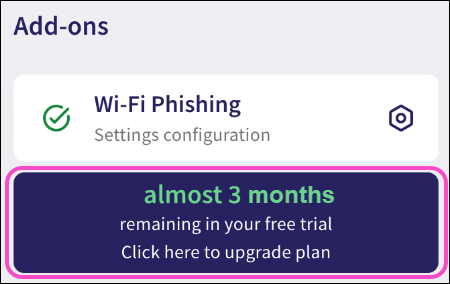
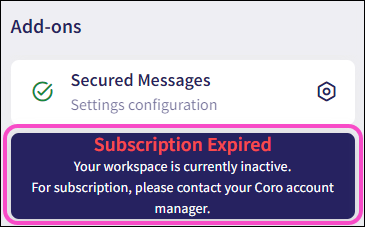
Activated add-ons are also available from the Actionboard via add-on panels:
This section describes the modules, add-ons, and workspace management/integration functionality that we are releasing with version 3.0.
1 - EDR¶
The Endpoint Detection and Response (EDR) module focuses on detecting and responding to advanced threats targeting endpoints (Windows, Windows Server, and macOS). Coro EDR continuously collects telemetry data from endpoints to monitor for suspicious activities, malicious behaviors, or signs of compromise. The EDR Allow/Block list allows you to block processes that are deemed unsafe.
The EDR module includes the following components:
-
Telemetry page
-
Processes page
-
Allow/Block list (Supports process blocking)
For further information, see Coro Endpoint Detection and Response (EDR).
2 - Endpoint Security¶
The Endpoint Security module is a robust solution that utilizes the Coro Agent to automatically recognize any endpoint devices that have the Coro Agent installed on them.
For further information, see Introducing Endpoint Security.
2.1 - Endpoint Security Allow/Block list¶
As part of the Endpoint Security module, the Allow/Block tab allows you to fully manage your own known files and folders by allowing those that are safe. Additionally, you can block processes that are deemed unsafe.
For further information, see Allow/Block files, folders, and processes.
2.2 - Windows device USB Lockdown¶
USB drives for a Windows device can now be blocked. Locking of USB devices is controlled via a Windows device policy. The USB Lockdown device policy allows you to:
-
Block portable devices - USB connected mobile phone
-
Block mass storage devices - USB flash drive or USB hard drive
For further information, see USB lockdown.
2.3 - Wi-Fi Phishing add-on¶
The Wi-Fi Phishing add-on integrates with the Endpoint Security module to extend endpoint security posture by detecting connections to Wi-Fi access points that are suspicious of man-in-the-middle attacks aimed at hijacking device communication.
Note
The Wi-Fi Phishing add-on is included in the Email Security module as standard. The functionality previously existed under Endpoint Devices settings.
For further information, see Wi-Fi phishing.
3 - User Data Governance¶
The User Data Governance module aims to establish an all-encompassing and proactive strategy for correct and secure data handling by a business's end users.
For further information, see Introducing User Data Governance.
4 - Endpoint Data Governance¶
The Endpoint Data Governance module aims to help administrators establish a strategy for correct and secure handling of data assets by authorized users.
For further information, see Introducing Endpoint Data Governance.
5 - Email Security¶
The Email Security module detects and remediates fraudulent email message aimed at deceiving the user into disclosing sensitive information or downloading malware.
For further information, see Introducing Email Security.
5.1 - Secure Messages add-on¶
The Secure Messages add-on integrates with the Email Security module to provide sender-to-recipient (outbound) email encryption service offering a secure digital messaging system based on an advanced two part encryption mechanism that initiates as soon as a message is sent.
For further information, see Secure Messages.
6 - Cloud Security¶
Coro's Cloud Security module is a CASB (Cloud Access Security Broker) based solution, providing advanced malware and ransomware detection and remediation for connected users and their cloud drives.
For further information, see Introducing cloud security.
7 - Workspace integrations¶
Security Information and Event Management (SIEM) is a technology that provides real-time monitoring, analysis, and correlation of security events and logs from various sources within an organization's network.
For further information, Security Information and Event Management (SIEM) integration.
