Endpoint Security¶
What level of Windows User Account Control (UAC) must be enabled for Coro to enforce a UAC Notification Missing policy?¶
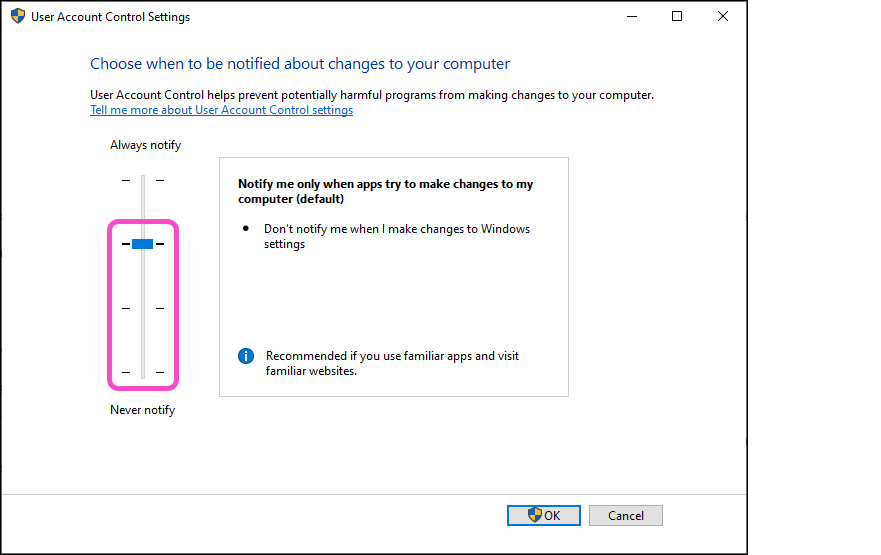
Coro enforces the UAC Notification Missing policy when Windows User Account Control settings are set to:
-
Default
-
Low
-
Medium
Warning
Windows UAC is considered vulnerable when set to Low or Medium.
For more information, see UAC Notification.
If an admin user configures a Remote Password & Session Locking policy on my workspace, how does the Coro agent detect how old my existing password is?¶
The Coro agent is capable of extracting user profile information directly from your device to determine the age of your existing password.
For more information, see Remote password and session locking.
Does Coro have the capability to auto-enforce hard drive encryption without allowing the end user to disable it?¶
While Coro can perform hard drive encryption, there is no method to ensure this functionality is auto-enforced. It is a manual remediation action performed by an admin user in the Coro console, either from the Devices page or from the Ticket Log.
Note
Hard drive encryption can be performed on Windows endpoint devices.
For more information, see Encryption for endpoints with Windows operating systems
For specific devices, how far back does Coro log recently logged in users?¶
Coro maintains a record of the previous three logged in users.
If I am running another Antivirus (AV) product, and it detects and quarantines a potentially malicious file, will Coro still detect this already quarantined file?¶
No, if a potentially malicious file has already been quarantined by another AV product, Coro does not detect it.
Where are encryption keys stored?¶
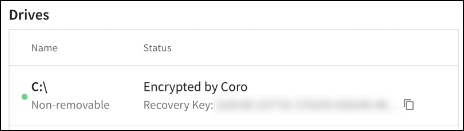
Encryption keys are stored on both the device (by Bitlocker) and on the Coro servers.
Additionally, Bitlocker recovery keys are displayed for all encrypted drives on a device. The recovery key is displayed within the Drives section of the Devices page:
For more information, see Encryption for endpoints with Windows operating systems
When an employee or contractor leaves the company, can an admin user remove the endpoint device linked to that employee, or does Tamper Protection prevent this?¶
Yes, an admin user with sufficient permissions can remove the endpoint device linked to that employee after disabling protection for the device.
Tamper Protection prevents corruption or unauthorized uninstallation of the Coro Agent on user devices. The entire workspace shares this setting. If clients want their employees to uninstall Coro independently, an admin user must disable protection for the specific device instead of the entire workspace.
To disable protection on an endpoint device:
-
Sign into the Coro console and select Devices from the toolbar:
-
Locate the desired device, and select Actions > Disable protection.
After the set Heartbeat Interval elapses, the device's protection is disabled, allowing the user to uninstall Coro.
Note
Protection on the device remains disabled until the first reboot.
