Cloud app security¶
Does the Coro Security Platform offer Multi-Factor Authentication (MFA)?¶
Yes, you can enable MFA from the console. In addition, all individually supported cloud applications support MFA.
Can Coro control accessibility to Microsoft Sharepoint using IP restrictions?¶
Yes, Coro can control accessibility to Microsoft Sharepoint using Microsoft 365 Access Permissions.
For more information, see Setting Permissions for your cloud applications.
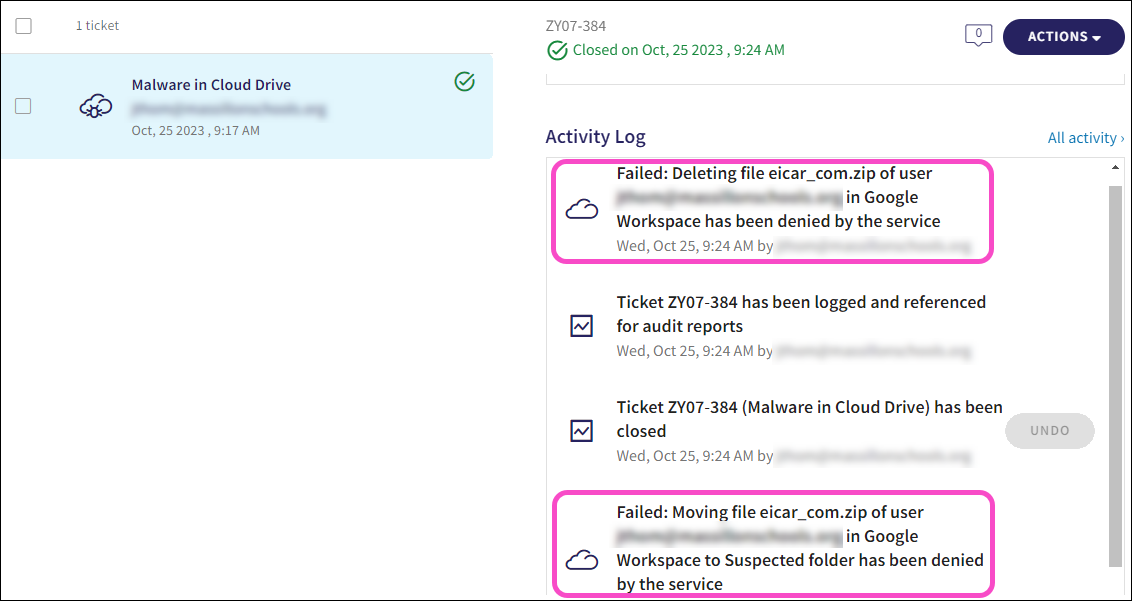
Why does the Activity Log of a Malware in Cloud Drive ticket indicate that remediation of a suspected malicious file failed?¶
A failed remediation activity within a Malware in Cloud Drive ticket indicates that the file was remediated by the native cloud application.
For more information, see Malware detection in cloud drives.
How does Coro's malware detection and execution process work?¶
Coro enhances malware detection and remediation across all monitored cloud applications, based on what each application provides natively.
To prevent possible damage, Coro moves malicious files to a quarantine folder within the cloud application and raises a Malware in Cloud Drive ticket to record the event, classified as suggested for review. Admin users can then review the ticket details in the Coro console and determine if any action is necessary.
Note
Coro does not clean infected files.
For more information, see Malware detection in cloud drives.
What monitoring and remediation functionality does Coro’s Salesforce cloud integration provide?¶
Coro provides the following monitoring and remediation functionality for Salesforce integration:
- Mass data downloads
- Mass data deletions
- Abnormal admin activity
- Suspected identity compromise
- Suspected bot attacks
- Access permissions violations
- Malware scanning
For more information, see Cloud Security tickets.
When a user is added/removed from O365/AzureAD, does the process happen in real time?¶
Yes, to synchronize all cloud application users immediately, select Synchronize users from cloud apps now from the Protected Users or Protected Groups tab on the Users page, accessible via (Control Panel > Users).
For more information, see Adding users and user groups for protection.
What is flagged as Abnormal Admin Activity?¶
Coro detects identity compromise suspicions for regular and administrative accounts by analyzing data from all customers, specific customers, and specific users behind a ticket, creating normative behavior models, and detecting anomalies from these models. The models range from simple statistical anomaly models to more complex models that cross-correlate data from various sensors throughout the system to uncover evidence of abnormal behavior.
For example, Coro can detect suspicious Admin Login due to the fact that activity took place on a user's account from different IP's in close time proximity.
For more information, see Abnormal admin activity.
Can I view audit reports from the Coro console?¶
Although you don't have the ability to generate audit reports directly from the Coro console, quarterly threat reports are provided to Coro customers.
What user behaviors does Coro monitor and track for anomalies?¶
Coro identifies anomalies such as abnormal admin activity, access permission violations, and suspected identity compromise.
For more information, see Ticket types for Cloud Security.
What protection is offered to O365 users that are not using Outlook?¶
Support is provided for all protection except email-based detections.
Does Coro provide granularity regarding which folders are being affected by a mass deletion event or malware infection?¶
Yes, Coro displays the full file path of the affected file. This applies to both local and cloud folders (1Drive, Sharepoint, Google-Drive, Dropbox etc.)
How does Coro identify Suspected Identity Compromise?¶
Coro calculates the login frequency threshold of cloud application users from various locations.
Where users log in to cloud applications from different geographic locations, Coro evaluates the login frequency across each location. Coro generates a Suspected Identity Compromise ticket when the login frequency from a particular location sits below a predetermined detection threshold.