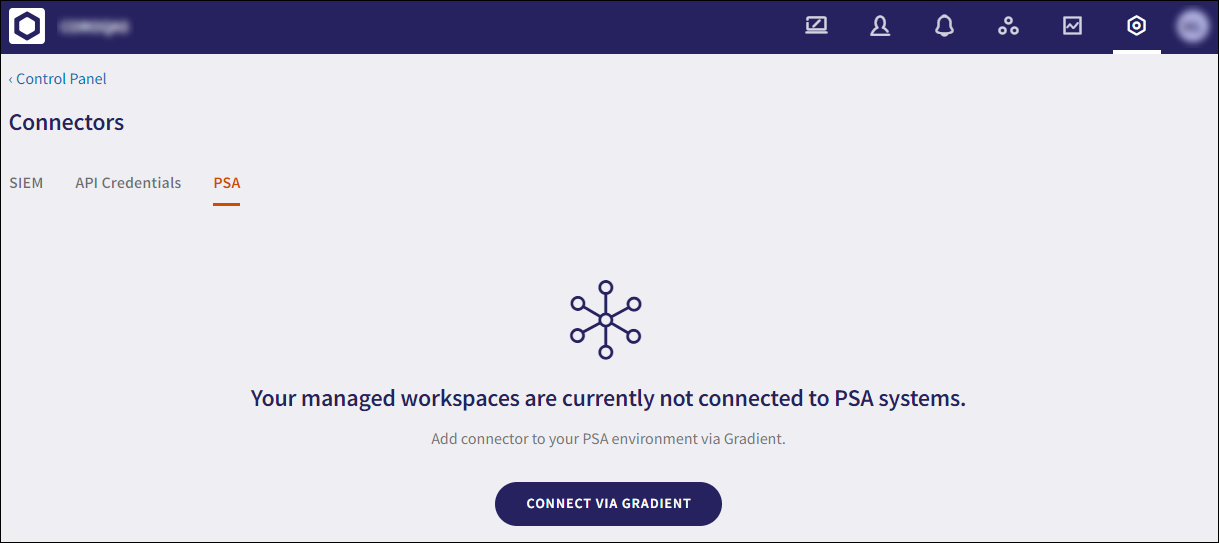
7.1 - Integration of Coro with Gradient to support channel PSAs¶
Coro can now report usage data from multiple Coro managed workspaces by integrating with Gradient MSP as middleware to connect to multiple Professional Services Automation (PSA) systems using a PSA connector. Gradient MSP is used to map services (Coro modules and add-ons) and accounts (managed workspaces) to PSA systems in order to report workspace usage data.
For further information, Gradient MSP integration.
Enhancements¶
1 - Interface updates and enhancements¶
Version 3.0 introduces the following additional changes to the Console. These modifications are intended to accommodate the new modular structure, with all future developments planned accordingly.
1.1- Additional Toolbar options¶
-
Devices and Users options added to the Toolbar in order to view the respective information independently of which modules are enabled:
-
New options for the Users, Devices, and Cloud Applications sections on the Control Panel:
1.2- Updated email notification¶
1.3- Notification banner moved¶
1.4 - Control Panel layout updates¶
-
The following Control Panel sections are now available from the Workspace area:
-
Users
-
Devices
-
Activity Logs (Previously located on the Toolbar)
-
For further information on Console and ticket modifications, see Control Panel, Using the ticket log, and The Actionboard.
