Endpoint Agent¶
Does the Coro Agent require an internet connection at all times?¶
The Coro Agent is fully autonomous and does not require connectivity for its operation. Occasional networking is needed to report findings to Coro servers, as well as to get updated on any changes to device posture policy and threats database.
How much disk space is required by the Coro Agent?¶
Approximately 1.5GB, of which over 1.2GB is devoted to the security knowledge base, which allows the client to operate autonomously.
How much memory does the Coro Agent consume?¶
The amount of memory consumed under normal conditions is approximately 400MB. During scanning, memory usage is determined by the size of the files to be scanned.
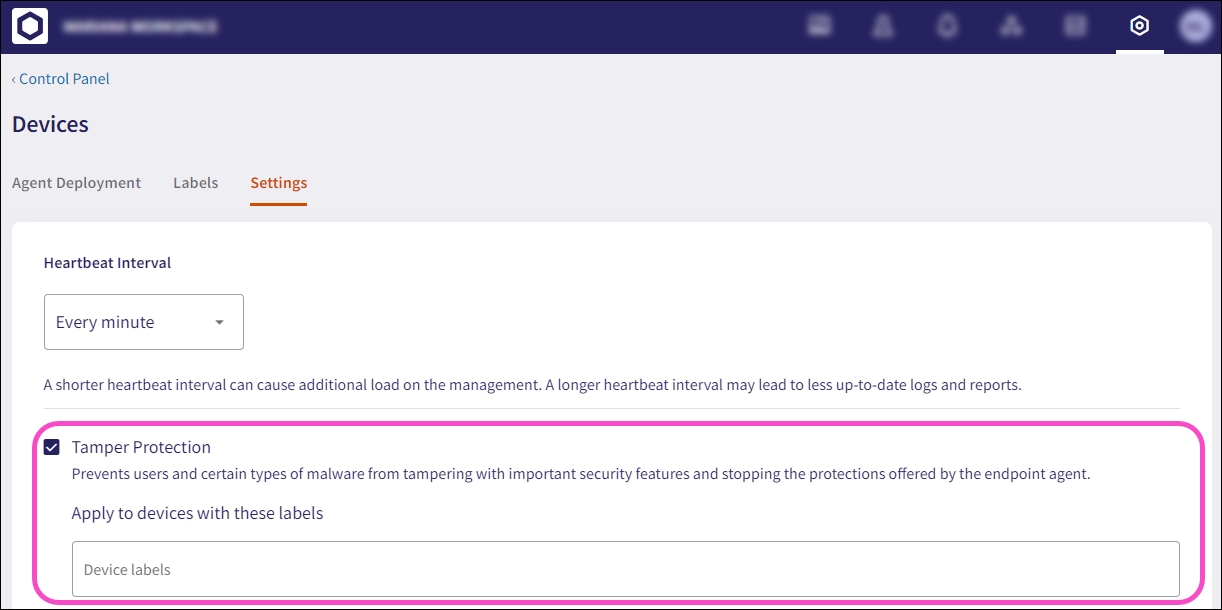
What is Tamper Protection?¶
Coro Agent Tamper Protection prevents malicious software from terminating or interfering with the Coro Agent, thereby disabling protection. Tamper Protection settings can be found in the Coro Console by navigating to Control Panel > Devices > Settings.
For more information, see Agent settings.
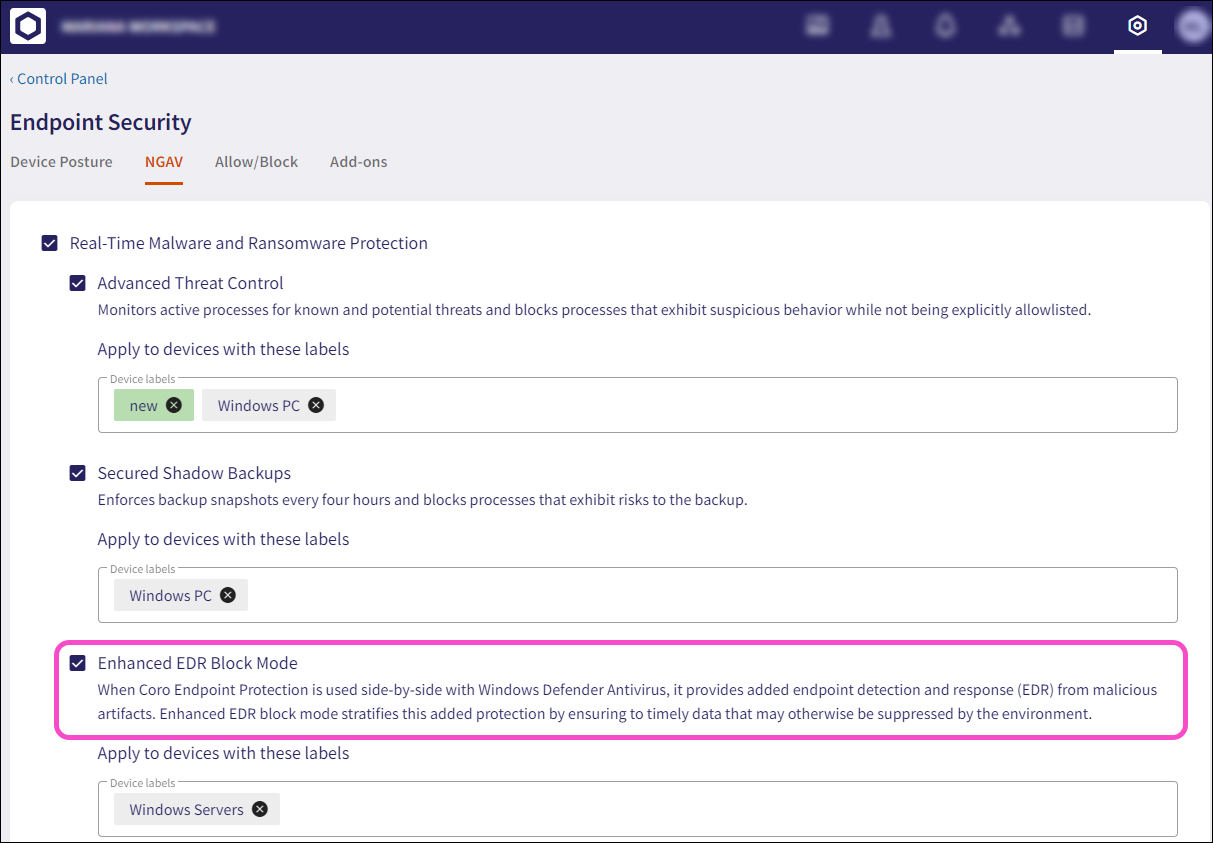
Can I run Windows Defender alongside Coro?¶
Windows Defender is not required when using Coro. If Windows Defender is running alongside Coro, Enhanced EDR Block Mode must be enabled in the console.