For more information, see Suspected identity compromise.
Are file locations included in Google Workspace related tickets?¶
No, file locations are not included in Google Workspace related tickets.
What detection and remediation functionality does Box offer?¶
By default, Box does not detect malware, but it offers a paid feature, Box Shield, that detects malware in Box storage and restricts downloading and sharing.
For more information, see Box detection and remediation.
What detection and remediation functionality does Dropbox offer?¶
Dropbox does not support malware detection.
For more information, see Dropbox detection and remediation
Does Coro detect mass data downloads/deletions on Salesforce?¶
Yes, mass data downloads/deletions are detected on Salesforce. With mass data downloads, Coro detects when a large amount of smaller files are exported from Salesforce.
For more information on mass data downloads/deletions, see Cloud Security tickets.
What detection and remediation functionality does Salesforce offer?¶
Salesforce does not provide malware detection in its repositories.
For more information, see Salesforce detection and remediation.
What monitoring and protection does Coro provide for Salesforce?¶
Coro Salesforce protection includes malware/ransomware detection and remediation, as well as user account access and activity control.
For more information, see Salesforce detection and remediation.
What detection and remediation functionality does Slack offer?¶
Slack offers limited malware detection. Slack protection features include:
-
Scanning files during upload to a Slack channel and halting the upload process if Slack detects malware.
-
Performing periodic offline scans of previously uploaded files to ensure ongoing security.
For more information, see Slack detection and remediation.
What monitoring and protection does Coro provide for Slack?¶
Coro protects Slack user account access while also monitoring and controlling user activity.
For more information, see Slack detection and remediation.
What detection and remediation functionality does Microsoft 365 offer?¶
Microsoft 365 offers limited malware detection, typically occurring 15 minutes or more after a file download. If a scan identifies a file as malicious, the system restricts its sharing capabilities, and a warning appears in the OneDrive interface, indicating the file cannot be shared. In addition, there are file types that Microsoft 365 does not detect.
For more information, see Microsoft 365 detection and remediation.
What detection and remediation functionality does Google Workspace offer?¶
Google Workspace offers limited malware detection, initiating scans only during file downloads, including those downloaded through the Google Download API. If a user attempts to download a malicious file, the Google Workspace interface actively alerts them with a warning. Google Workspace does not support malware detection or remediation directly on the cloud drive.
For more information, see Google Workspace detection and remediation.
What Box subscription plan is required to connect Box to Coro?¶
An Enterprise Box subscription plan is required to connect Box to Coro.
Does Coro scan SharePoint and OneDrive for malicious executable files (EXE, MSI, etc.)?¶
Yes, Coro scans all file types for malware. The entire file's content is checked for malware/ransomware.
Can Coro alerts be delivered to a Slack channel?¶
Yes, an email rule can be created to forward emails from Coro notifications to a Slack channel.
What is the difference between a Suspected identity compromise and an Access permission violation ticket?¶
Suspected identity Compromise tickets relate to suspect log-ins and abnormal user activity. Access permission violation tickets relate to someone successfully signing in from a different country.
To set up geofencing permissions:
-
Navigate to Settings > Cloud Security > Access Permissions.
-
Select New Permissions.
-
Select All Users or Specific Groups.
The New Access Permissions dialog is displayed.
-
From the Allow access from dropdown, select Country.
-
Select the allowed countries.
-
From the Automatic remediation dropdown, select an option.
There are three remediation options when an Access Permissions policy is created:
-
None: No remediation steps are required.
-
Suspend: The user account is automatically suspended.
-
Sign in: The user must re-enter their credentials.
-
-
Select Save Permissions.
Note
If geofencing is not set up, Coro creates a Suspected identity compromise ticket.
For more information, see Setting Permissions for your cloud applications.
Can an admin user approve an Access Permission Violation ticket when automatic remediation is enforced for sign-in activities? For example, permission is granted to all users in the United States only, but a user then travels to another country and cannot log in.¶
An admin user can undo the automatic remediation activity as follows:
-
Locate the automatic remediation activity in the Activity Log inside the Access Permission Violation ticket.
-
Select UNDO.
-
Add the user to a specific group.
-
Allow country-level access permissions to the specific group (Control Panel > Cloud Security > Access Permissions)
For more information, see Setting Permissions for your cloud applications.
Is it safe for Coro to use my Microsoft 365 or Google Workspace global admin account in order to connect to Coro?¶
Yes, direct Oauth authentication is performed with the cloud app. OAuth permits Coro to use only the information that the user consents to share. OAuth also protects your passwords from being compromised.
For more information, see Sign in to the Coro Console.
Are the contents of slack messages monitored and flagged for Data Loss Prevention (DLP)?¶
No, the contents of slack messages are not monitored and flagged for DLP.
For more information, see Slack detection and remediation.
Can Coro detect when a file has been deleted from a cloud drive?¶
Yes, Coro detects mass file deletions in cloud drives, and creates a Mass Data Deletion ticket.
For more information, see Mass data deletion.
Does Coro indicate which folder was affected when a file is deleted from a cloud drive folder?¶
When larger files are deleted from cloud drives, Coro records and organizes them by folder in a Mass Data Deletion ticket.
For more information, see Mass data deletion.
Can a prospect initiate a trial if they use M365 while hosting their Active Directory (AD) in-house on a local virtual machine? For the purposes of the Coro trial, would this setup be classified as on-premises?¶
Coro integrates directly with M365. They can connect a trial, even with an AD.