2 - Tickets and ticket logic¶
The following enhancements have been made to tickets and ticket logic:
2.1 - Ticket updates¶
-
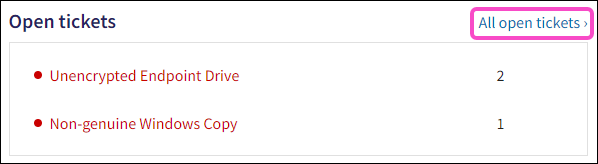
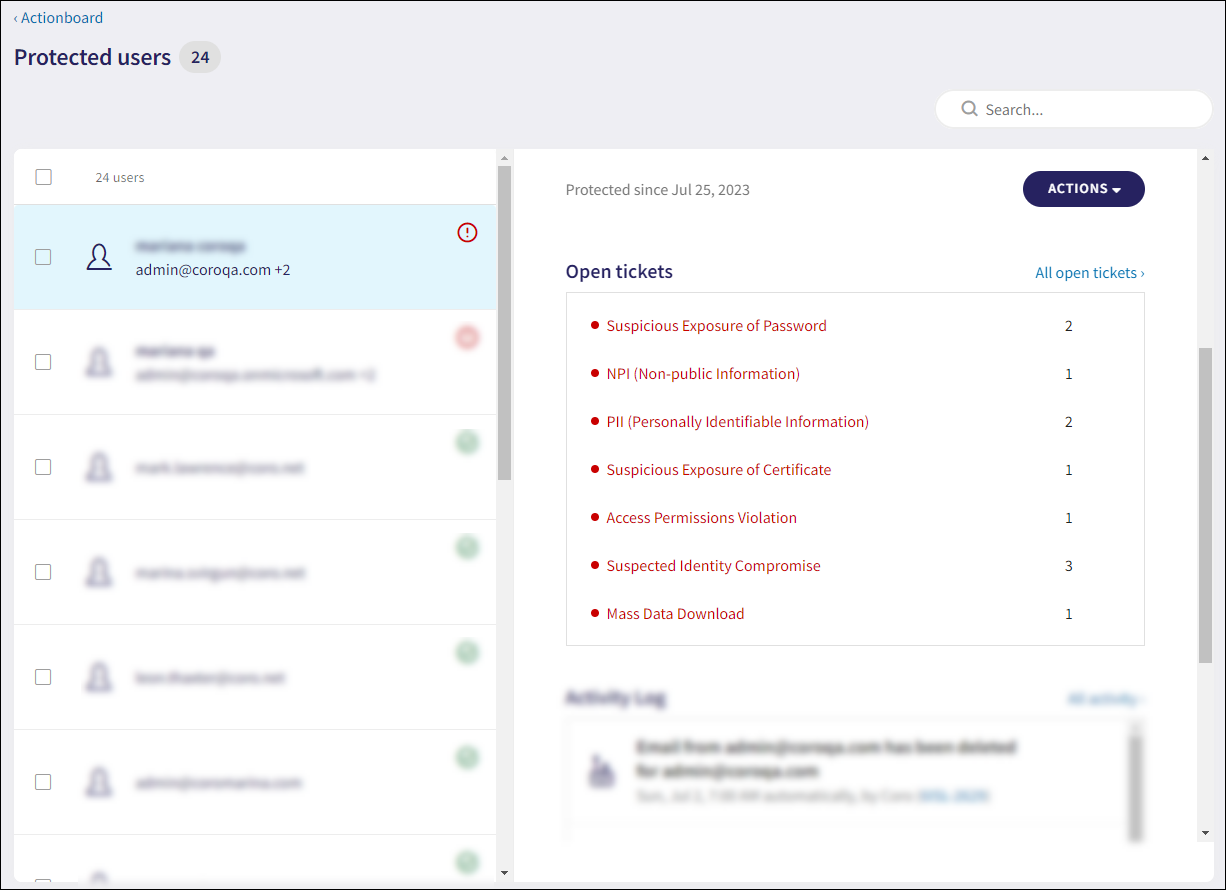
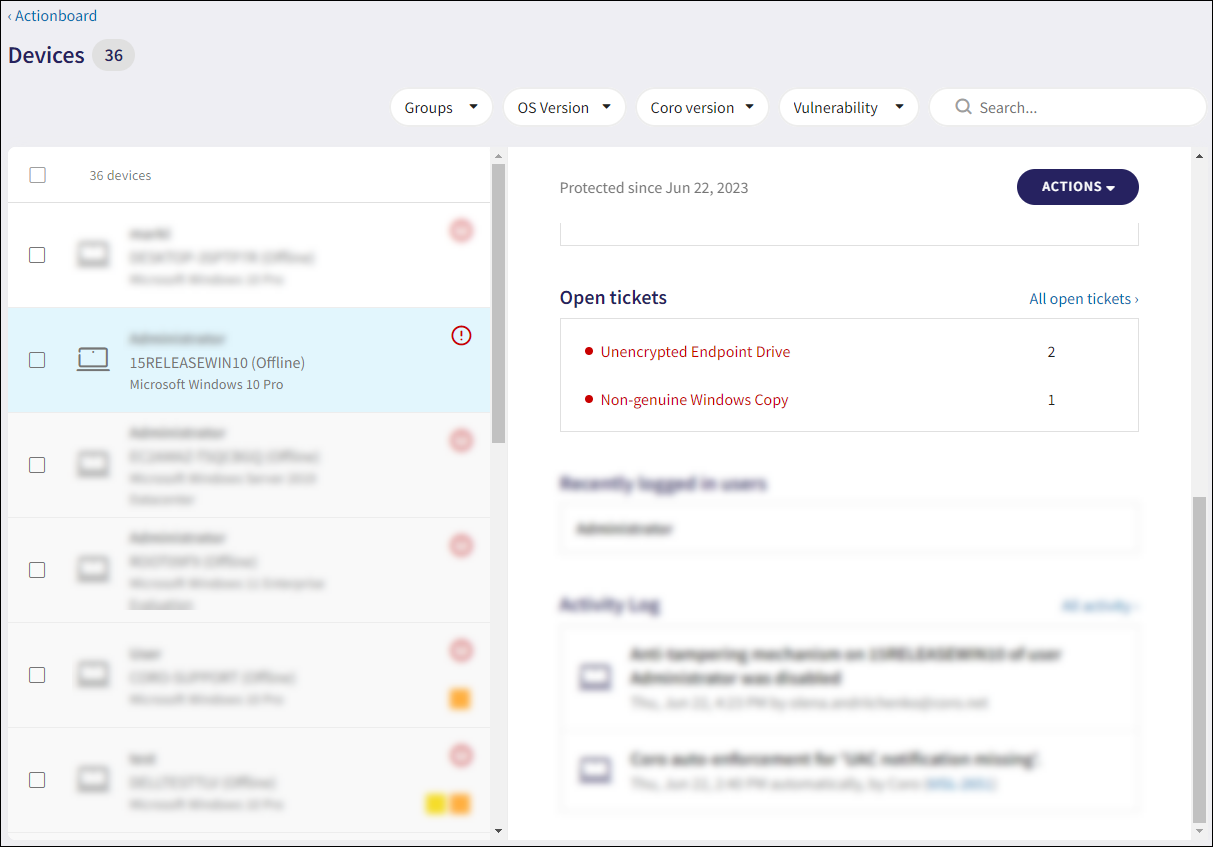
Updated All open tickets link query on the Protected users and Devices page to filter corresponding tickets on the Ticket Log as follows:
-
Protected users: Displays for all open Cloud security and User data governance tickets
-
Devices: Displays for all open Endpoint security and Endpoint data governance tickets
-
-
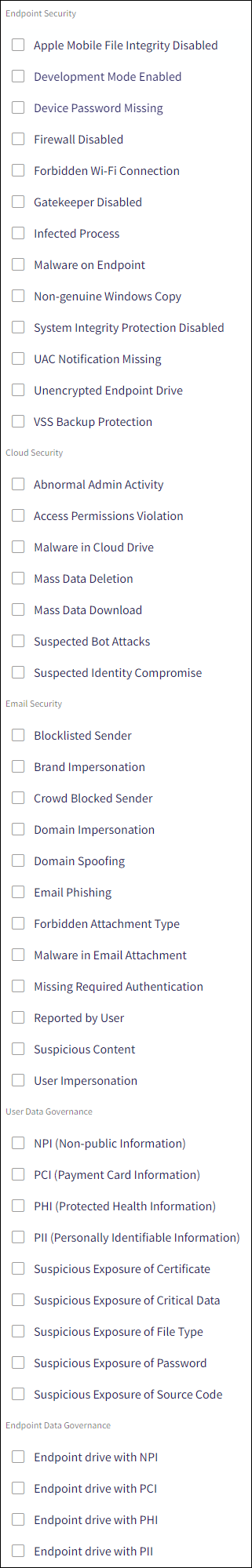
Updated the Type filter in the Ticket log to group tickets according to their respective modules:
-
Tickets are now classified by the following types:
-
Endpoint Security
-
Cloud Security
-
Email Security
-
User Data Governance
-
Endpoint Data Governance
-
-
Updated Open tickets section for Protected users page. The following tickets are displayed:
-
Malware in Cloud Drive
-
Suspected Identity Compromise
-
Access Permissions Violation
-
Abnormal Admin Activity
-
Mass Data Deletion
-
Mass Data Download
-
Suspicious exposure of password
-
Suspicious exposure of certificate
-
Suspicious exposure of source code
-
Suspected Bot Attacks
-
PII
-
PCI
-
PHI
-
NPI
-
-
Updated Open tickets section for Devices page. The following tickets are displayed:
-
Endpoint Drive with NPI
-
Endpoint Drive with PCI
-
Endpoint Drive with PHI
-
Endpoint Drive with PII
-
All Endpoint Security tickets
-
2.2 - Major Refactoring of Email Security tickets¶
We have overhauled Email Security tickets. Now one ticket is generated per email/domain. Each ticket includes an additional subset of detection information. This assists Admin users to have greater insight into:
-
Email Security threat types detected
-
Email Security threat types Coro identifies
The Allow/Block lists for Email Security threats is now divided into two sections, with each section supporting multiple ticket types:
-
Suspicious content
-
Authentication failure
For further information, see Email Security.