To enable Enhanced EDR Block Mode:
-
Select Control Panel from the toolbar:
-
Select Endpoint Security:
-
Select the NGAV tab.
-
Enable Enhanced EDR Block Mode:
Can the Coro Agent be removed from multiple users in bulk?¶
Yes, this is possible using an external mass deployment tool that can be used to uninstall the Coro Agent from all devices. Tamper Protection must be disabled on all the devices first.
For more information, see Agent settings.
What happens when you remove a user from protection? Does it also remove the Coro Agent from their devices?¶
No, when a user is removed from protection, only email and cloud apps are no longer protected. The device is not removed, and vulnerabilities are still detected, reported, and remediated. To remove the device, either disable Tamper Protection on the device so that the user can uninstall it or select Disable protection on the device from the Devices view. This prevents the endpoint client from detecting and reporting any device vulnerabilities.
As a ransomware detection and remediation tool, what advantages does Coro have over other traditional Endpoint Detection and Response (EDR) tools?¶
Unlike traditional EDRs, Coro provides extended protection, including device posture monitoring. Coro can assist in preventing such threats by ensuring users have firewalls installed, passwords set on their devices, and data encryption enabled.
A recent test of the Coro Windows Agent was conducted by SE Labs (https://selabs.uk/) and Coro received an overall score of 97%, giving it an AAA rating.
Can an endpoint device be connected to more than one workspace?¶
No, a device can only be linked to a single workspace. The installation process will fail if you attempt to install an agent from a different workspace on a device that already has Coro installed.
What is the average size of a definition/signature update received by the Coro Agent from the Bitdefender servers?¶
On average the Bitdefender engine downloads 60-70 MB a day.
Can the Coro Agent be uninstalled through the Coro Console?¶
No, currently, the Coro Agent cannot be uninstalled through the Coro Console. The user can uninstall the Coro Agent only after Tamper Protection has been disabled for the device from the console by an admin user.
For more information, see Agent settings.
When a client approves a file via the Coro Agent that's flagged as malware, does it apply to all endpoint devices?¶
The file is approved for all devices within the same workspace.
I am attempting to configure two-factor authentication (2FA), but I am not prompted to sign in with 2FA the next time I login to Coro.¶
You can only use 2FA if you log in with a username and password. Social logins (Microsoft 365 or Google Workspace) do not require the use of 2FA. The user's 2FA can be disabled in the Admin Users section of the Control Panel. 2FA can only be configured for social accounts directly from your Google or Microsoft account.
for more information, see Two-factor authentication (2FA).
How do I uninstall the Coro Agent from my device?¶
To uninstall the Coro Agent from a device, an admin user needs to first disable Tamper Protection (Control Panel > Devices > Settings) on the device. After Tamper Protection is disabled, the Coro Agent can be uninstalled from the device.
for more information, see Uninstalling the endpoint agent.
Can an admin user remotely remove the Coro Agent from a device?¶
No, the Coro Agent cannot be removed remotely. Device protection must be disabled from the console:
-
Go to Control Panel > Devices > Settings.
-
Disable Tamper Protection.
After Tamper Protection is disabled, uninstall the Coro Agent from the device.
For more information, see Agent settings.
What port number does the Coro Agent use?¶
Coro uses port 443. Non-standard ports are not supported.
What are the minimum versions of iOS and Android supported by Coro?¶
iOS 15+ and Android 9+ are the minimum versions of iOS and Android supported by Coro respectively.
What is Visibility Mode?¶
When Visibility Mode is enabled (Control Panel > Devices > Settings), the Coro Agent generates events and sends notifications to end users, but no automatic remediation (such as quarantine or process kill) is performed.
What should I do if my existing antivirus on the device is preventing the installation of Coro?¶
If you already have another antivirus running on our device, you can pause the antivirus protection for a few minutes while you install the Coro Agent.
For more information, see:
Is there a way to see when Coro Agent updates occur from the console?¶
Yes, you can see the available Coro Agent versions from the Devices section of the Control Panel.
For further information, see Agent deployment.
How does Coro manage the transition to a new version of the agent, and does this process involve any system downtime?¶
When updating to a new agent version, the old version is uninstalled and the new version is installed. There is a service interruption for a few minutes as this occurs.