For more information, see Device actions.
How do I disable Coro app notifications?¶
Although app notifications cannot be configured directly from the Coro Console, they can be configured from the device itself as follows.
Mac:
- Select Apple menu > System Settings.
- Select Notifications in the sidebar. (You may need to scroll down).
- Select the app or website on the right.
- Disable Allow notifications.
Notifications are disabled and are not received until Allow notifications is re-enabled.
Windows:
- Open Windows Settings by pressing the Win + I keys simultaneously.
- From the System page, select Notifications.
- Disable the Notifications toggle for the app.
Notifications are disabled and are not received until Allow notifications is re-enabled.
Does Coro detect Data Loss Prevention (DLP) of information within Computer aided design (CAD) files?¶
No, Coro does not detect DLP of information within CAD files.
Can Coro retroactively remediate tickets? For example, if a ticket is generated after my Coro trial expires, and therefore no remediation is performed, will Coro perform remediation on the ticket after I purchase Coro, or extend my trial period?¶
No, Coro does not perform any actions retroactively.
Under what conditions does Coro create a ticket and leave it open for an admin user to review and take action?¶
Coro employs adaptive data-driven or artificial intelligence (AI) driven decisions for detection, alerting, and remediation.
For more information, see Tickets in Coro.
Is it safe to use Coro alongside other installed antivirus (AV) products?¶
It is not advised to install Coro alongside other antivirus software, as the performance of both products will be negatively impacted. Windows Defender is, however, fully compatible with Coro.
How does Coro resolve malicious software detected on an endpoint or device?¶
Coro monitors all processes and terminates them if suspicious behavior is detected.
When Advanced Threat Control is enabled, Coro monitors active processes for known and potential threats, and blocks processes (that are not explicitly allowlisted) that exhibit suspicious behavior.
How do I add a process to the Allow/Block list?¶
The Endpoint Security and EDR module Allow/Block lists allow you to manage your processes by allowing those that are safe to be accessed.
For more information, see:
Does Coro support Linux endpoint protection?¶
Linux endpoint protection is currently not supported.
Does Coro provide protection for Chromebooks as endpoints?¶
No, Coro does not provide protection for Chromebooks.
Is Coro compatible with Spark?¶
Yes, Coro is compatible with Spark.
Can Coro detect malicious scripts embedded in Word, PDF, PPT, and other documents?¶
Yes, Coro detects malicious scripts embedded in Word, PDF, PPT, and other documents.
What gets backed up within secure shadow backup snapshots?¶
The entire hard drive of the device is backed up.
For further information, see Secured shadow backups.
Where are secure shadow backup snapshots stored?¶
Secure shadow backup snapshots are stored in the "System Volume" Information folder (hidden by default), and can be managed in the device's system protection configuration settings.
For further information, see Secured shadow backups.
How do I restore secure shadow backup snapshots?¶
For instructions on how to restore secure shadow backup snapshots, see Restoring secure shadow backup snapshots.
What does the USB Lockdown device posture policy do?¶
The USB Lockdown device posture policy blocks mass storage devices on macOS devices. For Windows devices, this extends to block both mass storage and other USB-connected devices, such as media players and smartphones.
I'm traveling outside my usual Wi-Fi network area, and when I try to connect my device to a public Wi-Fi network, the Coro Agent displays a notification: "Connection to <network> is not permitted by your administrator". What should I do?¶
Your device has a Wi-Fi connection policy enabled. Wi-Fi connection policies prevent devices from connecting to public Wi-Fi networks, only allowing connections to secure, password protected networks.
Admin users can allow the connection by ensuring no device labels that enforce this Wi-Fi connection policy are assigned to your device. Alternatively, they can remove the Wi-Fi connection policy from all devices.
Your device must first connect to a secure network to update its policy. After the policy update, your device is able to connect to public Wi-Fi networks.
Note
The time taken for the Wi-Fi connection policy to update depends on your workspace's heartbeat interval.
For more information, see Configuring Wi-Fi connectivity policies.
Does the "Approve This File" and "Exclude Folder from Malware Scan" ticket action apply only to the specific device, or does it extend to all devices within the workspace?¶
The "Approve This File" and "Exclude Folder from Malware Scan" actions extend to all devices within the workspace.