2.3 - Additional ticket data returned by the Coro REST API¶
The Coro REST API now returns the following ticket data for all ticket types:
-
Create Date
-
Ticket ID
-
Ticket Type
-
Status
-
Workspace ID
-
Parent Workspace ID
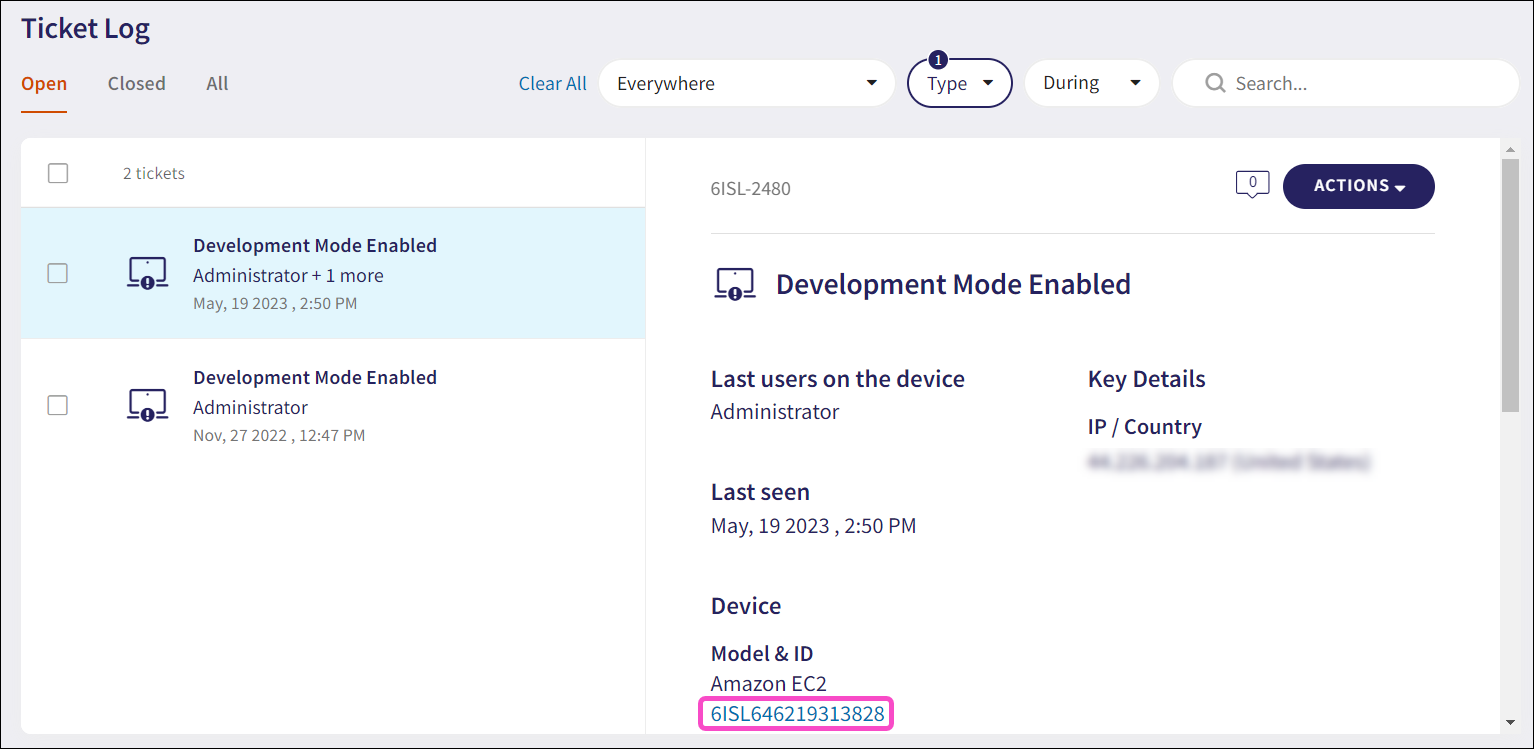
2.4 - Navigate to affected devices directly from the Ticket Log¶
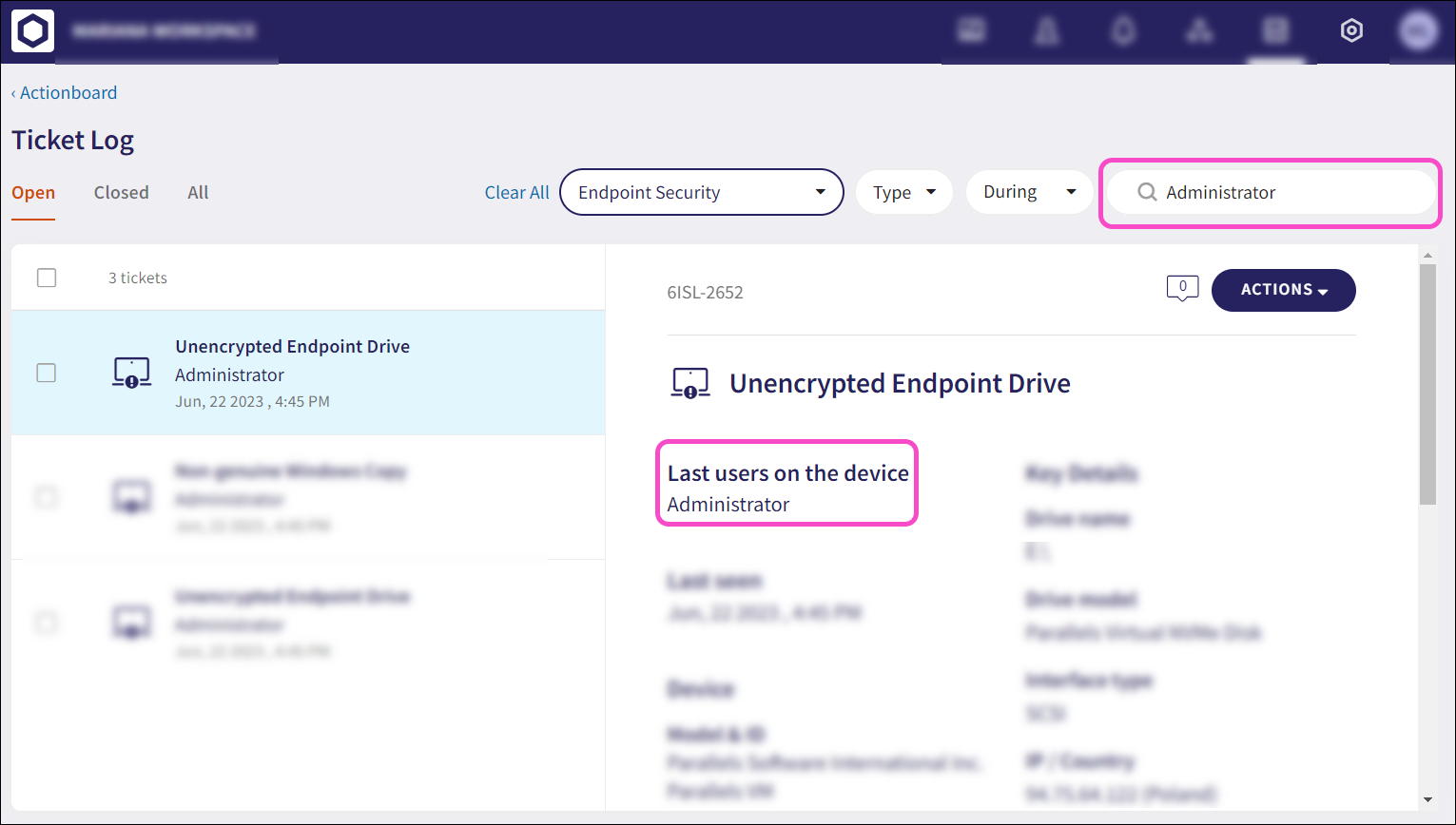
You can now navigate directly to the Devices page from Endpoint Security and Endpoint Data Governance tickets in the Ticket Log by selecting the device ID listed under Model & ID:
2.5 - Search by Last users on the device for device tickets¶
You can now search for Endpoint Security and Endpoint Data Governance tickets by the user listed under Last users on the device:
2.6 - Updated available actions for Malware in email attachment tickets¶
We have updated the available actions for Malware in email attachment tickets.
The following actions have been added:
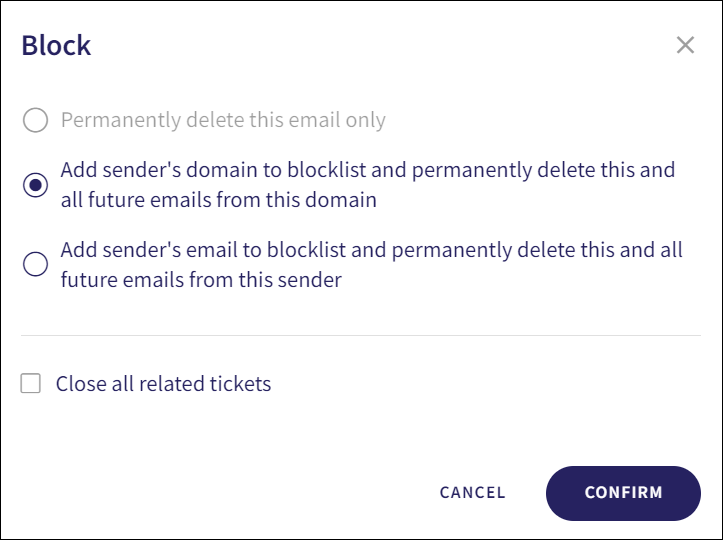
The following actions have been removed:
-
Approve this email - Deleted emails cannot be restored
-
Delete this email - This is included as part of the available actions when Block is selected
-
Add sender to blocklist - This is included as part of the available actions when Block is selected
-
Add sender's domain to blocklist - This is included as part of the available actions when Block is selected
For further information, see Ticket types for Email Security
3 - Add groups containing unprotected users to User Data Governance Permissions¶
You can now add groups that contain unprotected users to User Data Governance permissions
Warning
Unprotected users in groups that are added to User Data Governance permissions are not added to protection.
For further information, see Setting access permissions.
Fixed items¶
-
Fixed an issue where long keywords entered on the User Data Governance page created an infinite length chip. Keywords are now comma separated, with a separate chip created for each value. The length of chips containing long keywords without a comma has been restricted.
-
Fixed issues where:
-
Forbidden Wi-Fi Connection was not displaying in the Type filter on the ticket log.
-
Open and Resolved tickets were not displaying correctly in the Endpoint Data Governance section.
-
Agent updates¶
This section describes the following additional agent updates that we are releasing with version 3.0:
Prerequisites¶
The relevant agent must be updated on your device before changes take effect. The features described will not function until the updated macOS and Windows agents are installed. These are available on 29 October 2023.
1 - macOS agent 3.0¶
macOS agent 3.0 releases 29 October 2023, and includes the following:
1.1 - Device isolation from network support¶
For further information, see EDR process actions.
1.2 - Allowlist/Blocklist support for processes/folders/files¶
For further information, see EDR Allow/Block lists.
1.3 - Additional Device Posture policies¶
Three additional macOS Device Posture policies are now available:
-
Gatekeeper Disabled
-
Apple Mobile File Integrity Disabled
-
System Integrity Protection Disabled
Warning
macOS agent 3.0 must be installed in order for these policies to function.
For further information, Device posture.
1.5 - Bug fixes¶
General bug fixes were made for this release.
2 - Windows agent 3.0¶
Windows agent 3.0 releases 29 October 2023, and includes the following:
2.1 - Endpoint agent Visibility mode¶
Endpoints agents are now able to function in Visibility mode. In Visibility mode, the Coro Agent generates events and sends notifications to end users, but no automatic remediation (such as quarantine or process kill) is performed.
For further information, Protection settings.
2.2 - USB Lockdown support¶
For further information, see Windows device USB Lockdown.
2.3 - Device isolation from network support¶
For further information, see EDR Process actions.
2.4 - Allowlist/Blocklist support for processes/folders/files¶
For further information, see EDR allowlisting/blocklisting process, folders, and files.
2.5 - Bug fixes¶
- General bug fixes were made for this release.